Definition
npm (node package manager) is the default package manager for the JavaScript & typescript popular programming languages, functioning as one of the world's largest online software registries for public and private code packages and provisioning the command-line interface (CLI) client used by developers to interact with that registry to automate the process of discovering, installing, managing, updating, and publishing project dependencies.
Overview of npm
npm is fundamentally a two-part system: a massive online registry and a client-side command-line tool. It automates the process of managing reusable code modules and is critical for both open-source collaboration and enterprise-scale development.
Key functionalities of npm center on automating the package lifecycle. The npm install command resolves dependencies and downloads packages, while npm publish uploads new or updated packages to the registry. The tool manages versioning to ensure dependency compatibility and tracks package information within the project’s package.json file.
How to Get Started with the npm Registry and CLI
The public npm registry serves as the primary distribution hub for the JavaScript and typescript ecosystems, while the npm CLI is the developer’s direct gateway to accessing and managing those packages.
The most common public npm registry is https://www.npmjs.com/
Node.js and the CLI Client
Since npm is bundled with Node.js (the javascript runtime engine), installing Node.js automatically installs the npm CLI client. Once installed, developers can manage and access packages from the registry. For initial setup and configuration details, see Get Started with npm.
Installation and Configuration
The installation process typically involves downloading and running the Node.js installer for the target operating system, which includes the npm CLI. After installation, the CLI is available directly from the command line. By default, the CLI will download packages from the public repository of npmjs. In order to configure a private or self-hosted registry, users must update configuration file .npmrc to direct the CLI to the correct registry URL and handle authentication, just as npm CLI connects to JFrog Artifactory using .npmrc.
Creating and Managing package.json
package.json is the manifest file for all Node.js projects. It centrally defines metadata such as the project’s name, version, description, main entry point, and crucially, all of its required dependencies. Managing this file is critical for ensuring a project’s portability and reliable reproduction across multiple environments.
Dependency Management Fundamentals
Effective dependency management is the cornerstone of scalable JavaScript development. npm provides granular control over how a project tracks and consumes its external code modules.
Types of Dependencies
The package.json file categorizes dependencies based on their role in the project lifecycle:
dependencies: Packages required for the application to run in production.devDependencies: Packages only required for local development, testing, and building such as test runners and linters.peerDependencies: Dependencies an application expects its consumers to already have. This is common for plugins or add-ons.optionalDependencies: Dependencies the application attempts to use if present, but will tolerate their absence without failing the installation.
Semantic Versioning (SemVer)
Semantic Versioning (SemVer) is a three-part version string (MAJOR.MINOR.PATCH) that dictates how versions are incremented based on the changes they introduce. A MAJOR version change indicates incompatible API changes, MINOR indicates backward-compatible new features, and PATCH denotes backward-compatible bug fixes. npm uses prefixes such as ^1.0.4, ~1.0.4 in package.json to define acceptable version ranges based on SemVer rules.
Overrides and Resolution of Conflicts
Dependency conflicts commonly arise when packages introduce incompatible SemVer ranges, leading to a complex or unstable dependency tree. npm’s overrides field in package.json explicitly forces the package manager to use a specific version for any dependency in the graph, overriding potentially problematic sub-dependencies. This provides granular control to resolve conflicts and mitigate security vulnerabilities in deeply nested dependencies.
The package-lock.json file is critical for ensuring deterministic builds by recording the exact dependency tree used during the last successful installation. This file details the versions, sources, and Subresource Integrity (SRI) hashes of every package, including transitive dependencies, irrespective of the semantic versioning ranges specified in package.json. When a subsequent user or CI/CD process runs npm install, the presence of package-lock.json forces the installation of these precise versions, effectively bypassing package version resolution and mitigating depedency issues often caused by conflicting version requirements across a large project dependency graph.
How to Build and Publish npm Packages
A JavaScript package is usually a directory containing a package.json file. The process of making this package available to others involves careful preparation and publication to a registry.
Preparing a Package for Distribution
Preparation ensures that a package is correctly structured for consumption. This involves defining the main entry points, the expected runtime environments, and all necessary metadata. A well-prepared package clearly communicates its purpose, dependencies, and constraints to other developers.
Setting Up Essential Files
Essential files for distribution include the README.md (which documents usage and purpose), the LICENSE (which defines legal terms for reuse), and the CHANGELOG (which details version history and major changes). Crucial metadata, such as the SemVer version and author information, are defined in package.json.
Versioning and Releasing Packages
Package versioning must adhere to the rules of SemVer. npm simplifies version management through the npm version command, which automatically updates the version number in package.json and creates a corresponding Git tag. A release is officially executed by running npm publish after the version has been tagged and committed.
