Prevent Credential Exposure in Code
Reduce your organization's potential exposure by detecting and eliminating any exposed secrets before production releases.
In today’s software development world, developers rely on numerous types of secrets (credentials), to facilitate seamless interaction between application components. As modern applications become more complex and require authentication for services and dependencies, the practice of hardcoding secrets during software development is on the rise. The most common types of credentials are:
- Application Program Interface (API) keys
- Certificates
- Encryption keys
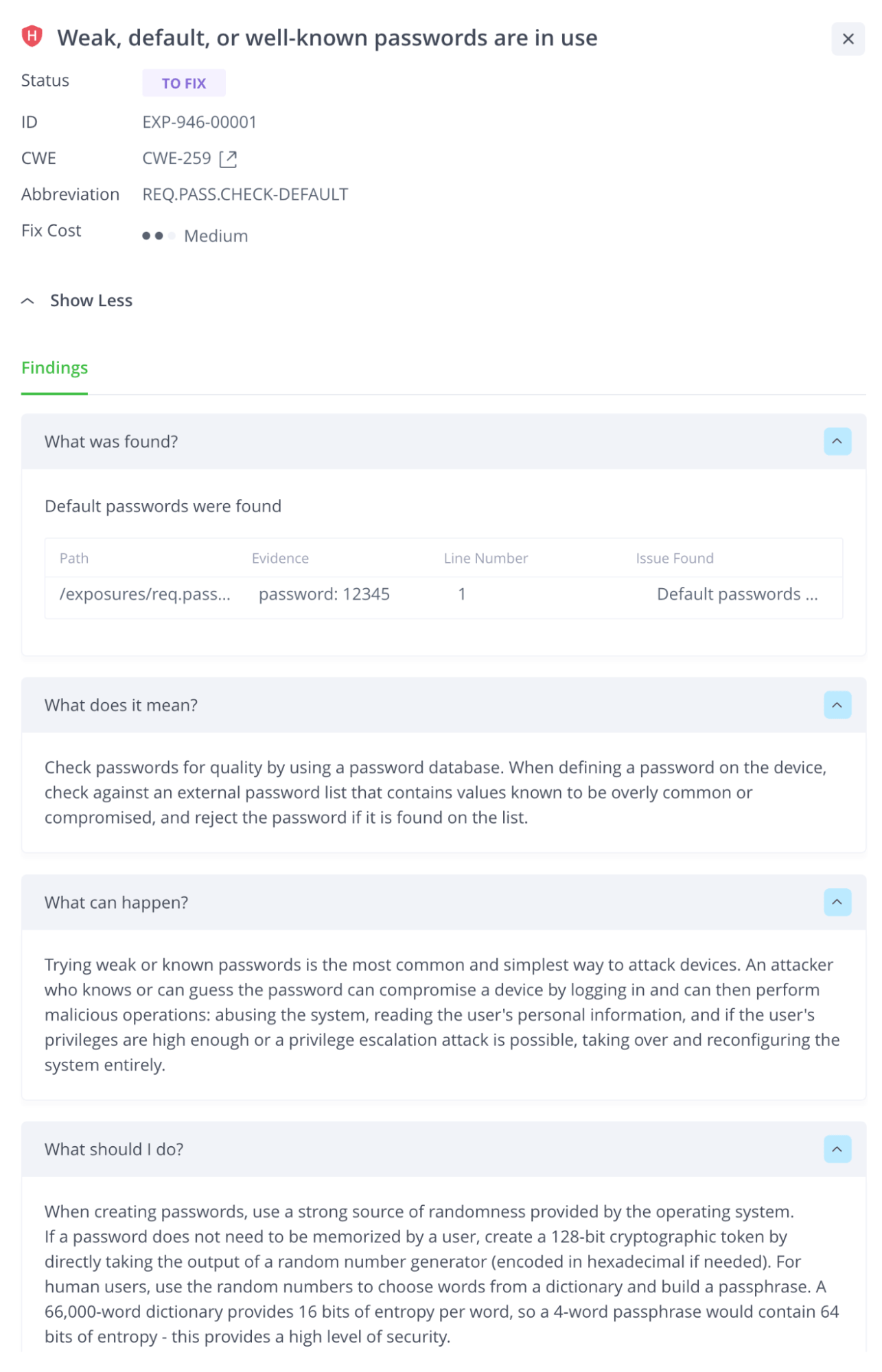
- Passwords
- Secure Shell or Secure Socket Shell (SSH) keys
Embedding secrets enables comprehensive application testing and ensures that all components are working together effortlessly. Failing to properly remove them can have disastrous consequences for businesses, making it essential to double-check that they are not present before release. In March 2022, it was reported that the average cost of a leak of a secret is $1.2 million. Poor secrets management can result in organizations losing $8.5 billion annually.
