Still Trusting Automated Patches Blindly? Think Again
The Breach: A High-Impact Compromise
JounQin’s npm account, the maintainer of popular packages such as eslint-config-prettier, was compromised in a phishing attack. The attackers used the breached credentials to publish six malicious versions of eslint-config-prettier, along with three additional infected packages tied to the same account. In total, the compromised packages see roughly 78 million weekly downloads. Notably, the account had publishing rights for packages with a combined weekly download count of 180 million!
Hijacking isn’t new. We’ve covered similar incidents before. This latest case is just another reminder of how vulnerable widely used and trusted packages can be.
First Signs: A Suspicious Version Emerges
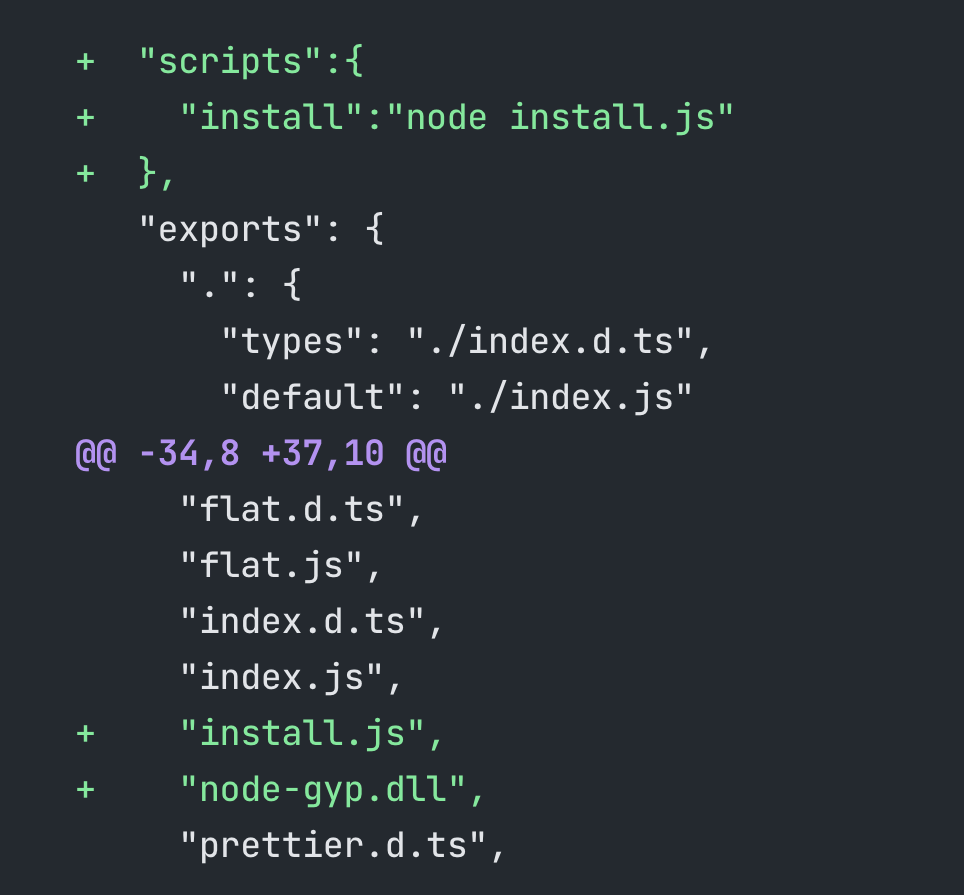
On July 18, 2025, a GitHub issue (#339) was opened by user dasa in the eslint-config-prettier repository, flagging unusual versions that had recently appeared on the npm registry. One version in particular, 10.1.7, stood out due to a suspicious modification: An install script had been quietly added to its package.json, raising immediate concerns.
