Denial of Service Vulnerability in Envoy Proxy – CVE-2022-29225
The JFrog Security Research team is constantly looking for new and previously unknown software vulnerabilities in popular open-source projects to help improve their security posture. As part of this effort, we recently discovered a denial of service (DoS) vulnerability in Envoy Proxy, a widely used open-source edge and service proxy server, designed for cloud-native applications and high traffic websites. JFrog Security Research responsibly disclosed this vulnerability, which was subsequently assigned to CVE-2022-29225.
CVE-2022-29225 is a DoS vulnerability that enables attackers to crash the proxy server, leading to performance degradation or unavailability of resources handled by the proxy. This vulnerability was fixed in Envoy versions 1.19.5, 1.20.4, 1.21.3 and 1.22.1, see also the “Fixes and Workarounds” section at the bottom for a solution if you are using Envoy but cannot upgrade to any of the new versions.
CVE-2022-29225 Technical Details
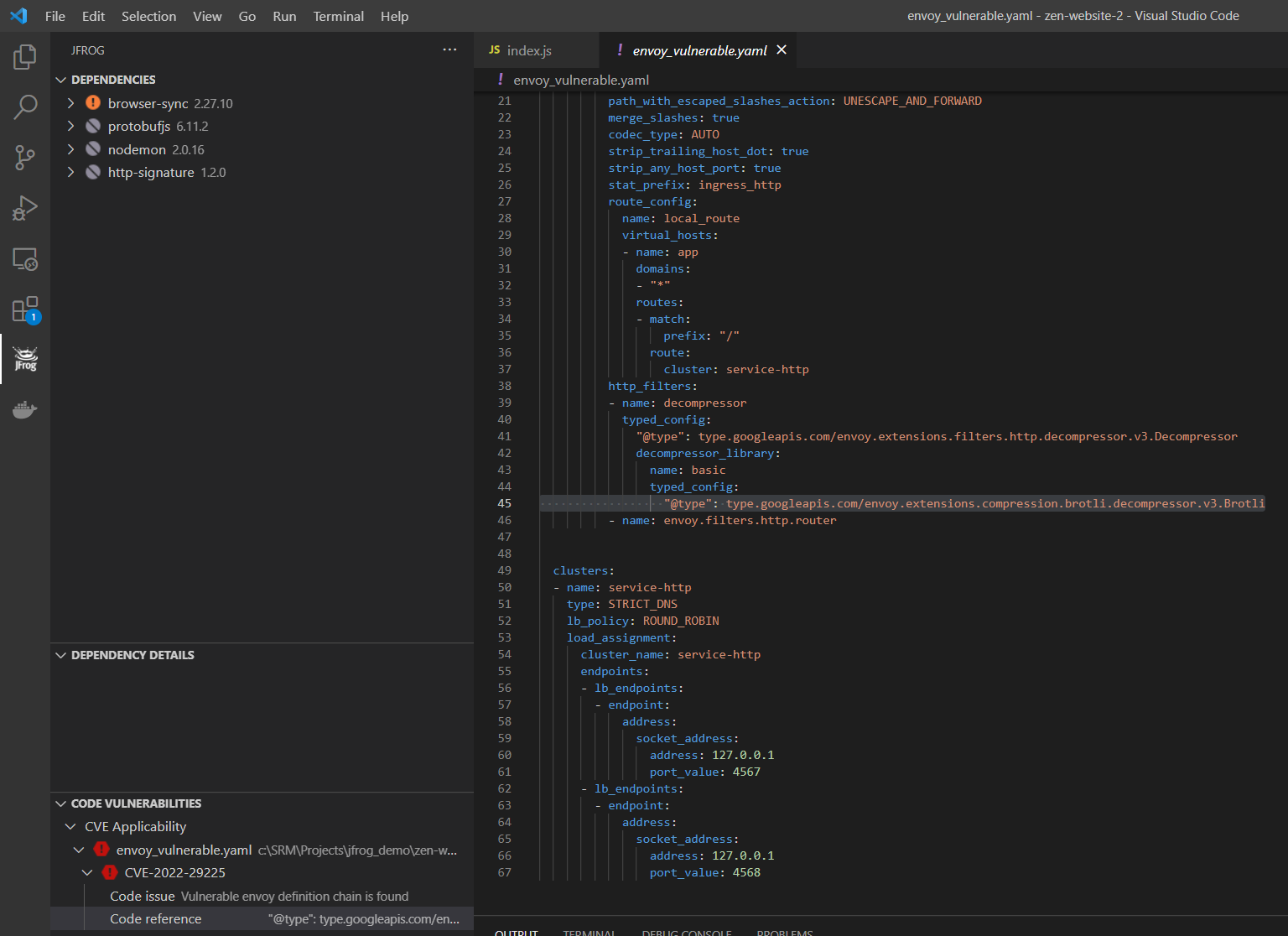
Envoy proxy has the possibility to decompress GZip and Brotli data. These features can be enabled via configuration, by adding the relevant filters. For example, to enable Brotli decompression, the following filter could be added under http_filters:
- name: decompressor
typed_config:
"@type": type.googleapis.com/envoy.extensions.filters.http.decompressor.v3.Decompressor
decompressor_library:
name: basic
typed_config:
"@type": type.googleapis.com/envoy.extensions.compression.brotli.decompressor.v3.Brotli
The code that is in charge of decompressing the user supplied data does not implement a size limit for the output buffer, allowing the buffering of virtually unlimited amounts of data by accumulating all the extracted data into one large buffer before sending it upstream. An attacker can send a simple Brotli Zip Bomb (a small zip file that decompresses to a very large file) that can cause severe performance issues or crash the Envoy process due to memory exhaustion.
How Can CVE-2022-29225 Be Exploited?
If the Envoy configuration allows decompression of Brotli files by using the configuration above, an attacker can create a Brotli bomb or use a ready-made one that can be found online and send it to Envoy using the curl command. For example, assume Envoy is running on IP address 10.0.0.1, listening for HTTP on port 10000. Running the following command:
