Reverse SSH Tunneling – From Start to End
Reverse SSH Tunneling – From Start to End
As access to machines becomes increasingly essential in business, especially with the rise of cloud applications, users have become accustomed to having full or limited remote access, making access machines remotely absolutely necessary.
The occurrence of the ongoing Covid-19 pandemic has highlighted the necessity for remote access as businesses have had to decentralize their operations and adapt to remote working environments. For this reason, both corporations and individuals have exploited various localization techniques that are available to them.
This article provides a step-by-step guide for setting up and using reverse SSH tunneling in Linux-based environments. Specifically, the article introduces the concept of SSH tunneling, which includes its definition, use, and disadvantages before transitioning to reverse SSH tunneling.
SSH Tunneling
SSH is the cryptographic network protocol that runs on port 22 and allows you to connect to the shell of a remote machine. On the other hand, SSH tunneling/port forwarding is a mechanism that creates a secure SSH connection between a local and remote computer. Because of its encrypted nature, you can use SHH tunneling to transmit messages that use unencrypted protocols such as IMAP, VNC, or IRC.
There are three types of port forwarding:
- Local Port Forwarding
This connection enables you to access another server from your local computer. However, you need to know two port numbers and your destination server. For instance, if you want remote access to www.HackerOne.com, your SSH tunnel would be:
ssh -L 8080:www.HackerOne.com:80 <host>
Where you replace <host> with your laptop’s name and the -L option specifies local port forwarding. You can use any source port number (see Wikipedia’s list of TCP and UDP port numbers). Even so, port numbers that are less than 1024 or greater than 49151 are reserved for the system and can only work with specific source ports.
- Remote Port Forwarding
Unlike local port forwarding, remote port forwarding allows you to connect from a remote SSH server to remote network service located at the tunnel’s client side. To do so, type the following command in your terminal:
SSH -R 5900:localhost:5900 guest@janes-pc
The -R option determines the remote port forwarding, allowing Jane to access your laptop (localhost) by connecting a VNC client to port 5900.
Remote forwarding is useful when someone outside an organization needs to access an internal web server or when there is a need to avail an internal web application to the public internet.
- Dynamic Port Forwarding
This SSH tunneling makes a client a SOCKS proxy server. As a result, all the proxy server’s programs require configuration and reconfiguration when you are through with it.
As shown below, use the -D option to specify a dynamic port forwarding.
SSH -C -D 1080 laptop.
You can also use any number for the connection. However, the standard SOCKS port is 1080, and some programs may not work if other ports are in use.
SSH Tunneling Risks
The SSH protocol is susceptible to various malware to hide data breaches and attack sources channels. Maliciously obtained SSH keys have also been in use for network attacks. For instance, together with unmanaged SSH keys, SSH tunneling enables attackers to use stolen SSH keys for a private network from the public channels.
According to SSH Academy, these attacks can act as hideouts for the source of attack when hackers redirect attacks from systems and devices, In turn, the attackers can search for and exploit vulnerabilities without being detected.
Among the frequently carried out malicious activities are trying various log-in credentials and running attack tools against email and web protocol. Hence, it is essential for tunneling techniques to provide both secure remote access and control and security over the accessed network.
Reverse SSH Tunnel
A firewall on a router denies all connection requests or transfer requests that have no outgoing requests from reaching a remote machine. As a result, the only allowed connections are those requested by the remote machine, which creates a problem: the firewall rejects SSH connections initiated by a client and cancels your access to the remote machine when it resides behind NAT.
Reverse SSH solves this issue by simulating an SSH to the remote server. In this case, the remote machine listens on the local computer’s network port. It relays SSH connection requests to that port back to itself, which establishes a new connection between the local and remote computers. In other words, you use a tunnel inside a tunnel to connect a server, remote machine and your machine (see Figure 1).
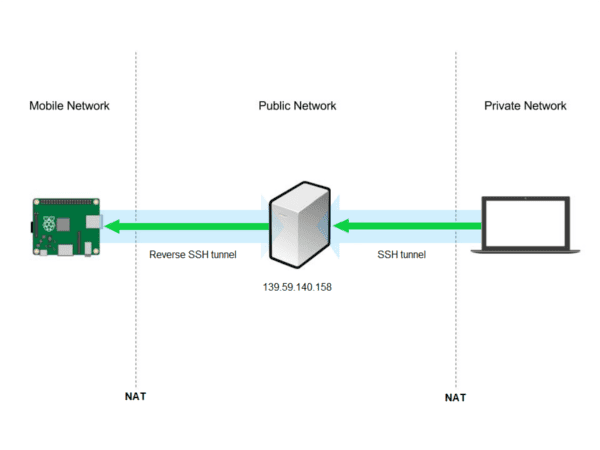
To create a reverse SSH tunnel, the machine in question first needs to open an SSH connection beyond the firewall and then include a -R tunnel at the remote machine’s connection port. On the man page, SSH -R description is: -R [bind_address:]port:host:hostport.
