OTA Updates for Remote Devices – Different Methods Explained
OTA Updates (Over-the-Air updates) is the term that’s used to describe the wireless delivery of new software, firmware or other data to remote devices that have difficulties being accessed physically.
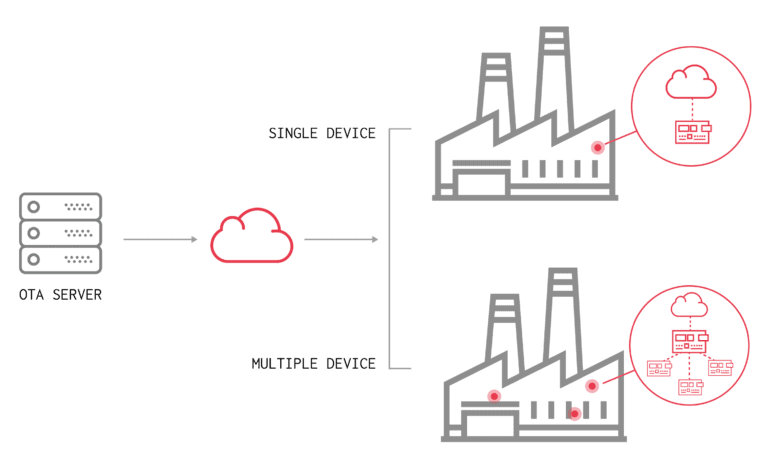
Typically, OTA updates are deployed by the OEM (Original Equipment Manufacturers) through wireless mediums such as the internet or local network to provide bug-fixes and feature upgrades.
Benefits of OTA Updates in IoT
Over-the-Air updates introduce a plethora of benefits when it comes to both developer-side and client-side.
Improved safety and compliance
Without having to recall the devices, the vendors can update the firmware on the devices to make sure that they are up-to-date and the latest known vulnerabilities are patched.
Maintenance cost reduction
By using OTA updates, the need to in-person maintenance is eliminated, thereby cutting the cost significantly and removing the need to provide field services.
Additional revenue streams
OTA updates can be used to add features that were not originally included in the devices, thereby increasing the value of the device, which can be used as a ‘paid-upgrade’.
Reduced operational cost
According to the Stout Risius Ross report, software issues account for 15% of the all-industry recalls. OTA technology streamlines software upgrades and fixes, and, as projected by IHS Automotive, is capable of saving businesses over $35 billion in operational costs.
Types of OTA Updates
When it comes to the perspective of the edge device/end user, OTA updates can be categorized into two main methods:
- Automatic OTA updates
These types of updates are deployed by the IoT device manufacturers themselves and are installed automatically on the devices depending on the configuration settings such as automatic update enable flags and schedules.
Examples: Android/Linux critical security patches etc.
- Manual OTA updates
For the updates that are not usually mandatory for the user such as operating system feature updates and UI updates, manual OTA updates are entertained. In this case, the end-user needs to launch the update-checker routine to check for updates and opt-in to install the updates if any are found available. Sometimes the firmware of the IoT device will notify the user of an available update, providing him the choice to whether and when to install it.
Examples: Linux kernel upgrades, UI updates, feature updates etc.
OTA update methods
OTA updates can be deployed through the internet, a local network (router), a dedicated gateway device or even it can be deployed by connecting to the individual hardware wirelessly.
Mainly, there are three major methods of OTA updates:
- Edge-to-Cloud OTA updates (E2C)
- Gateway-to-Cloud OTA updates (G2C)
- Edge-to-Gateway-to-Cloud OTA updates (E2G2C)
Edge-to-Cloud updates (E2C)
A connected device with a built-in microcontroller or a microprocessor receives OTA packages from a remote server. The package can include upgrades to both the microcontroller/microprocessor’s underlying hardware capabilities (FOTA) and updates to applications running on them (SOTA).
