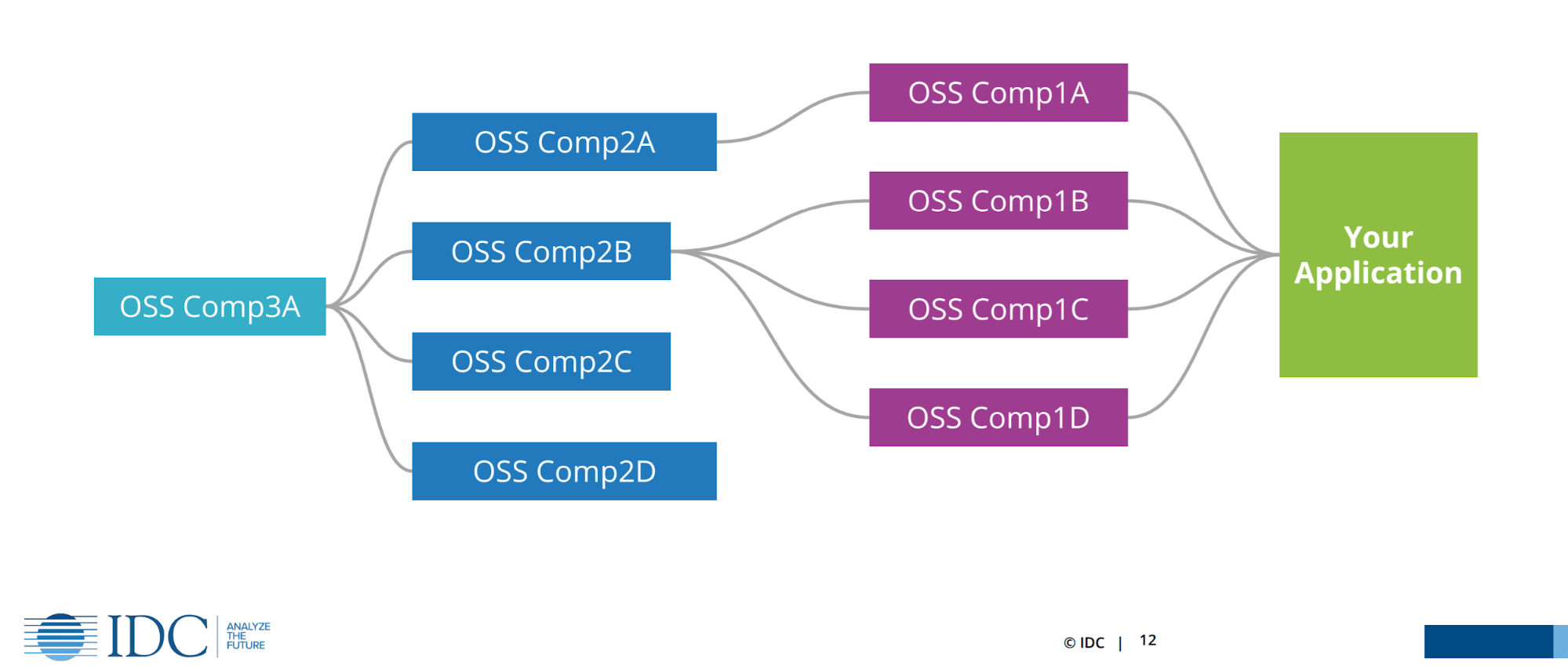
Definition
Software Composition Analysis (SCA) is the use of automated tools to identify open source components within an application’s code base. SCA tools scan software, determine which dependencies and other contents exist within it, then identify the original sources of those components. In this way, SCA tools determine which parts of a codebase have been obtained from third-party sources.
Overview
Software vulnerabilities and risks come in many forms, and they can appear at any stage of the SDLC. Poor coding practices could introduce risks into application source code, while insecure dependencies could be integrated into pre-deployment packages. Outside of potential security breaches, from a business perspective, failure to comply with licensing and regulatory requirements could expose the organization to lawsuits or harm its brand reputation.
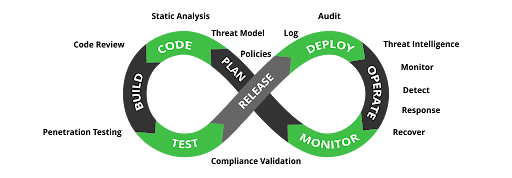
One method used to mitigate these risks is to implement SCA scanning for detection of potential threats, at every stage of the SDLC. Let’s take a deeper dive into what SCA means and how it works, to better understand its benefits and limitations, and how SCA tools should be deployed to achieve continuous protection against an ever increasing number of attacks and vulnerabilities.
SCA tools can detect many types of vulnerabilities, and more specifically insecure dependencies in open source libraries including:
- Vulnerable Libraries: These are libraries that contain known security vulnerabilities that can be exploited by attackers.
- Unmaintained Libraries: Libraries that are no longer actively maintained by their developers can become insecure over time.
