How to Spend Less Time Fixing CVE’s
One of the most common complaints of SCA tools from developers is that they generate far too many results, requiring them to fix lots of vulnerabilities that don’t in reality pose any risk. This wastes time, money and lowers productivity.
How much time and money can you save if you only focused on fixing what you need to… rather than simply “fixing everything?”
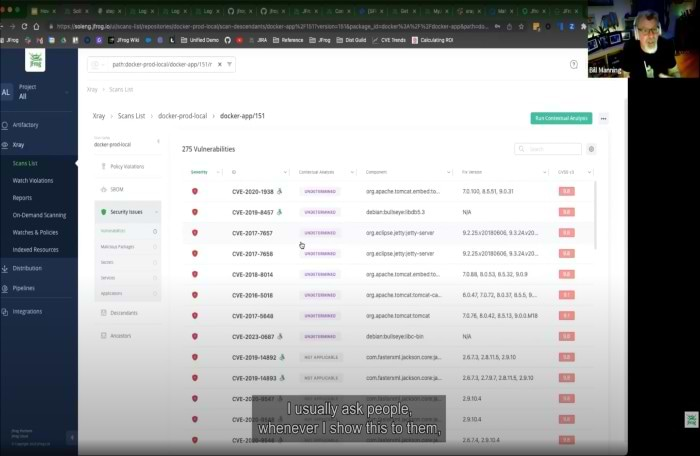
JFrog’s Contextual Analysis scans the container indicating whether a CVE is applicable (or not) to that specific container image. We provide concrete, and actionable remediation options that take into account relevance to your build, while providing proof points
How much time and money can you save if you only focused on fixing what you need to… rather than simply “fixing everything?”
JFrog’s Contextual Analysis scans the container indicating whether a CVE is applicable (or not) to that specific container image. We provide concrete, and actionable remediation options that take into account relevance to your build, while providing proof points
1.
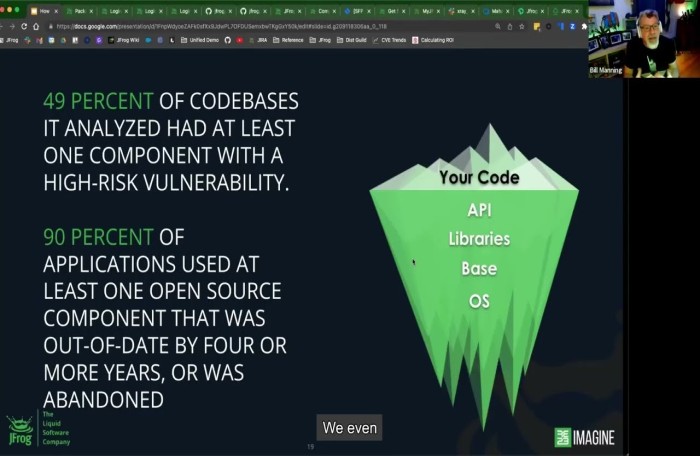
Operation Risks to pay attention to in open-source components
Let’s look a the four main risk areas of an open-source component
2.
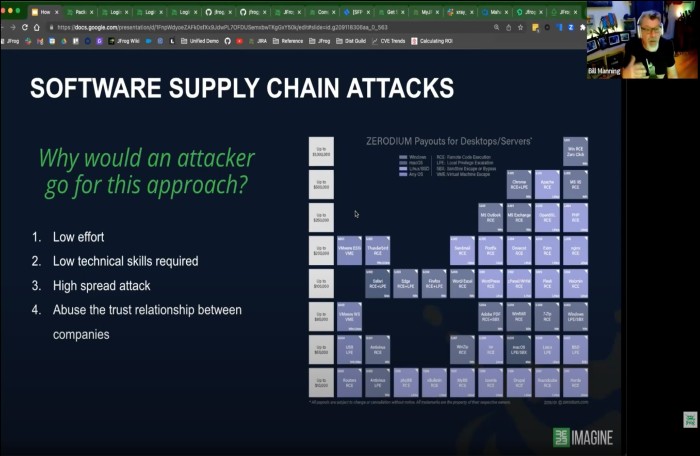
Why would a attacker go after your software supply chain?
The four reasons that make your supply chain easy to penetrate and the cost of the damage in $ and time spent
3.
The modern approach of fixing your vulnerabilities
Let’s look at the true cost of infinitely fixing vulnerabilities and a more modern approach to intelligently identify and fix vulnerabilities
4.
Not all CVE are threats
Let’s look at a better system that intelligently identifies ONLY CVEs that are applicable to your software and IF they are worth your time remediating