CVE-2025-55182 and CVE-2025-66478 (“React2Shell”): All you need to know – UPDATED
IMPORTANT UPDATE: React2Shell Continues to Attack Cloud Infrastructure
(Dec 9th, 2025) JFrog Security Research continues to track the React2Shell vulnerability. Recent developments include the original POC from the researcher who found this vulnerability. This POC shows the simplicity of exploiting this CVE and reflects the real severity and impact of this CVE.
(Dec 12th, 2025) Two high-severity denial of service vulnerabilities – CVE-2025-55184 and CVE-2025-67779 have been published. The CVEs affect the same scenarios as React2Shell, however they cannot be exploited for remote code execution.
The CVEs affect both React and Next.js, and new fix versions have been published in order to address them.
JFrog continues to track and provide updates on React2Shell at research.jfrog.com.
What happened?
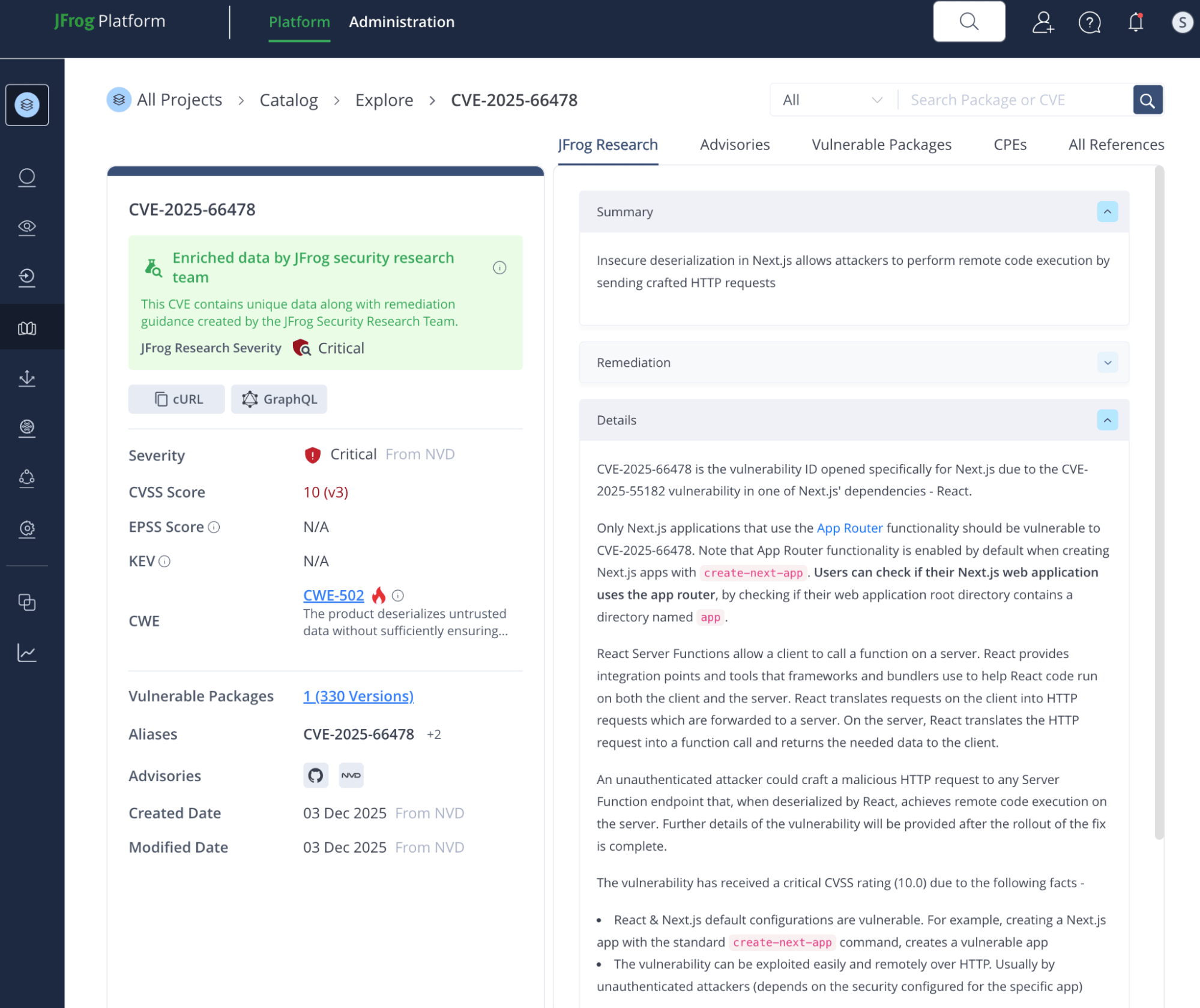
A critical React vulnerability – CVE-2025-55182 (and the corresponding CVE-2025-66478 in Next.js) was published by the React maintainers. The vulnerability was named “React2Shell” by the original researcher as it leads to arbitrary code execution by remote (possibly unauthenticated) attackers.