This specifies that the given port on the remote (server) host needs forwarding to the given host and port on the local side. This works by allocating a socket to listen to the port on the remote side. Whenever a connection goes to this port, the link happens over the secure channel, and a connection goes through to the host port from the local machine.
Step By Step Guide on Creating a Reverse SSH Tunnel on Linux
Before establishing a connection, ensure that you already installed SSH in your Linux/Ubuntu machine. If it is not, complete the following steps to enable SSH:
- Run the following command on the terminal to install the OpenSSH-server package:
$ sudo apt install OpenSSH-server
Enter the password when prompted and Y to continue with the installation.
- The SSH service will start automatically once the installation is complete. However, you need to verify that the installation was successful and that the service is actually running. To do this, run
$ sudo systemctl status SSH
This will display Active: active (running) if the installation was successful and the service is running. Press q to get back to the command line prompt.
- If you are using an Ubuntu machine, ensure that you open the SSH port using the following command
$ sudo UWF allow SSH.
Linux-based and macOS systems have pre-installed SSH clients. However, if you want to connect from a Windows machine, use the environment’s SSH client, for instance, PuTTY.
If the local computer has never accepted SSH connections before, start the SSH daemon (sshd) by running the following command on the terminal
$ sudo systemctl start sshd
To have the daemon start each time you boot your computer, run the following command
$ sudo systemctl enable sshd
How Does it Work?
- Connect to a remote server
To connect to a remote server, use the ssh command
$ ssh [your-account-login]@[server-ip]
- Create a Reverse SSH Tunnel
After you establish the connection, a person, say a system admin, on the remote server side, should run the following command on their machine:
ssh -fN -R 7010:localhost:23 username@yourMachine-ipaddress.
This connection request will ensure that SSH connection requests for port 7010 on your machine move to port 23 of the remote server.
- Make an SSH connection request from your machine to your machine
In this step, you will establish a connection at port 7000.
ssh username@localhost -p 7000
Your request will then find its way to the remote host. As such, use your account username on the remote server and password when prompted for these details.
You can also set up SSH keys to make it more secure to connect from the remote computer to the local computer. On the remote computer, type the following command:
$ ssh-keygen
which will prompt you for a passphrase.
It is advisable to use four words separated by symbols to make a robust passphrase and ensure that only those with the phrase can create an SSH connection to your computer without being challenged for a password. Additionally, you need to transfer the generated key to the local computer using the command ssh-copy-id username@localhost.
Conclusion
Network Address Translation (NAT) hides legitimate IP addresses by engaging undetectable secret IP networks that rely on unregistered IP addresses available to the internet. As such, NAT, which combines two networks, is located on a router and can be configured to advertise only one address for the entire network globally.
Reverse SSH Tunneling enables you to access remote machines behind NAT. For instance, you can access your office from home. Therefore, Reverse SSH Tunneling is a technique that enables you to SSH your Linux-based system that doesn’t have a public IP address.
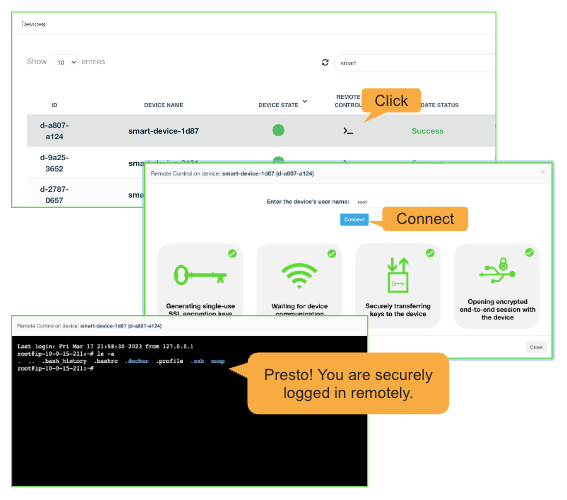
Connect today to JFrog Connect and access all your remote devices easily within seconds, with a safe and secure connection.
All Linux-based OS are supported, as well as all the SBC’s available such as: Raspberry Pi, Beaglebone, Jetson Nano and more.