Announcing JFrog’s Evidence Partner Ecosystem
As software supply chains get more complex, your GRC initiatives become more critical. You need a deeper level of assurance that your software has gone through required processes as it moves toward release. The stakes are only getting higher; new software and AI regulations are gaining ground, and businesses that aren’t able to prove compliance risk facing significant financial and legal consequences.
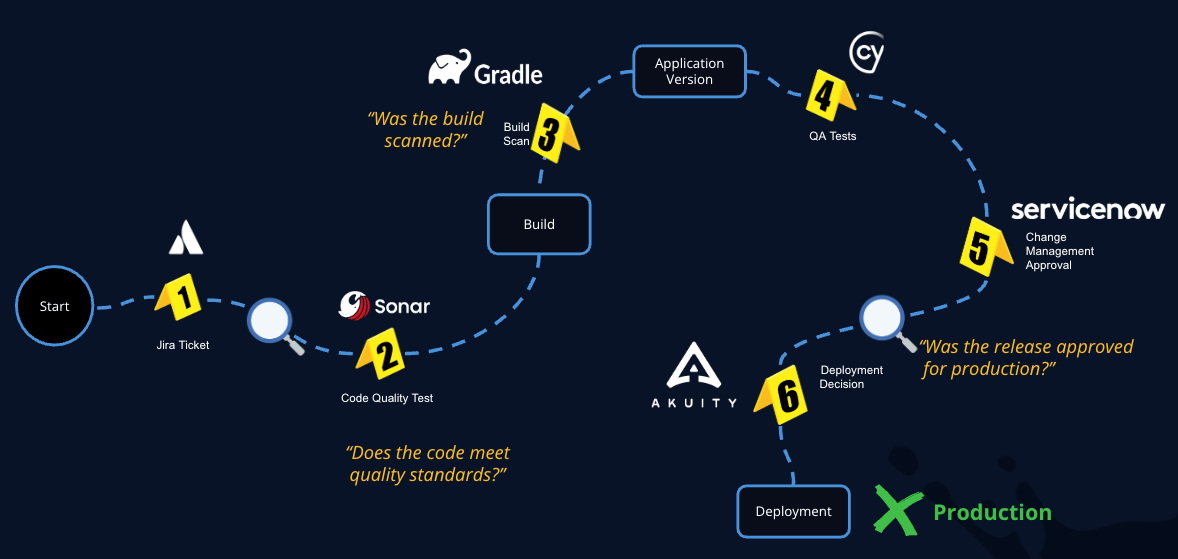
However, the SDLC audit trail is fragmented across teams, tools, and processes, making collecting SDLC evidence a painful, manual process. To help our customers seamlessly capture evidence, we launched third-party Evidence Collection earlier this year, which enables teams to capture important actions across the SDLC and store them in the JFrog Platform, so that each piece of evidence is connected to its relevant binaries for easier auditability. Since the SDLC tool landscape is so vast, we made sure Evidence Collection supports the ability to collect any type of evidence from any tool, with a combination of JFrog CLI and APIs.
Today, we’re thrilled to announce a major evolution to Evidence Collection. Recognizing there’s a need for speed, and setting up integrations with bash scripts can be quite time-intensive, we’ve partnered with industry-leading vendors across the SDLC to natively ingest proof of actions their tools take against a release. This allows teams to automate the collection of attestations without intensive manual set-up, streamlining DevGovOps.
JFrog’s Founding Evidence Collection Integrations
We’re proud to launch our first 12 native ecosystem integrations to JFrog’s Evidence Collection, with a commitment to expand our library based on users’ needs and requests. Here is our list of initial partners and technologies, and what’s possible leveraging our new integrations (shown in alphabetical order):
- Akto: Discovers, tests, and protects MCP servers and APIs across multi-cloud and on-prem environments, bringing vulnerability findings from Akto’s Security Testing into JFrog as evidence proving MCP servers and APIs are secure.
- Akuity: Consumes evidence collected by JFrog, bringing it into Akuity Kargo to make informed deployment decisions, helping teams streamline compliance and audit needs.
- CoGuard: Scans an application’s IaC (Infrastructure as Code) for misconfigurations and other issues, and provides the results as signed evidence that IaC security standards were met.
- Dagger: Composes and runs portable software engineering workflows, and brings signed links to detailed open telemetry traces of the entire build and test process into JFrog as signed evidence.
- GitHub: Generates build attestations when a developer commits code, which is then automatically converted and stored in JFrog permanently, ensuring they’re available anytime for compliance and policy enforcement. Any GitHub attestation, including SBOMs, is captured with JFrog’s Evidence Collection.
- Gradle: Scans builds with Gradle Develocity Provenance Governor, and integrates deep provenance insights from Develocity Build Scan data seamlessly into JFrog as signed evidence.
- NightVision: Conducts DAST (dynamic application security testing) and API discovery, and attaches the results as signed evidence in JFrog. Teams gain traceable, code-aware vulnerability attestations that gate promotions while leveraging JFrog as the single source of truth across the SDLC.
- OCI (Open Container Initiative): Provides a standard to generate builds with SLSA build attestations, which are automatically ingested and displayed in JFrog as build provenance for seamless traceability.