A remote attacker could craft a malicious HTTP request to any React Server Function endpoint that, when deserialized by React, achieves arbitrary code execution on the server. The exploitation success rate is reported to be nearly 100% in default configurations.
While initially no proof of concept exploits for the vulnerability was available, On December 4th a “non-official” full remote code execution exploit & technical analysis has been made public. The next day, the researcher’s original PoC was also made available – This makes the vulnerability extremely likely to be exploited by external attackers.
Who is vulnerable to React2Shell?
React servers that use React Server Function endpoints
React servers that use React Server Function endpoints are known to be vulnerable. It is possible to check React Server applications for this vulnerable functionality by looking for the use server; directive in any of the application’s source code files, which signifies a Server Function is defined.
For example –
async function requestUsername(formData) {
'use server';
const username = formData.get('username');
// ...
}
export default function App() {
return (
<form action={requestUsername}>
<input type="text" name="username" />
<button type="submit">Request</button>
</form>
);
}
React servers that support React Server Components
React’s advisory states “Even if your app does not implement any React Server Function endpoints it may still be vulnerable if your app supports React Server Components.”.
It is currently unclear what are the exact conditions that allow exploitation of CVE-2025-55182 when React Server Function endpoints are not used, but React Server Components are supported.
If your application supports React Server Components in any way, we highly recommend upgrading the vulnerable components to one of the fixed versions (see table below).
Next.js web applications that use App Router
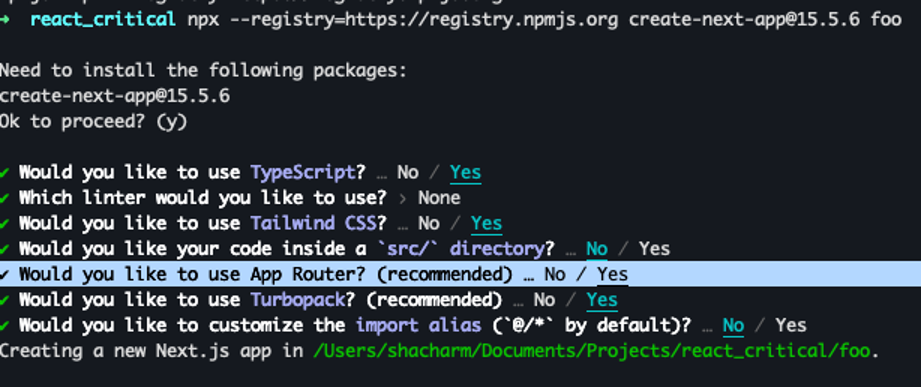
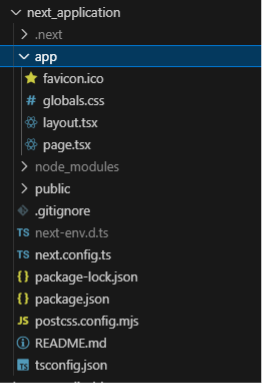
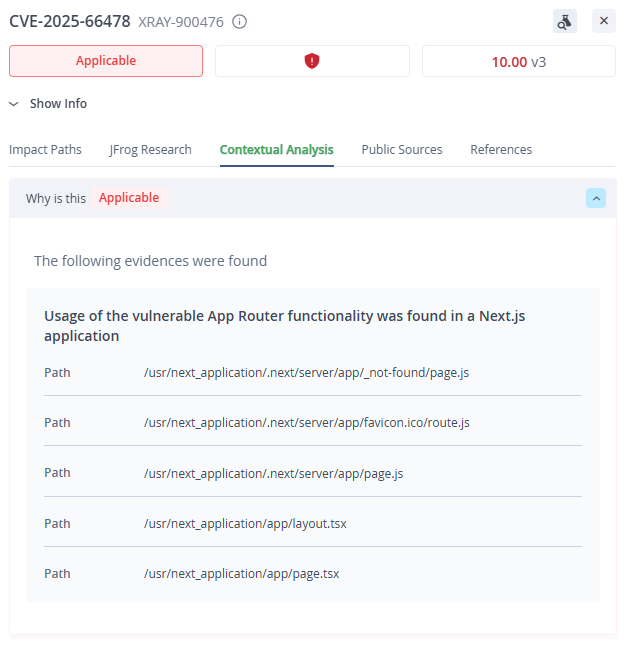
The most likely exploitation vector would be through Next.js web applications (CVE-2025-66478), since these are vulnerable in their default configuration. For example, creating a Next.js app with the standard create-next-app command and using the recommended values creates a vulnerable application, since these values enable the Next.js App Router, which gives access to the vulnerable React Server Function endpoints. These next.js applications will contain the app directory which means they are using the vulnerable App Router.