curl -v http://10.0.0.1:10000 -H "Content-Encoding: br" -H "Expect:" --data-binary @/tmp/10GB.html.br
Will send the /tmp/10GB.html.br file to it. This file, when decompressed using the Brotli algorithm, will decompress to 10 GB of data in the memory of the process. In most cases the machine’s memory will not be able to handle such large amounts of data and the Envoy process will eventually crash. In most cases, before the process crashes, there will be severe performance issues due to the processor allocating a lot of resources to the decompression process.
It is important to note that due to some differences between the GZip and Brotli decompressions, this issue will most likely affect only Brotli configurations and not GZip, though the code of the GZip decompression contains the same root issue as the Broli decompression code.
Is the JFrog Platform Vulnerable to CVE-2022-29225?
After conducting a comprehensive internal inspection, we concluded that the JFrog DevOps platform is not vulnerable to CVE-2022-29225.
Fixes and Workarounds
As advised by Envoy, the best solution is to upgrade to Envoy version 1.19.5, 1.20.4, 1.21.3 or 1.22.1, which completely fixes the issue.
If upgrading is not possible, make sure that your configuration does not allow Brotli decompression. The Brotli decompressor (type.googleapis.com/envoy.extensions.compression.brotli.decompressor.v3.Brotli) can either be completely removed, or replaced with the Gzip decompressor (type.googleapis.com/envoy.extensions.compression.gzip.decompressor.v3.Gzip)
Acknowledgement
We would like to thank Harvey Tuch from the Envoy maintainer team for professionally handling this issue.
Stay Up-to-Date with JFrog Security Research
Follow the latest discoveries and technical updates from the JFrog Security Research team in our security research website and on Twitter at @JFrogSecurity.
Finding Vulnerable Versions with JFrog Xray
In addition to exposing new security vulnerabilities and threats, JFrog provides developers and security teams easy access to the latest relevant information for their software – including the use of Envoy open-source library versions and associated CVEs – with automated security scanning by JFrog Xray SCA tool.
JFrog’s contextual analysis engine can also detect Envoy instances with a configuration vulnerable to this issue –