Securing Vibe Coding: JFrog Introduces AI-Generated Code Validation
A fundamental shift in software development is already here. Gartner predicts that by 2028, 75% of enterprise software engineers will use AI code assistants – a massive leap from less than 10% in early 2023. While this AI-driven speed creates a competitive advantage, it also opens a dangerous new front in the battle for software supply chain security. Traditional Software Composition Analysis (SCA) tools are essential for scanning declared dependencies, but many of them are completely blind to the risks “laundered” into your codebase from an AI prompt or a copy-pasted snippet. To address this critical visibility gap, JFrog is excited to announce the launch of AI-Generated Code Validation, a key new enhancement to JFrog SCA.
Your Biggest Blind Spot: The Dangers of Untracked Code
Even the most robust SCA scanner is designed to analyze packages, which are the declared dependencies in your project. However, untracked code may bypass that checkpoint entirely. Untracked code often enters a project during fast-paced workflows like “vibe coding,” where a developer uses natural language prompts to have an AI generate code, focusing on quick results over source verification. Whether that code comes from an AI or a manual copy-paste, it is invisible to standard checks and creates critical risks:
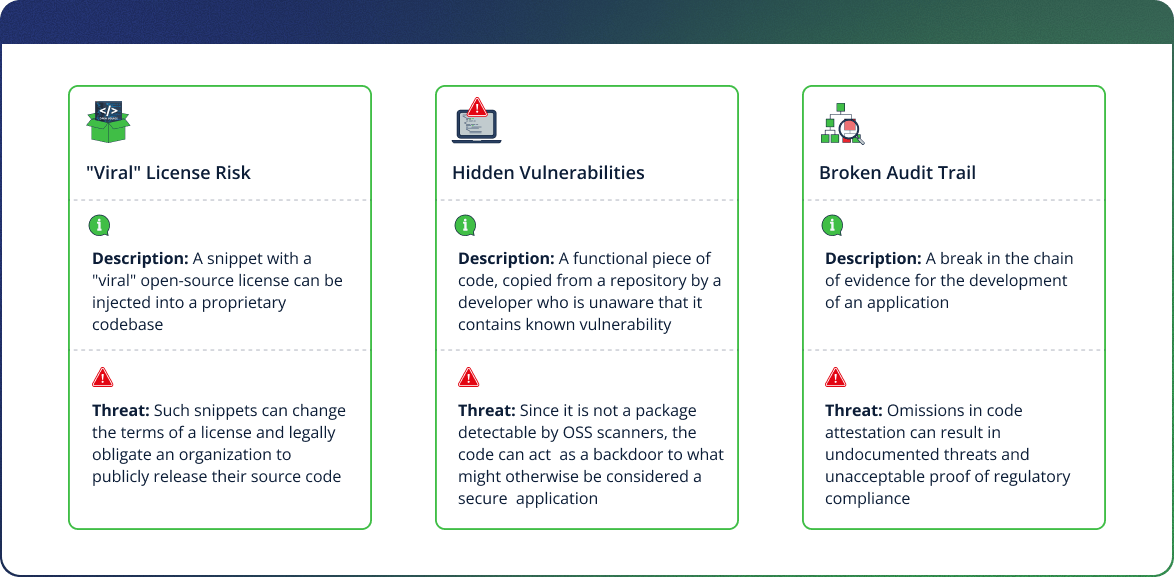
Understanding three key dangers of untracked AI-generated code
- “Viral” License Risk: A snippet with a “viral” open-source license can be injected into your proprietary codebase. For example, a developer might copy a useful function licensed under the GNU General Public License (GPL). The GPL is a strong “copyleft” license and incorporating that snippet could legally obligate your company to release the source code of your entire proprietary application to the public. This poses a direct and severe threat to your intellectual property.
- Hidden Vulnerabilities: A developer might use a functional piece of code, unaware that it was copied from a repository with a known critical vulnerability. As it is not a formal package, it remains an invisible backdoor in your application.
- Broken Audit Trail: When you don’t know the origin of every line of code, you break the chain of evidence required to prove your software is secure, making it impossible to pass security reviews.
AI-Generated Code Validation: Deep Source Analysis with Semantic Matching
To solve this, our AI-Generated Code Validation uses a more intelligent approach: semantic matching.
Instead of just matching text, we analyze the code’s underlying logic and function. We understand what the code does, or what it’s meant to do, not just what it looks like. Ultimately, this allows you to guarantee the integrity of your software, turning code provenance from your biggest blind spot into a verifiable strength.
Some newer solutions use LLMs, but they are slow, resource-intensive and create pipeline bottlenecks. JFrog’s approach is different. We deliver the high accuracy you need to find hidden risks, but with the speed and performance your developers demand.
How It Works: From Detection to Prevention
JFrog’s semantic matching technology is integrated directly into the developer workflow as a security guardrail. If a developer attempts to merge a pull request containing an AI-generated or copied snippet that violates your company’s security or license policies, the action is blocked.
This preventative control stops risk at the source and directly resolves the threats from untracked code:
- Proactive IP and Compliance Enforcement: When a developer, during a “vibe coding” session, unknowingly introduces a snippet with a “viral” open-source license, the pull request is blocked. Your intellectual property is protected automatically, and compliance is enforced before a violation ever reaches the main branch.
- Real-time Vulnerability Prevention: If a copied snippet contains a known critical vulnerability, the pull request is blocked. This stops a potential backdoor from ever entering your application, shifting your security posture from reactive clean-up to proactive prevention.
- An Enforced Audit Trail: The block itself becomes a critical entry in your audit trail, providing verifiable proof that your security policies are being actively and automatically enforced at the earliest point in the development lifecycle.
Secure Your Code Today
Delivering innovative software on tight deadlines is the goal for every development team, but it shouldn’t introduce unknown risks. By integrating deep source analysis directly into our foundational SCA scanner, the JFrog Platform transforms this blind spot into a control point.
Ready to close the visibility gap in your software supply chain?
Then start by learning more about how to protect your AI generated code by signing up for a beta at your convenience.