- Malicious Libraries: These are libraries that have been intentionally created or modified to include malicious code. Attackers may distribute these libraries through public repositories, hoping that developers will unknowingly include them in their applications. stealing sensitive data, installing backdoors, or compromising the integrity of the application.
In addition, SCA tools can determine when code from a third-party source has been introduced into an application. Detecting such code is important not only because it could contain potential threats, but also because of possible licensing violations.
According to IDC, SCA leverages scanning tools such as JFrog Xray to provide critical visibility detecting vulnerabilities, compliance issues and more.
It is important to note, however, that a single SCA scan is not necessarily capable of detecting security issues across all vulnerability categories. The results for a given scan depend on whether you are scanning application source code, application binaries, application packages or configuration files.
Therefore it is recommended to scan your applications at every stage of development and production to ensure detecting all instances of a particular vulnerability. For example, because insecure dependencies could be defined in source code as well as in configuration data, it is necessary to scan both the source code and the release package to detect all potential dependency-related vulnerabilities.
Examples of SCA Scanning
To illustrate what Software Composition Analysis means in practice, let’s look at two examples of using SCA to find real-world risks and vulnerabilities.
Insecure module in source code
For this example, we are looking at a legacy Python application that is dependent on a specific version of an external Python module. For illustrative purposes, the defective module has been named “Insecure” where version 1.2.3 is imported into the application using the following source code:
import pkg_resources
pkg_resources.require("Insecure==1.2.3")
import insecure
In this scenario version 1.2.3 of the Insecure module is known to be vulnerable. By scanning your application’s source code, an SCA tool could determine that your application is importing an insecure module. Your developers could then update the application to use a secure version of the module.
In parallel, the DevSecOps team might be able to mitigate the issue by blocking whichever conditions allow the vulnerability in the insecure module to be exploited within the application’s runtime environment. For example, if the vulnerability requires a certain port to be open in order to be exploited, the DevSecOps team can make sure the port is closed.
Insecure package dependency
In this example, we consider a Debian package, a file format used to install software on Ubuntu and certain versions of Linux, that includes a configuration file at the location:
packagename-1.0/debian/control
The contents of the file include:
Source: packagename Section: unknown Priority: optional Maintainer: "Firstname Lastname" <email.address@example.org> Build-Depends: ssl-cert (= 1.0.39) Standard-Version: 4.5.1 Homepage: <insert the upstream URL, if relevant> Requires-Root: no
Among other things, this file defines version 1.0.39 of the package ssl-cert as a dependency, meaning that if you install the application on a Linux server, then version 1.0.39 of the ssl-cert package is installed as well. Since ssl-cert version 1.0.39 turns out to contain a known vulnerability, installing the package introduces an exploitable threat into the host environment.
In this instance deploying an SCA tool that reads the control file for this package would detect the insecure dependency, then flag it so security engineers can mitigate the risk.
Benefits of SCA Scanning
SCA is not the only way to detect risks and vulnerabilities within source code or binaries. Prior to the introduction of SCA technology, manual review of the application at each stage of the development was the only option, which slowed down development speed and was less accurate due to human error. Today SCA has become a core security tool in the DevSecOps arsenal, providing a range of benefits including:
Automated workflow
By leveraging automation, SCA tools can find risks using background processes that are transparent to developers, while security teams can spend their valuable time on improving protection of the software supply chain.
Early detection
The ability to automate vulnerability detection means that you can start scanning at the earliest stages of the SDLC, resulting in detection of potential security issues early in the development process, where they can be handled in a faster and more efficient manner.
For instance, if you detect an insecure dependency while you’re still in the coding stage of the app, it is relatively straightforward to update the source code to solve the issue. If the same vulnerability remained undetected until deployment of the release into production, it would necessitate going back into the code, re-compiling and testing the software wasting valuable time and resources.
Dependency visibility
Dependencies are a good thing. They allow developers to integrate functionality into applications without having to write all of the code from scratch, which saves time and increases development efficiency.
The trade-off is that applications that lean heavily on dependencies end up with dozens of different modules, libraries and dependencies that are required to run the application. To complicate matters, those same dependencies could be defined in multiple locations such as the source code, configuration files or deployment instructions, making it extremely difficult to track them all.
SCA tools address this issue by providing visibility into which dependencies are defined in the applications, , which versions are required and whether those versions are known to be vulnerable or secure.
Licensing compliance
SCA tools not only check for security issues, they can also alert developers that are in the process of adding a particular third-party package to a codebase, that it may be in violation of relevant licensing agreements.
In such cases, the SCA tool would flag the open source license, allowing developers to see if they can incorporate the code in a compliant manner, avoiding potential legal liability and costly lawsuits..
Limitations of SCA
SCA is a powerful technology that should be in every DevSecOps arsenal, but it’s important to recognize that SCA solutions alone won’t catch every type of threat and vulnerability.
Applicability
For the most part, SCA tools can only detect risks associated with open source code or dependencies. They can’t flag security problems caused by proprietary dependencies, because those dependencies are not subject to public scrutiny, and security issues within them are therefore not typically reported in public databases.