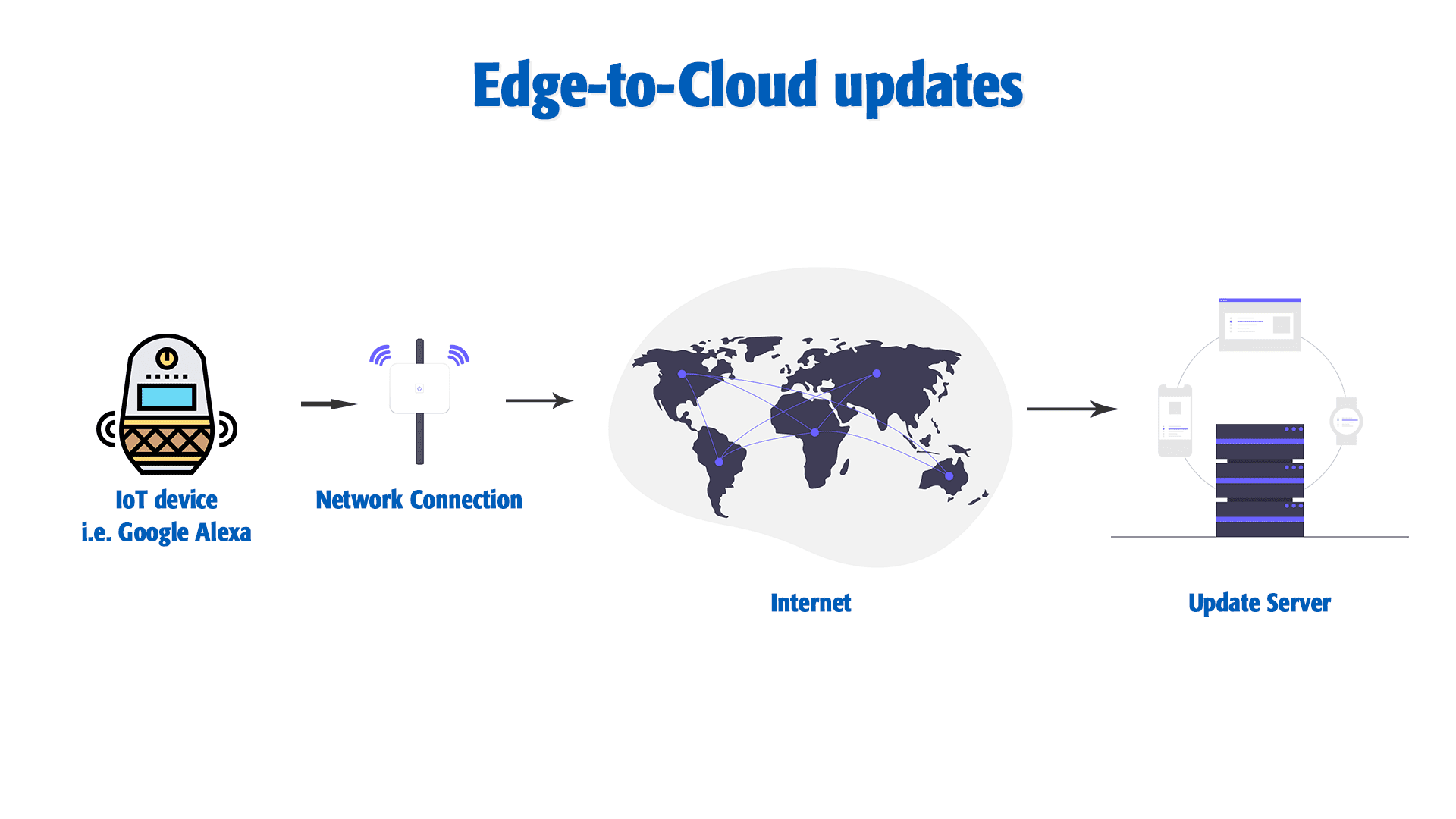
Google Home, Apple Siri and the Nest thermostat are some of the examples that use the E2C update method. Raspberry Pi and other single board computer-based systems are also capable of receiving updates in the same way using specialized services such as JFrog Connect.
Advantages of E2C OTA updates:
Allows the update of individual devices, making the entire fleet secure from corruption if the update process goes wrong
Disadvantages of E2C OTA updates:
Individual updates may take a lot of time if the fleet is larger. It should also be made sure that the correct device(s) is selected to deploy the update considering the working state of the device (i.e. if the device is in the middle of performing a critical task, the update should be deferred regardless of trying to force the update to be installed)
Gateway-to-Cloud updates (G2C)
A system featuring an Internet-connected gateway (for instance, a telematics system), which manages a set of local devices, and receives updates from a remote cloud-based server. The updates include newer versions of the installed software applications, the app’s host environment, and/or the gateway device’s firmware. In this case, the connected devices are not updated, rather the gateway itself.