Secrets ‘Security Gaps’ Can Burn You
Applications are built using smaller modular building blocks that require passwords to connect. These credentials are essential for development and testing. However, security teams are acutely aware of the risk of “secret sprawl” that plagues companies, with secrets being scattered across various applications and systems. This can lead to a dangerous security gap, leaving businesses vulnerable to cyberattacks and data breaches. It’s critical for companies to implement robust measures to ensure that secrets are properly secured or removed to avoid potentially devastating consequences.
To Hardcode or not to Hardcode…?
The hardcoding of secrets into developers’ source code is a common practice, with passwords being included in application source code or configuration files. This approach can leave applications vulnerable to cyberattacks, giving attackers access to sensitive data, valuable networks, and critical resources. Managing these freely utilized credentials can become a daunting challenge for businesses.
One big problem is that source code is inherently fluid or leaky. Source code is frequently copied and transferred between developers, and git makes this easy to do. The proliferation of code is a monster of its own that can often lead to projects or source code getting onto public machines. Publicly exposed secrets are the worst-case scenario, but secrets embedded into applications are just as dangerous and a welcome invite for the determined attacker.
Leaked secrets are a notable security challenge often forgotten about or not considered a threat by many small or medium-sized businesses. They’re different from other types of vulnerabilities, but shouldn’t be ignored. The impact of copied or found secrets can be devastating for the life of an application and even until the secret is revoked. Because humans are involved in software development (and they always are), there is a risk of secrets exposure.
Bridge The Gaps With Secrets Detection
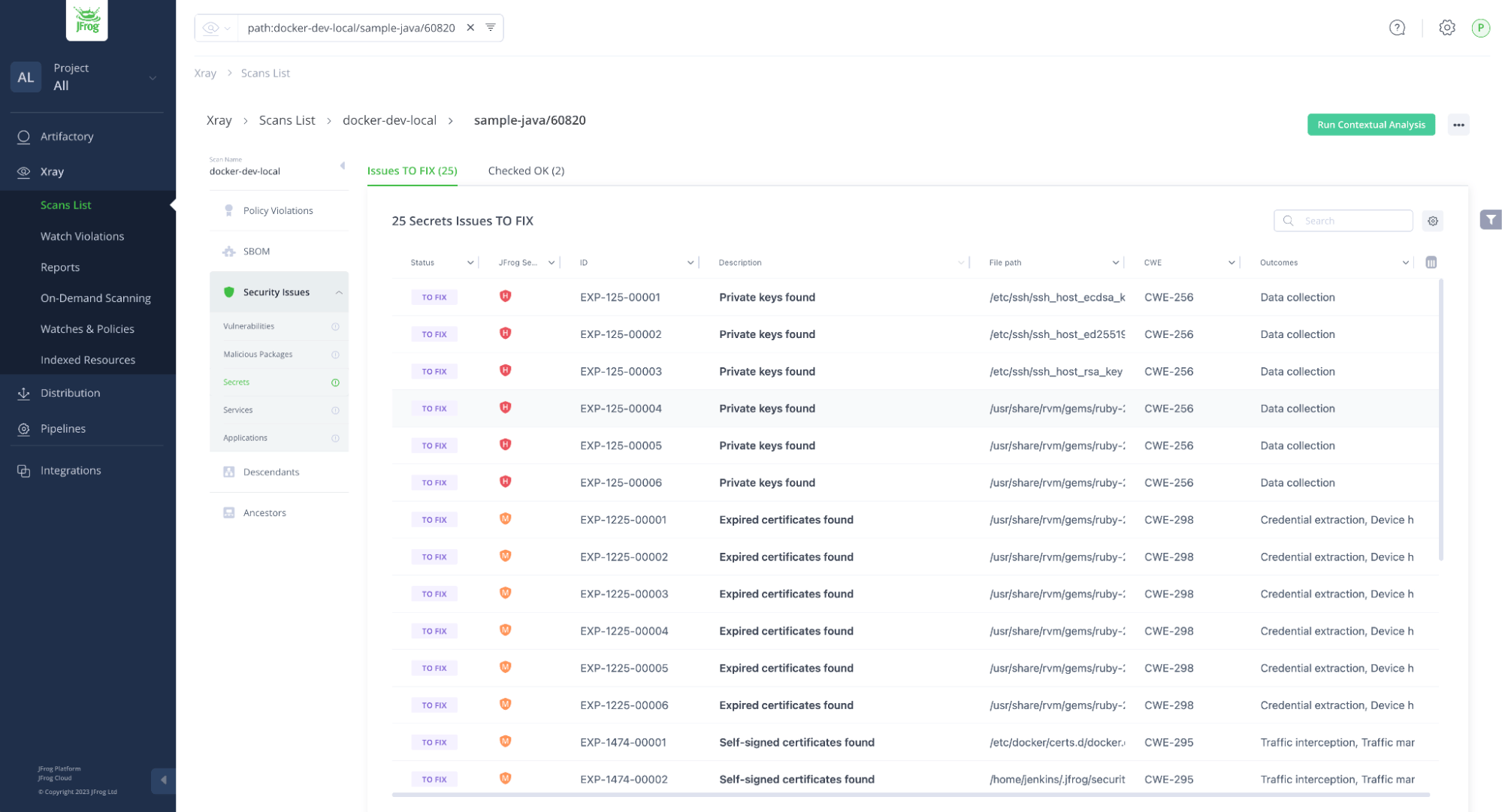
Keys and credentials are often stored in various forms, including containers and artifacts such as tokens and key files. This can lead to security risks, with some secrets even being hardcoded into binaries, a clear example of malpractice. Others may be found in configurations or text files, making it challenging for businesses to track and secure them properly.
