GoCenter Reveals Go Module Vulnerabilities With Xray
UPDATE: As of May 1, 2021 – GoCenter central repository has been sunset and all features deprecated. For more information on the sunsetting of the centers read the deprecation blog post
Golang developers care a lot about security and as Go modules become more widely used, they need more ways to assure these publicly shared files are safe.
One unique feature included with Golang version 1.13 is the foresight that went into authentication and security for Go modules. When a developer creates a new module or a new version of an existing module, a go.sum file included there creates a list of SHA-256 hashes that are unique to that module version. That go.sum file is then sent to Golang’s official checksum database where it is stored and used to verify that modules haven’t been tampered with when accessed later by a GOPROXY. This helps keep the integrity of packages intact.
The checksum authentication feature helps create trust among developers, but it isn’t fully tamperproof. If a vulnerability is introduced in the original module’s files, the GOSUMDB will only be able to indicate that the module wasn’t changed later. This doesn’t solve the problem of malicious code being introduced in the very first commit.
Luckily, GoCenter can now tell you when any Go module has a known vulnerability. We’ve brought the power of JFrog Xray’s security scanning to this reliable repository of Go modules for the Golang developer community.
The Xray DevSecOps Difference
JFrog Xray is the DevSecOps tool relied upon by some of the largest enterprises in the world to identify known vulnerabilities in their application builds. When joined with Artifactory, it performs deep recursive scans on the binaries held in repositories, to identify anywhere that open source components with reported security weaknesses or malicious code have been used.
Xray supports scanning of a large variety of language and package types. The most recent release of Xray supports vulnerability scanning of Go modules as well, so that Golang applications can fully implement DevSecOps procedures to prevent risky binaries from being deployed from Artifactory into production.
Xray Scans GoCenter
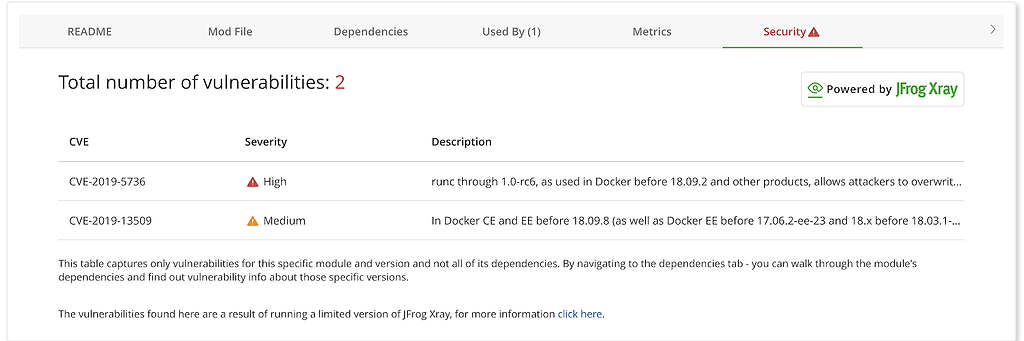
We’ve now brought the Xray difference to GoCenter as well, so that every module and version in GoCenter is automatically scanned for known vulnerabilities recognized in public vulnerability databases such as NVD. Those results are stored in GoCenter, which will list all vulnerabilities that exist in the module version.
When you land on a specific module page, you’ll know if there is a vulnerability in that module version if a warning triangle exists next to the security tab. Clicking on the tab or triangle will direct you to the security page that provides specific information about each vulnerability including the CVE number, severity, and description.
Try It and Learn More
Xray in Go Center is just a subset of Xray’s full capabilities! This universal analysis of all of your binary software components adds an extra level of trust in your Go projects. By scanning binary components and their metadata, going through dependencies at all levels, Xray provides unprecedented visibility into issues lurking in your module dependencies. For more detailed information about each vulnerability including remediation steps, you’ll want to checkout the full version of Xray, which includes:
- Security and Compliance Visibility multiple technologies (not just Golang)
- Enhanced vulnerability database from JFrog’s Security Research Team
- IDE Integration
- Open for Integration and Automation
- Stopping Download of Vulnerable Packages
- Xray for License Compliance
- Impact Analysis Graph
In the meantime, take a look at GoCenter to see what Xray can reveal. You may find that modules you’re already using have issues you weren’t aware of. Helping Golang software to be more secure is our proud contribution to the open source developer community.