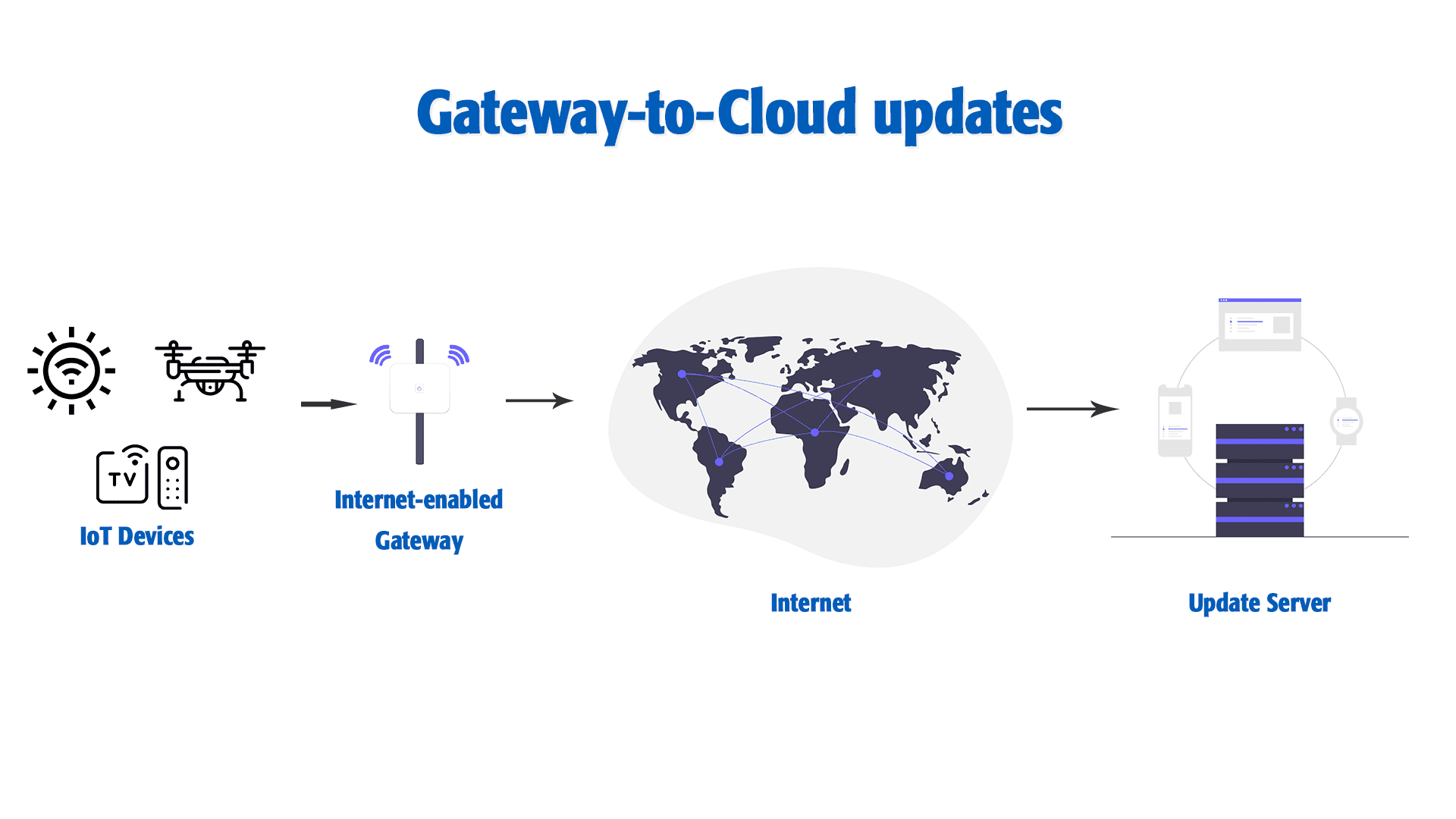
Some of the devices that use G2C OTA update methods are ATMs, remote energy monitoring systems and other banking and financial services such as kiosks. This OTA update method improves the security of the system as the devices are protected from outside attacks and vulnerabilities.