- ServiceNow: Generates change requests, approvals, and vulnerability exceptions, which are captured as signed evidence in JFrog to synchronize change management workflows and a unified audit trail tied to software releases. Also ingests SDLC evidence collected in JFrog to automatically apply policies to decide whether to approve or reject a change request.
- Shipyard: Manages the lifecycle of ephemeral environments for developers and their agents, bringing attestations from Shipyard environments (including build lifecycle timestamps, URL, status, and ownership) into JFrog as signed evidence.
- Sonar: Performs static code analysis, generating signed code quality attestations which are brought into JFrog as verified evidence that software has met quality standards before release. This can be in the form of quality gate results, security scan findings, and code coverage metrics.
- Troj.ai: Automates GenAI redteaming with TrojAI Detect, and attaches the results of TrojAI’s AI security testing as signed evidence in JFrog’s Evidence Collection.
Can’t Find Your Tool? Start With Our Reference Designs
If you can’t find your favorite tool above, you can bring their evidence into JFrog using our new ready-to-deploy reference designs, available on our Evidence Collection GitHub repository. With a basic understanding of how attestations work, you can integrate these reference designs into your workflows in just a few easy steps. Here is what’s available today (shown in alphabetical order):
- Anchore (Syft & Grype): Generates signed SBOMs using Syft and vulnerability scan reports using Grype, creating verifiable evidence that artifacts have been analyzed for known vulnerabilities and their dependencies have been cataloged.
- Atlassian Jira: Captures signed evidence from Jira tickets by scanning Git commits for associated issues, preserving key metadata like ticket type, status, and priority to provide verifiable proof that code changes are tied to authorized work.
- BlazeMeter: Attaches signed performance test reports as evidence, containing key metrics like response times and error rates to provide verifiable proof that the application meets performance and scalability standards.
- Cypress: Creates signed end-to-end test reports as evidence, capturing detailed results including passes, failures, and duration to validate application functionality and user experience.
- GitLab Evidence (SBOM & Provenance): Captures signed build attestations, including SBOMs and SLSA provenance, directly from GitLab CI/CD pipelines to ensure a complete and verifiable audit trail for compliance and policy enforcement.
- Jenkins: Attaches signed attestations from Jenkins pipeline executions, providing verifiable proof of build status, test results, and deployment actions to create a comprehensive audit trail.
- JUnit: Creates signed test result attestations from JUnit reports, providing verifiable evidence of code quality and functional correctness by capturing detailed outcomes of unit and integration tests.
- Katalon: Attaches signed test execution reports from Katalon Studio, providing verifiable proof of automated testing completion and capturing detailed outcomes for UI, API, and mobile tests.
- OpenSSF: Generates signed Scorecard reports as evidence, creating a verifiable attestation of a project’s security posture by analyzing it against a set of open-source security best practices.
- TestRail: Captures signed test run summaries from TestRail as evidence, linking automated test results to test case management and providing a verifiable audit trail of QA processes.
Get Started Today
Our founding integrations for automated, seamless evidence collection are only the beginning of our commitment to providing you with deep visibility and governance over your development processes. We’ll have more exciting integrations to share in the coming months!
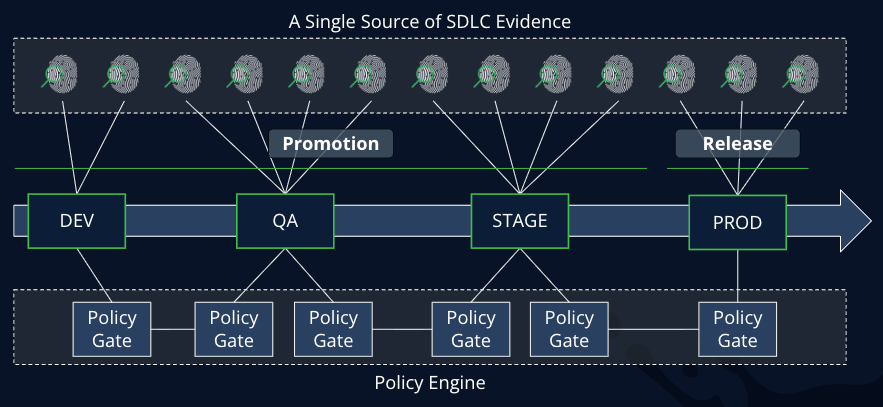
This significant enhancement to Evidence Collection allows teams to truly leverage JFrog as their single source of SDLC proof with a unified, immutable, and verifiable system of record. As your enterprise binary repository, JFrog ensures that verification evidence always stays paired with the artifacts it validates, preventing the disconnect that renders proof useless when stored in disparate systems. By collecting all your SDLC evidence in JFrog, you can also automate application risk governance with JFrog AppTrust, setting and enforcing evidence-based policies for optimal DevGovOps.
JFrog users can get started leveraging Evidence Collection and our built-in integrations today. If you’d like to learn more, you can take a free trial, or speak to a JFrog team member. Are you a technology partner interested in developing an integration for JFrog Evidence Collection? We’d love to partner with you!