What are the Top npm Security Challenges?
The Node Package Manager (npm) is a central point for JavaScript development, making it a prime target for Application Security (AppSec) compromises, leading to sophisticated supply chain attacks. The core security challenges stem from the massive scale of the registry and the inherent trust developers place in packages.
Securing JavaScript dependencies in the Software Supply Chain is a critical AppSec concern. The primary attack vectors leverage vulnerabilities or malicious code injection within the package consumption model.
Key npm security challenges include:
1. Account Takeover and Package Poisoning Attacks
Attackers compromise the accounts of trusted package maintainers (often via sophisticated phishing that bypasses basic 2FA) to take over their public packages and inject malicious code into popular, widely-used libraries. This direct attack on a software’s source is a severe supply chain attack that immediately compromises downstream users.
A recent example in Sept 2025, involved the largest attack in npm history based on compromising a maintainer’s account to inject malware into libraries like debug and chalk. Shortly afterwards, the “Shai-Hulud” worm attack compromised over 500 additional packages by self-replicating, stealing credentials, such as npm and cloud tokens, and then automatically continuously spreading by publishing malicious versions using the compromised accounts.
These incidents highlight the extreme threat posed by compromised developer credentials and automated malicious payloads, underscoring the need for rigorous scanning and security gates at every stage of the software supply chain..
2. Dependency Bloat and Transitive Risk
The average modern application relies on hundreds or even thousands of transitive dependencies (packages installed by the packages you explicitly installed). A vulnerability or malicious code in any single dependency deep within this hidden chain is automatically executed during the build process, creating a massive, opaque attack surface. Developers often lack visibility into this deep dependency graph, making manual risk assessment virtually impossible.
3. Malicious Run-Scripts and Post-Install Hooks
npm packages can contain scripts that automatically execute during the installation process, specifically via lifecycle hooks like postinstall. Attackers leverage this legitimate feature to execute arbitrary code (e.g., harvesting environment variables, stealing credentials, or deploying malware) immediately upon the developer running npm install. This grants attackers execution authority on the developer’s local machine, potentially facilitating lateral movement.
4. Typosquatting and Dependency Confusion
Typosquatting involves attackers publishing packages with names very similar to popular libraries (e.g., react-domm instead of react-dom). Dependency Confusion exploits weaknesses in organizational package management by registering a public package with the same name as a private one. Developers or automated build systems can accidentally pull the malicious public version when attempting to resolve dependencies, causing a profound security breach.
What are Best Practices when Using npm?
Implementing a robust set of best practices minimizes security risks, improves collaboration, and enhances the reliability of Node.js applications across the Software Development Lifecycle (SDLC).
Managing Dependencies Effectively
Dependency management is not passive; it requires proactive tools. Teams must utilize lockfiles (package-lock.json) to enforce deterministic builds and reduce the attack surface created by transient dependencies. Automated Software Composition Analysis (SCA) scanning should be integrated early in the process to detect known vulnerabilities and license compliance issues before a package is even integrated into the application.
Using npm Scripts for Automation
The scripts field in package.json should be leveraged as the primary mechanism for standardizing build, test, and development tasks across a project. This consistency is a core principle of DevOps. By standardizing commands, developers ensure that common tasks are executed predictably across all environments, from local machines to Continuous Integration servers.
Keeping Packages Updated and Secure
Regularly updating packages is critical for security, as newer versions often contain patches for known vulnerabilities. However, updates must be controlled to prevent breaking changes. Teams should automate updates within safe SemVer boundaries and integrate automated security gates into their pipelines to ensure that newly installed dependencies do not introduce high-severity vulnerabilities.
How Does JFrog Integrate with npm?
The JFrog Platform provides a robust, centralized solution that secures and optimizes the usage and distribution of npm packages throughout the entire development pipeline, extending enterprise-grade control to the JavaScript ecosystem, with extensive integration with npm repositories
The JFrog Platform, centered around JFrog Artifactory, functions as a universal Software Artifact Repository. It provides a single source of truth for all binary artifacts, including npm packages. This central hub is critical for DevOps practices, enabling seamless automation, and improving the efficiency and speed of CI/CD processes.