However, with JFrog Advanced Security’s Secrets Detection, companies can quickly and easily identify any secrets that exist within containers. This robust security solution helps businesses stay ahead of potential cyber threats, protecting their valuable data and resources.
Unlike other scanners that may generate a high number of false positives due to inaccurate heuristic approaches, our secrets detection engines are designed to look for different yet specific types of keys and credentials, ensuring unparalleled accuracy. Moreover, our scanner results not only pinpoint where the secret is located but also provide a detailed explanation of the problem, including how the secret is being utilized, rather than just its specific attributes such as encryption or encoding.
Considering they are not often found in source code, scanning for secrets in binary form becomes a crucial security measure. By identifying and fixing or removing any secrets in left in plain text, businesses can prevent any accidental leak of internal tokens, keys, or credentials. Our powerful security solution helps you stay one step ahead of potential cyber threats, protecting your valuable assets and ensuring the closing of those unwanted security gaps.
Leveraging a security tool to scan the contents of public-facing registries/repos for secrets is a key step to take to neutralize this often-used tactic by nefarious actors. Taking this final step will help ensure you’re not exposing sensitive information via the components within the repo/registry. If you’re using JFrog Artifactory and Xray this can be configured to occur any time an artifact is deployed to the public-facing repository and even automatically block the artifact from being deployed if secrets are detected.
In conclusion, the ability to effectively detect and manage secrets in the DevOps process before deployment is crucial for maintaining the security and integrity of production software. Secrets mishandling can lead to severe consequences, including data breaches and compromised system and user information. By prioritizing secrets detection as a part of your app sec practices with a trusted software supply chain security solution, organizations can significantly reduce the risk of secrets exposure and fortify their overall security posture.