Maintainer Confirms Phishing Attack
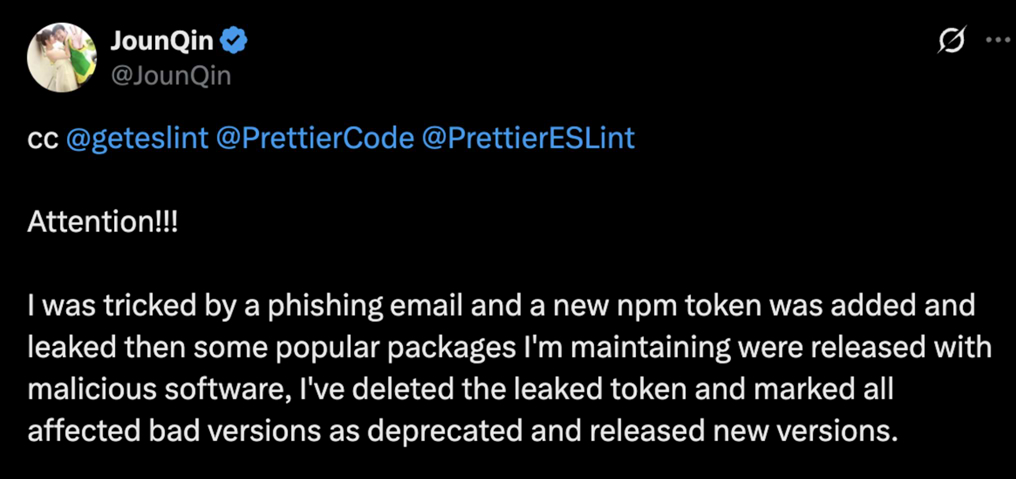
On July 19, 2025, the maintainer of eslint-config-prettier confirmed he had fallen victim to an email phishing attack. The attackers gained access to his npm account and used it to publish malicious code across several packages. The most notable target was eslint-config-prettier, which alone accounts for 31 million weekly downloads according to npm.
The Full Blast Radius:
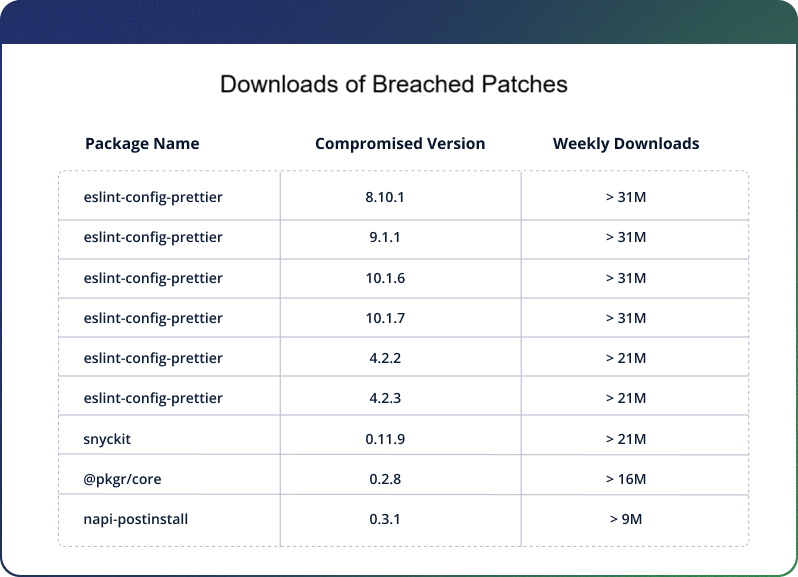
In a post on X, JounQin also revealed the full list of compromised packages that were published with malicious code. The affected versions spanned several widely-used projects, including multiple releases of eslint-config-prettier. Here’s the breakdown:
Collectively, these packages represent tens of millions of weekly downloads, making this one of the most severe npm supply chain compromises in recent memory.
