Stop the Chaos: How to Centralize, Secure, and Control Developer Extensions
Picture this: A new developer joins your team, excited to start contributing. On day one, they spend hours installing and configuring their IDE, searching for the “right” extensions. Their setup ends up being completely different from everyone else’s. Sound familiar? Worse yet, what if that “productivity-boosting” extension or new MCP server they just installed also secretly opened a backdoor in your codebase?
While managing and securing your software supply chain traditionally focuses on open-source components, packages, and container images, the same principles of control, visibility, and efficiency are just as essential for the tools developers use daily: their IDEs.
In this post, we’ll explore the operational challenges of managing and securing developer extensions and plugins and show how IDE Extensions Control with JFrog can provide a solution for a more efficient and trusted developer process.
The Problem: A Wild West of Developer Tooling
Modern software development heavily relies on IDEs like Visual Studio Code and JetBrains products. To boost productivity, developers extensively use add-on functionalities, called extensions in VS Code and plugins in JetBrains IDEs. While powerful, this freedom comes at a significant operational cost:
- Inconsistency and Inefficiency: With every developer pulling tools from public sources, there is no standardized toolset. This leads to configuration drift, makes onboarding new developers difficult, and creates friction when teams collaborate.
- A Lack of Control and Security Risk: Without a centralized system, IT and platform teams lack visibility into the tools being used, making it impossible to enforce best practices, standardize the developer experience, or maintain a consistent and compliant toolchain. This absence of oversight also introduces significant security risks, as unvetted extensions can become vectors for malicious attacks or data breaches.
- Operational Overhead and Wasted Costs: Your organization repeatedly downloads the same extensions and plugins from external sources, wasting network traffic and bandwidth. For large enterprises, this is a significant and unnecessary cost.
The Solution: A Two-Step Approach to IDE Control and Security
These challenges are addressed by extending the power of the JFrog Platform directly to your developers’ IDEs with a two-step approach. This solution provides a clear path to regaining control of your extensions.
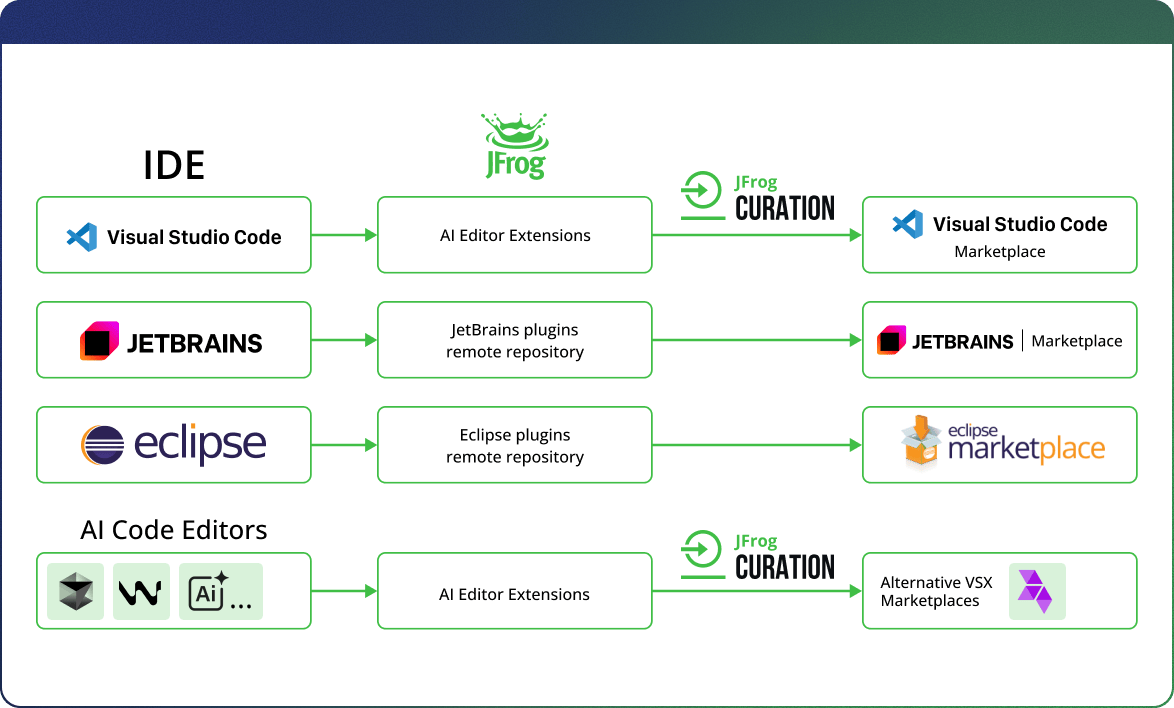
Step 1: Control Access with a Managed Repository
The first step is providing a managed repository for both VS Code (and VS Code forks) extensions and JetBrains plugins. This creates a crucial intermediary between developers and the public marketplaces, ensuring they can only access extensions from your trusted Artifactory repositories. JFrog provides a powerful caching layer within this repository that offers several key advantages:
- Reduced Traffic and Costs: Stop redundant downloads and cut network traffic by serving extensions from a local, cached repository, ensuring instant access for all subsequent downloads.
- Streamlined Operations and Consistency: Standardize the developer experience across your organization with a pre-approved, trusted catalog of extensions, making onboarding and collaboration easier.
- Centralized Visibility and Control: Gain a single source of truth for tracking all extensions used by your organization.
Step 2: Ensure Security with Proactive Curation
Building on the managed repository, JFrog Curation provides a deeper layer of security and control. It actively scans public marketplaces and applies automated policies to prevent the installation of known malicious, vulnerable, or risky extensions. This feature applies these security policies to vet and approve extensions for VS Code and its forks like Cursor and Windsurf, proactively mitigating risks before a developer can even download them.
Get Started in Minutes
Setting up IDE Extension Control in Artifactory is quick and straightforward, and can be done in minutes. Once configured, developers can quickly connect their IDEs, or your DevOps team can easily script the setup across your organization.
Wrapping up: Secure Coding Starts with Your IDE
JFrog’s unified approach helps you regain control and security over your development environment. By bringing smart, real-time protection directly into your coding tools, you can catch issues early and prevent threats. The result is a more trusted development process from start to finish.
Ready to see how shift-left security with JFrog can help your team code and ship more securely without slowing down? Schedule a demo or take an online tour today to experience the difference for yourself.