Curation
Keep Malicious Code Out of Your SDLC
Automatically enforce software policies on open source packages, IDE extensions, AI/ML models, and third party downloads so only trusted components reach your Developers
Build FastDon’t let curation of malicious packages slow down your release velocity |
Stay SecurePrevent vulnerabilities from ever reaching your development environment |
Remain CompliantEstablish a single source of truth for all software artifacts |
THE CHALLENGEImplementing security controls slows down development Your developers download countless unvetted third-party components like open-source packages and IDE extensions directly from public sources. Current security controls often drastically slow down development, yet without a proactive checkpoint, each download is an unchecked entry point for malicious code, non-compliant licenses, and vulnerabilities to enter your software supply chain. |
THE SOLUTIONEnhance security while maintaining your release velocity JFrog Curation proactively secures your software supply chain at its entry point by automatically validating every open-source package, IDE extension, tool, and AI/ML model your developers try to use. This check instantly enforces your corporate policies on every request, replacing slow manual reviews with instant, automated approvals. It blocks non-compliant software whether it is being requested from a public registry or already in your cache, ensuring you maintain development velocity. |
Block Risky Components Before They Reach Your Developers
“With JFrog Curation, we’re truly shifting left because we’re now able to block malicious packages and risky components before they even enter our cloud instance, easing the minds of our security leadership team.”
Head of Software Engineering, IT
JFrog Customer: Leading Healthcare Provider, EMEA
THE RESULT
Build Fast, Stay Secure and Remain Complaint
Establish Consistent Security Policy
Ensure absolute consistency by automatically applying a single security policy to every third-party software request. This automated approach replaces manual, unreliable developer self-policing and provides a complete, auditable trail required for compliance.
Prevent Fires, Don’t Fight Them
Move from a costly reactive posture to a proactive defense. Curation automatically blocks malicious and non-compliant packages at the point of entry. This eliminates threats before they are ever downloaded, preventing expensive remediation at a later stage.
Build Without Bottlenecks
End developer waiting games. Automate security approvals to instantly replace tedious, manual review gates. Your teams gain velocity and can deliver faster, knowing every component they use is already pre-vetted and compliant.
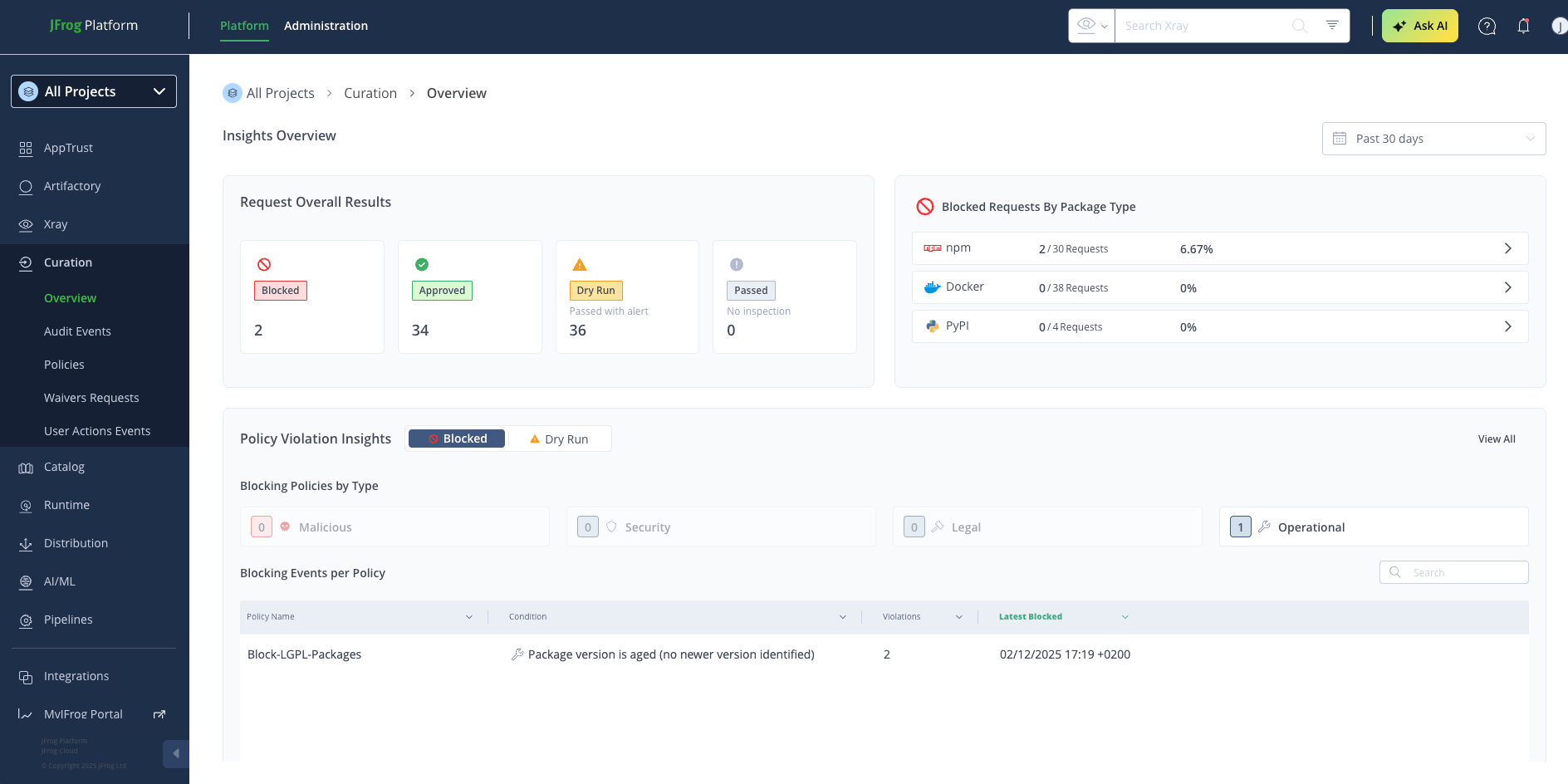
Figure 1: Insights Overview Dashboard: Gain instant visibility into all open-source package requests, including what was approved, blocked, or flagged by your policies
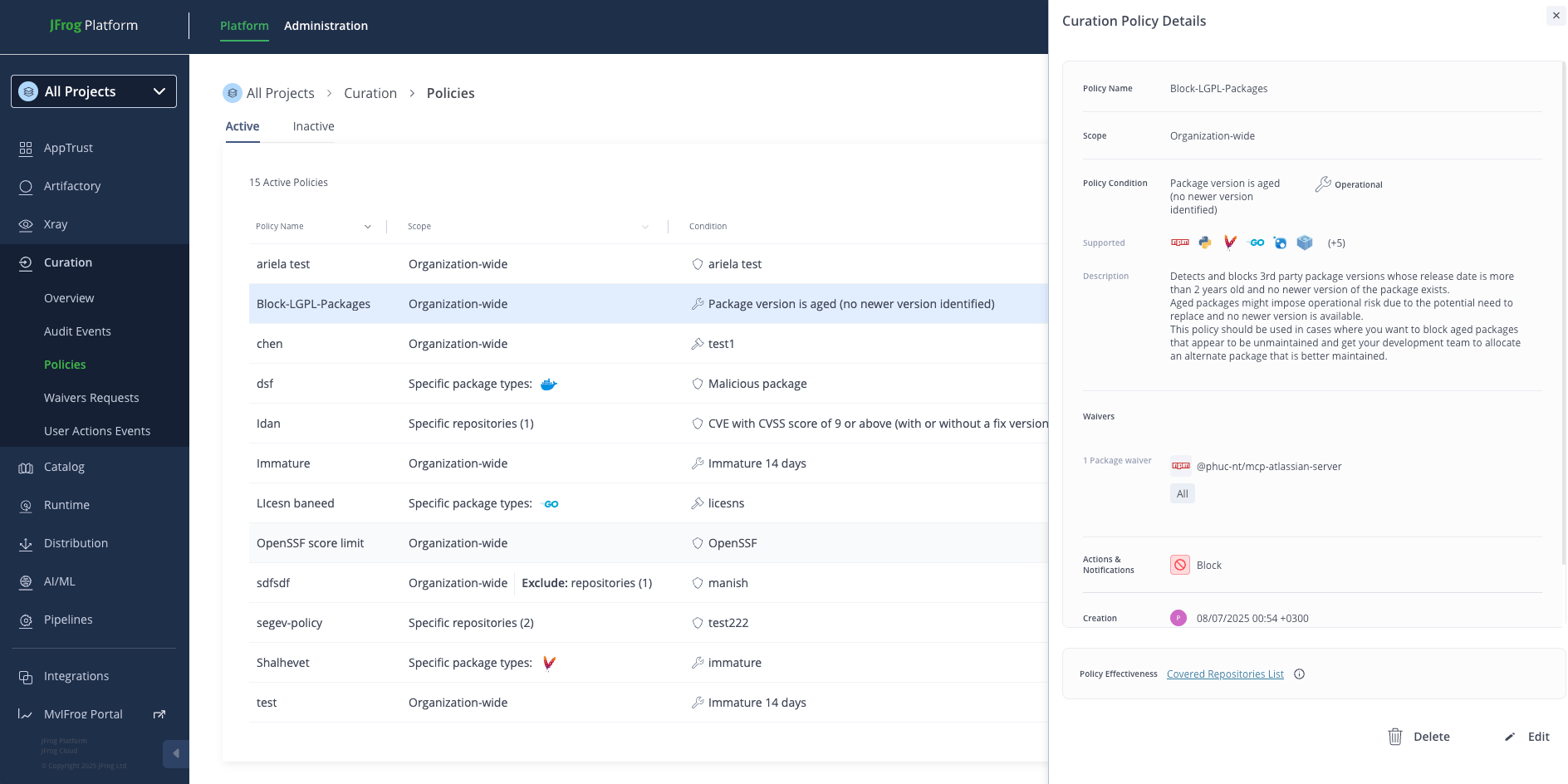
Figure 2: Set and Review Automated Policies: Block specific risks and enforce security standards across your organization
Key Features and Benefits
| Key Features | Benefits |