Advantages of G2C updates:
Since it’s the gateway that’s being updated and not the sensors or sensor nodes, the gateway can stay up-to-date, handling the communication and processing tasks.
Disadvantages of G2C updates:
When it comes to security/reliability, the gateway itself provides a single point failure which can render the whole system unusable if an OTA update goes wrong. IF the gateway cannot recover from a failed update attempt, the whole system can fail permanently.
Also, it can never be certain when the gateway device will be free for installing the update, since it manages multiple nodes and handles data coming from them continuously. When the update process is executed, it can certainly be expected to cause some disturbance to the functionality of the system in this case.
Edge-to-Gateway-to-Cloud OTA updates (E2G2C)
An Internet-connected gateway acts as a dispatcher, downloads updates from the cloud-based server, and then dispatches to another edge/gateway. In this case, the IoT devices should be able to execute the update by themselves. This method is used by devices such as field-based sensors such as temperature, humidity sensors, weather sensors and other industrial management sensor systems; the master device is capable of downloading and distributing updates corresponding to the slave/other devices in the network and those devices are capable of installing their updates on their own.
Advantages of E2G2C:
This is one of the best possible architectures that allows safe, modular OTA updates. This reduces the risk to the entire fleet since each node connected to the gateway can handle their updates by themselves or the gateway can directly execute updates on the edges, protecting the fleet if one or more updates go wrong. The system will still be able to function with the corrupted nodes.
Disadvantages of E2G2C:
Just like G2C mentioned above, E2G2C also has the same single-point-of-failure when it comes to failed updates. In this case, the nodes may or may not also be able to have the ability to let the gateway know of the update status in an event of corrupted update, thereby leading to a mismatch in update schedule.
Drawbacks and concerns related to OTA updates
If a certain manufacturer does not enforce the security of their devices’ OTA update routines such as enforcing checksum calculation, attackers can intercept the OTA updates and exploit those vulnerabilities to hack into the remote devices. This poses a huge security risk and can expose sensitive data on the remote device to a third party.
Typical OTA update steps
When deploying an update, be it OTA firmware (FOTA) or any other update such as from simple file replacement to complete firmware upgrade, the update process should contain the following steps;
- Pre-update preparation – to stop a service, remove a file handle that exists to prevent data corruption, install dependencies etc.
- Update process – replacing files, updating services and applications, executing update routines etc.
- Post-update clean-up – to make sure that there are no stray files/programs that are leftovers from the update process to both conserve space and resources
- Rollback routine – in case if an update goes wrong such as connection interruption, there should be a fallback routine to rollback the changes that are being made to ensure that the device is able to function as it was before the update was initiated
With these four main steps; followed carefully, can ensure a successful deployment of OTA updates.
Best practices for OTA updates, followed by industry professionals
When designing/developing and deploying a system, the following key points are a must to be addressed:
Incorporating an OTA mechanism from day-one: adding OTA update routines to the firmware greatly improves the chance of introducing feature updates and bug fixes at a later time, during the production and even after deployment.
Progressive development approach: following a progressive development approach, it can not only make the development more reliable, but also streamlines the development of new features.
Prioritized updates: To make sure that the functionality of the running devices is not interrupted, the updates must be prioritized so that the devices that are idling get the update first; and installs them.
Atomic updates with rollback: instead of pushing large updates, micro updates can make the update process more gradual and the migration from the older version a swift task.
Backing up current configuration
Management platform: using a central management platform, the previous updates must be logged and managed to track the changes upto the date.
Security: the OTA updates in deed should be secure to ensure the edge device’s security and the other connected devices that reside in the same network.
Authentication
Integrity: updates must not be corrupted during transmission.
Using JFrog Connect for deploying OTA updates
For your convenience, we have developed an easy-to-use, feature-rich Update tool which can be used as a regular update tool to replace/update files, execute remote update commands and deploy container updates as well.