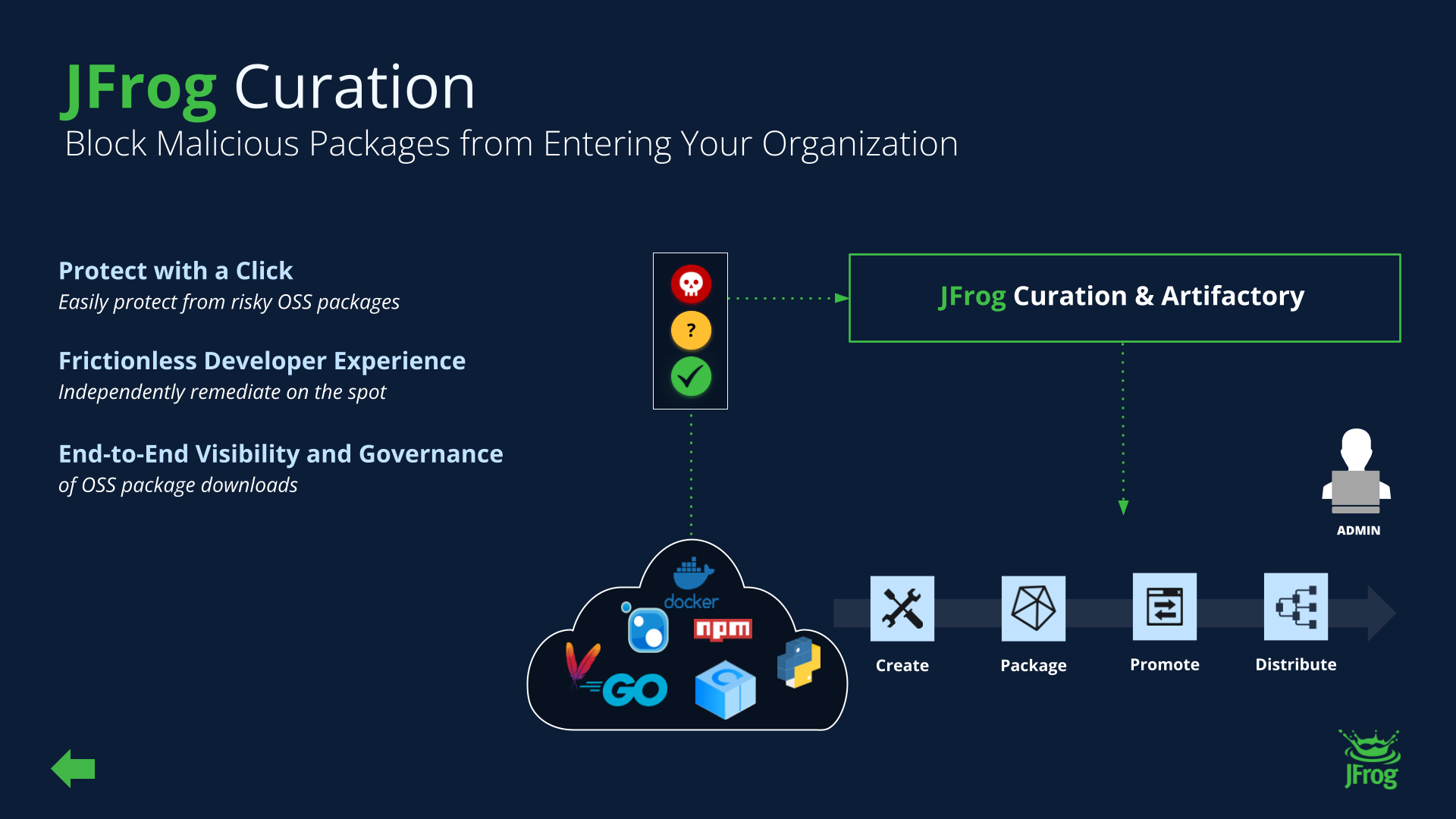
JFrog Curation directly addresses the security challenges inherent in npm’s massive public registry. It automatically scans third-party open-source packages for security vulnerabilities, malware, and license compliance issues in advance and before they are downloaded to a developer’s workstation or integrated into a build. By leveraging a contextualized security model, JFrog helps filter and block malicious or non-compliant packages from entering your environment, thus mitigating risks like package poisoning, typosquatting, and the exploitation of transitive dependencies. A good example of this is the npm “Manifest Confusion” attack, where JFrog Artifactory protected local repositories by indexing and storing each package according to its actual package.json information and not based on the manifest metadata file.
By integrating Artifactory’s advanced artifact management with JFrog’s security capabilities, organizations transform the volatile public npm ecosystem into a trustworthy, compliant Software Supply Chain.
The JFrog platform enables you to take a more proactive approach to managing and securing OSS packages coming into your development environment and secure your JavaScript supply chain against the latest npm attacks. To see for yourself, please take an online tour, schedule a personal demo or Start a Free Trial of JFrog curation at your convenience.