Windows-Only, But Still Dangerous
The malicious behavior was delivered via an embedded node-gyp.dll PE32+ binary included in the compromised packages, effectively limiting the attack to Windows systems only. Due to the payload’s format, GNU/Linux distributions and macOS users are unlikely to be impacted. On infected machines, the payload installs the Scavenger malware, which enables attackers to exfiltrate files, steal credentials, and carry out a range of malicious activities.
JFrog Curation: Your First Line of Defense
With JFrog Curation’s advanced detection capabilities, you’re no longer relying on blind trust. Malicious or suspicious packages flagged by the community or JFrog’s security research are automatically blocked, preventing them from ever entering your organization. You control what’s allowed in before it becomes a risk.
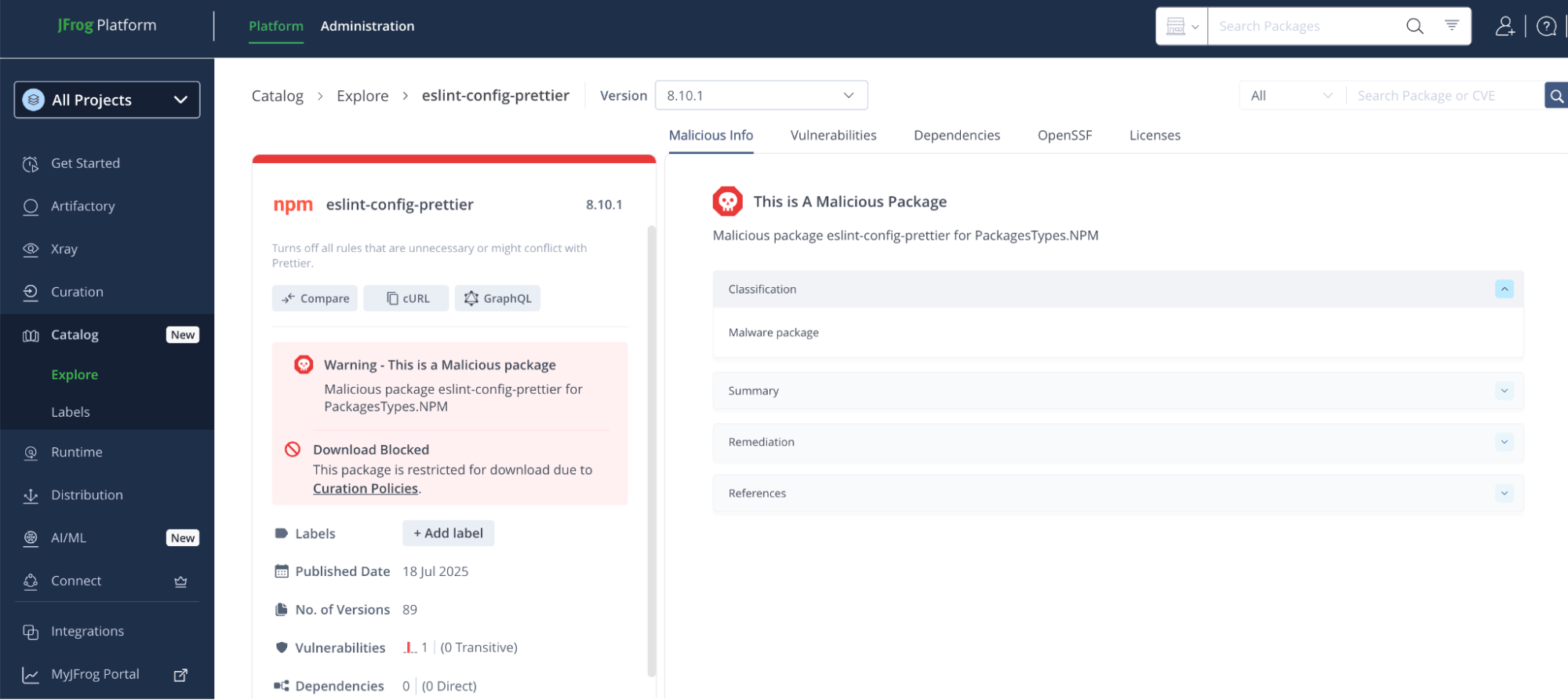
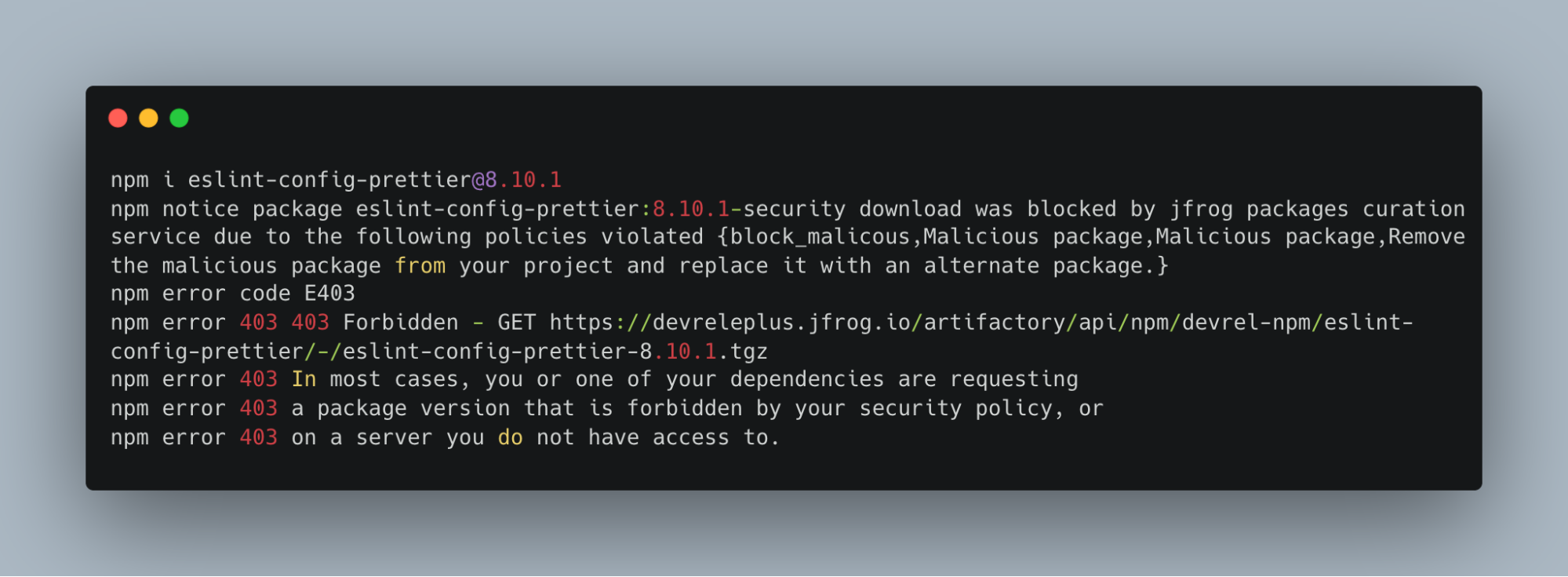
At this stage, all compromised packages would already be flagged as suspicious by the JFrog Platform, automatically, without any manual input. Our supplemental research clearly indicated what the system had already detected, providing technical validation regarding the efficacy of JFrog’s solution.
Organizations using JFrog Curation with a malicious block policy are fully protected, not just from these specific packages, but from similar supply chain attacks in the future.
Final Thoughts
This incident is a wake-up call for the entire ecosystem – even the most trusted packages can become attack vectors overnight. Without active governance and real-time protection, you’re flying blind. Make sure you have the right tools in place – before it’s too late.
For more info on how JFrog can help manage and protect your development environment, feel free to take an online tour, schedule a demo or start a free trial at your convenience.