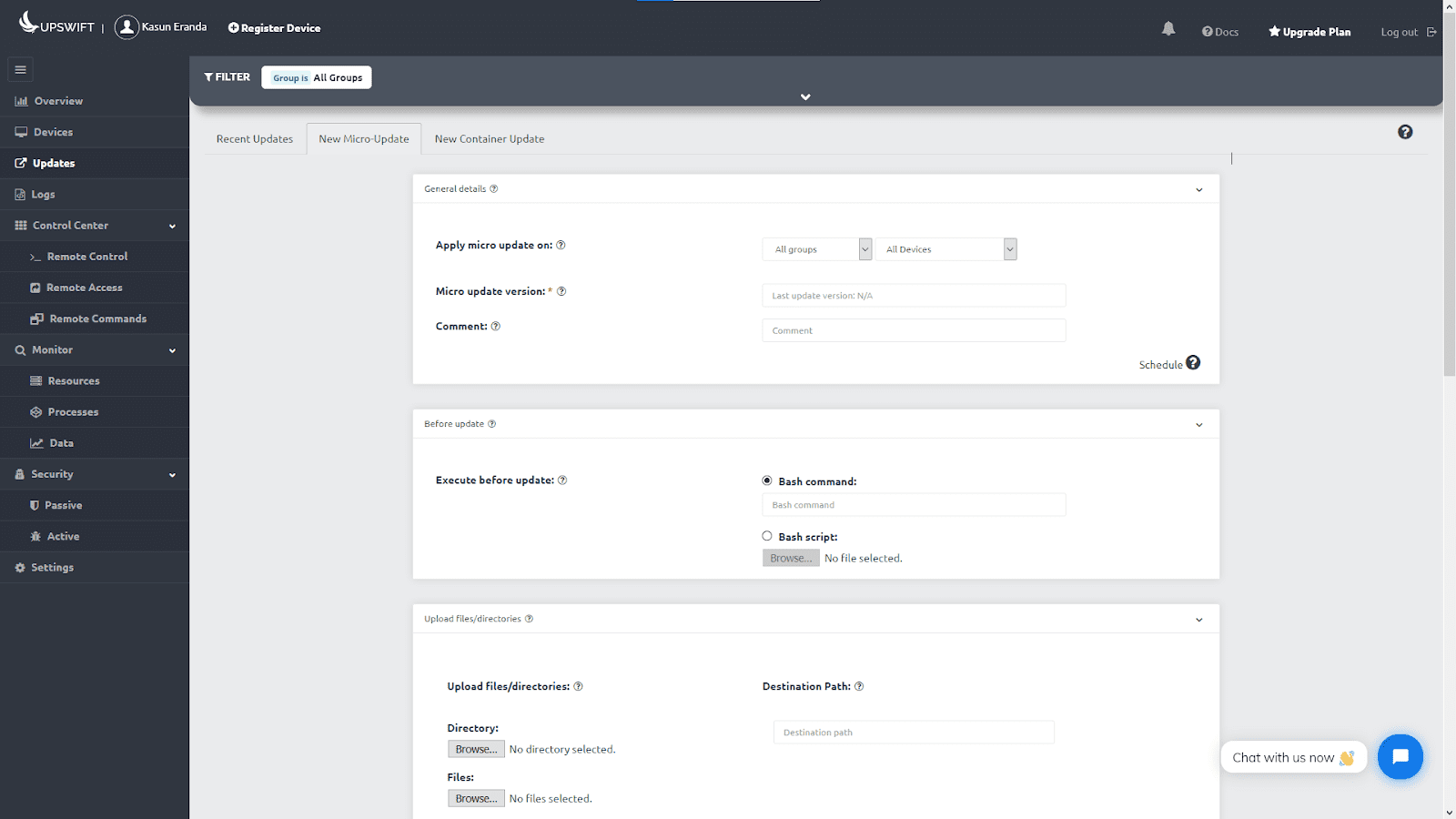
We also have prepared straightforward, simple guides you can follow on how to use the Updates tool to maximize the efficiency of OTA update deployment, while ensuring a safer and reliable update process.
JFrog Connect is not just another OTA update platform; it’s so much more. We offer you every key feature you’ll need to manage your Linux IoT devices remotely including remote secure control access and remote device monitoring.
Haven’t tried JFrog Connect yet? Click here and sign up to learn more!