In addition, while SCA tools can identify some types of risks that developers may introduce into their code due to poor coding practices, other risks may evade detection. There are an infinite number of ways to write source code, making it impossible to detect every potential deviation from secure coding practices.
External Configuration Files
Another major limitation of SCA tools is their ability to scan only configuration files within an application, but not configuration data that is external to the application. For example, if you configure insecure Identity Access Management (IAM) settings in a cloud environment where you deploy an application, your SCA tool won’t catch insecure settings in that configuration. To catch those types of vulnerabilities, requires IaC scanning capabilities, available in solutions such as JFrog Advanced Security, IDE Plugins or CSPM tools.
Alert Fatigue
Like many security tools, SCA scanning can result in a large volume of alerts which can contribute to alert fatigue if not properly managed. The problem is exacerbated in enterprise environments due to project complexity and the large number of dependencies which can detect a potential vulnerability in many components that may not be exploitable in reality. This can quickly become overwhelming for DevSecOps teams who must figure out a way to prioritize potential vulnerabilities and respond to alerts which represent serious threats while disregarding the rest.
Besides the sheer number of alerts, SCA tools may also report vulnerabilities that are not actually exploitable in the context of the application. This can happen due to generic vulnerability database entries that do not account for the usage of a component within a specific application. Therefore it is extremely important to use SCA scanners that minimize the number of False Positives, as each occurrence requires developers to spend valuable time investigating and dismissing alerts, which slows down development speed and reduces overall productivity.
How to Leverage SCA Scanning
Since the results of SCA scanning depends on the types of resources being scanned, the most effective way to leverage SCA, to make sure it is deployed at multiple stages of the application development lifecycle.
SCA scanning can help detect vulnerabilities at multiple points in the development cycle
Start by doing an SCA scan on the source code at the start of the development pipeline. From there, scan the binaries that are created during the build process. The third phase, should include scanning of the packages and containers where the binaries are stored for distribution.
The more consistently you integrate SCA scanning across the software development lifecycle, the greater your chances of catching and addressing security and licensing-compliance issues, before they trigger serious disruptions and financial loss.
Trends in SCA Security
The continuing evolution of software development operations and increasing use of open source components, are having a profound impact on the latest trends in SCA security, including:
Enhanced Features
- Integration with DevOps Platforms – This enables automated scanning of open-source components as part of the development process, ensuring vulnerabilities are identified and addressed as early as possible in the SDLC.
- AI and Machine Learning – Incorporation of these algorithms into SCA tools are designed to improve accuracy and provide more insightful vulnerability analysis including prioritization, potential impact and suggested responses.
- Enhanced Compliance & Governance – As more industry and governmental standards emerge, SCA tools are adding more sophisticated policy and licensing management capabilities to ensure compliance with internal policies and external regulations.
- Expansion of Vulnerability Databases – The scope and detail of these databases, which are the basis for SCA vulnerability detection, are expanding to draw on a wider range of sources, including comprehensive information about the context, exploitability, and remediation for published CVEs.
- Additional Language and Framework Support – With the high rate of adoption of new languages and development frameworks, SCA tools must expand their language support to stay effective and provide a full solution for security teams.
- Reporting and Visualization – These features are becoming increasingly important as organizations strive to increase the efficiency of security operations including interactive dashboards, real-time reporting and integration into leading DevOps platforms.
Consolidation of Point Solutions
In addition to these important enhancements, it is important to recognize the larger trend of point solution consolidation. The concept is that a multiplicity of disparate security tools from multiple vendors are difficult to manage, can produce contradictory results and lead to siloed, rather than holistic end-to-end solutions.
Consolidation of security tools leads to better security and more efficient operations. For example, a full scanning solution could include not only SCA scanning, but SAST and DAST solutions as well.
The JFrog Approach to SCA
JFrog’s approach to Software Composition Analysis (SCA) is based on their platform’s ability to provide full traceability and provenance for the software supply chain. JFrog Artifactory, the central repository for all software artifacts, captures expansive and detailed metadata for every component in the platform, making it fully traceable. This enables organizations to identify all transitive dependencies in third-party components and export required data in a compliant Software Bill of Materials (SBOM) automatically or on demand.
JFrog’s security offering is natively integrated with Artifactory, enabling fast and efficient scanning and remediation in the context of the actual software inventory. With JFrog’s Contextual Analysis, wasted time is saved and the most critical vulnerabilities are prioritized for remediation based on their applicability within the environment, not just their CVSS score.
JFrog Advanced Security extends the capabilities of JFrog’s SCA with deep security research by the JFrog Security Research team that delivers extended insights into security issues, their impact on the software, and advice on how to remediate them. The JFrog Platform helps DevSecOps improve performance with prioritized, contextual remediation advice that identifies what matters most to ensure protection of the software supply chain.
JFrog’s SCA approach is based on their platform’s ability to provide full traceability, provenance, and prioritization capabilities to save time on remediating vulnerabilities. Continue to explore more topics related to SCA here, or if you’d like to see the platform in action, schedule a demo, take a tour or start a free trial at your convenience.