Avoiding Clear Text Passwords in Maven
On Secure LDAP Integration: Avoiding Clear Text Passwords in Maven Settings and Controlling Login Fallback
First, Some Background
One shortcoming of Maven is that it requires you to store your repository passwords in clear text inside the settings.xml file. Now, this stops being mere annoyance and starts becoming a real security hole once your repository’s authentication is done by integrating with an external security service, such as LDAP. SSL can help you overcome transmitting your password in clear text, but storing your LDAP/Active Directory password in clear text is a different story, as it opens the door for anyone who grabs your settings file to all resources accessible by you on the organizational network: email accounts, shared documents, backoffice applications etc. Certainly not a welcome side-effect.
Artifactory includes an out-of-the-box LDAP integration, that can be quite easily set up and tested from the web UI. Soon after introducing LDAP into Artifactrory, we received an inspiring feature request from Patrick Crocker, that led us to implement the current encrypted password support which overcomes this security hole in Maven.
BTW, you can use encrypted passwords even without LDAP, of course, for just not letting people seeing what your clear text passwords look like.
How Does It Work?
First, an Artifactory admin has to enable password encryption by going to Admin:Security:General and setting the password encryption policy to either “Supported” or “Required”:

This activates secure password generation for each user based on a secure key stored as part of the user’s details.
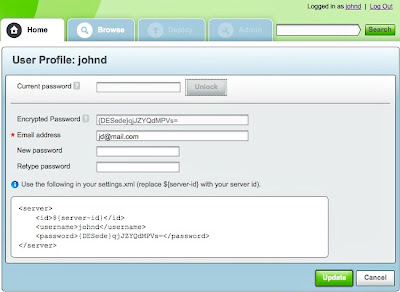
From now on, any user can use his profile page (your login name on the upper-right corner) to get an auto generated Triple DES secure password to use in his settings.xml file –
just type in your current password and take your secure password for the Encrypted Password field.
Artifactory also gives you a sample server xml element snippet for use your settings.xml.
Controlling Login Fallback
A common case that often appears when integrating with an external authentication system is that you want to force all users to go exclusively through LDAP, except for a couple of special users that need to be able to log in using internal passwords even when the LDAP server is unreachable (e.g., when a change on the LDAP server requires adjusting the connection settings), or when no LDAP authentication details exist (like in the case of a CI build server). For this kind of users, just leave the “Disable Internal Password” flag off in the users’ details panel.