Vulnerable packages & Fixed versions
| Vulnerable Components | Vulnerable Versions | Fixed Versions |
| react-server-dom-webpack | 19.0.0
19.1.0 – 19.1.1 19.2.0 |
19.0.1
19.1.2 19.2.1 |
| react-server-dom-parcel | 19.0.0
19.1.0 – 19.1.1 19.2.0 |
19.0.1
19.1.2 19.2.1 |
| react-server-dom-turbopack | 19.0.0
19.1.0 – 19.1.1 19.2.0 |
19.0.1
19.1.2 19.2.1 |
| Next.js | 15.0.0 – 15.0.4
15.1.0 – 15.1.8 15.2.0 – 15.2.5 15.3.0 – 15.3.5 15.4.0 – 15.4.7 15.5.0 – 15.5.6 16.0.0 – 16.0.6 |
15.0.5
15.1.9 15.2.6 15.3.6 15.4.8 15.5.7 16.0.7 |
| Next.js | 14.3.0-canary.77 and later canary versions | Downgrade to the latest stable 14.x release by running npm install next@14 |
| Other Frameworks | Any framework/library bundling the vulnerable React RSC implementation (e.g., Vite RSC plugin, Parcel RSC plugin, React Router RSC preview, RedwoodSDK, Waku) |
How can I mitigate React2Shell?
- The definitive way to resolve CVE-2025-55182 and CVE-2025-66478 is to upgrade the vulnerable packages to one of the fixed versions from the table above.
If an immediate upgrade is not possible, the following workarounds can also make the vulnerability unexploitable –
- Next.js apps – In cases where App Router functionality is not heavily used, the web application may be migrated back to using the Pages Router by following the Next.js App Router migration guide.
How can I track React2Shell?
Using the JFrog Platform
- The vulnerabilities are tracked in JFrog Xray as XRAY-900398 & XRAY-900476.
- JFrog Catalog provides comprehensive visibility by automatically detecting all vulnerable React/Next.js packages and offering prioritized remediation paths using fixed version data.
- JFrog Advanced Security users can view Contextual Analysis results for CVE-2025-55182 & CVE-2025-66478 –
Dynamically – Using an open-source detector
We recommend looking for vulnerable web applications dynamically with the following scanner – https://github.com/assetnote/react2shell-scanner.
“The scanner sends a crafted multipart POST request that triggers a specific error condition in vulnerable versions of React Server Components. Vulnerable hosts return a 500 status code with E{"digest" in the response body. This check differentiates vulnerable hosts from those that are simply running RSC.”
What Makes React2Shell so Dangerous?
Here are a few differentiators that make this such an impactful attack:
-
Zero-Config Compromise: Attacking the Default State
The flaw exists in the core deserialization logic of the React Flight Protocol itself. Next.js applications are vulnerable by default, since the vulnerable App Router is used in the default configuration. A standard project generated with “create-next-app” is immediately exposed, even if the developer hasn’t written a single line of custom code. This means the attack surface is enormous, covering a vast number of newly deployed and widely-used applications.
-
Pre-authentication
An attacker does not need credentials, session tokens, or any user interaction to exploit the flaw. The malicious payload targets the React Flight protocol which is processed before the application’s custom authentication logic is executed. The attack only requires a single, specially crafted HTTP request sent to the public-facing server.
-
Reliable Remote Code Execution
The exploit allows attackers to seize complete control over the compromised server’s process. Exploitability is near-100% against vulnerable systems, making the exploit a “set-it-and-forget-it” attack vector for threat actors. The existence of reliable, public PoC code accelerates the timeline for mass exploitation, as it significantly lowers the barrier of entry for less sophisticated attackers. Active scanning and exploitation attempts were detected in the wild within hours of the public disclosure.
Enterprise Response Playbook
What are the steps enterprises (including those who are not JFrog customers) should take in the immediate, medium and long term
Here are the key steps that we recommend Enterprise customers take:
| Time Frame | Recommendation |
| IMMEDIATE | Upgrade the vulnerable packages to fixed versions (see table above) |
| MEDIUM | Next.js apps – If App-Router is not required, disable it and migrate the app |
| LONG | The attack can be detected by WAF rules – Add a WAF security solution |
Get Proactive with JFrog
With the growing number of attack vectors, DevOps teams and Security professionals need to step up their game and move to a shift-left platform based software supply chain management and security solution. To understand how JFrog can help protect your organization from current and future attacks, take an online tour, schedule a demo or start a free trial today.