| Automated policy enforcement | Gain a consistent, 100% enforceable security standard that automatically blocks malicious packages and license risk, freeing your team from slow, error-prone manual approvals. |
| Centralized audit log | Simplify compliance audits by instantly providing a complete log of every package request, block and approval. |
| Recommended package alternatives | Maintain developer productivity by automatically offering a compliant version of a blocked package, preventing “blocked workflows” and work interruptions. |
| Block immature packages | Reduce the risk of zero-day attacks by blocking newly published packages, before a threat is publicly discovered. |
| Block risky cached packages | Validates all cached packages against the latest policies, protecting the organization from new vulnerabilities found in previously “safe” components. |
The Leading Platform for Software Supply Chain Management, Security & Governance
“Our Curation deployment provides effective and efficient supply chain protection. We were able to shut down recent provider attacks in mere minutes once discovered and the control has proven 100% successful since.”
Sr. Cybersecurity Executive
Leading Financial Services Company
The JFrog Platform is the single source of truth for over 7,000 companies. JFrog embeds trust and control directly into the software development lifecycle, giving your teams the confidence to accelerate releases and deliver secure trusted applications at speed.
For more information about how you can gain all the benefits of JFrog Curation, feel free to explore the JFrog Platform, schedule a one-on-one demo or visit our help center at your convenience.