Definition
A Secure Software Development Lifecycle (SSDLC) is a disciplined approach to embedding security throughout the software development process. It extends the traditional Software Development Lifecycle (SDLC) by integrating well defined security requirements at all stages of development from pre-coding, coding, the build , testing to deployment and maintenance.
Overview of SSDLC
SSDLC is a structured process that proactively addresses security concerns throughout the entire software development process, rather than treating security as an afterthought. This approach ensures that security is an inherent part of the application’s design, development, and deployment.
Definition and explanation of SSDLC
The Secure Software Development Lifecycle (SSDLC) refers to the integration of security activities and considerations into every stage of the conventional software development lifecycle. Its primary goals include:
- Defining security requirements.
- Performing security testing.
- Conducting code reviews.
- Managing vulnerabilities to build inherently more secure applications.
- Minimizing security defects and exposures early in the development process.
Key principles of SSDLC
The evolution of the Secure Software Development Lifecycle (SSDLC) is a direct response to two critical factors: the ever-growing complexity of modern software systems and a rapidly escalating cybersecurity threat landscape. In earlier approaches, security considerations were frequently relegated to the final stages of the Software Development Lifecycle (SDLC). This “bolt-on” security approach often resulted in the discovery of vulnerabilities late in the development cycle, necessitating costly, time-consuming, and reactive fixes.
The current shift towards a robust SSDLC fundamentally acknowledges the inefficiency of reactive security. It champions the principle that embedding security practices, tools, and mindsets from the very inception of software design and throughout every subsequent phase is far more efficient and ultimately effective.
This transition signifies a crucial pivot for organizations, moving their security posture from merely reacting to threats after they emerge to proactively building resilience and security into the software from its foundation. This mirrors the broader industry movement towards DevSecOps, which fully integrates security as a shared responsibility across development, operations, and security teams.
Why is SSDLC important?
Implementing an SSDLC is crucial for developing robust and secure applications in today’s digital environment. It addresses the growing need to protect sensitive data and systems from sophisticated cyber threats.
Benefits of implementing SSDLC
Implementing an SSDLC offers numerous benefits for organizations developing software:
Reduced Security Vulnerabilities: A primary benefit of integrating security throughout the development lifecycle is a significant reduction in the overall number of security vulnerabilities present in released software. By implementing proactive detection methods and emphasizing early remediation, flaws are identified and addressed when they are simplest and cheapest to fix. This “shift-left” approach means that security issues are caught long before they become embedded deep within the code, drastically decreasing the attack surface and improving the inherent robustness of the software.
Lower Remediation Costs: Fixing security defects earlier in the software development lifecycle translates directly into dramatically lower remediation costs. When vulnerabilities are discovered during the design, coding, or early testing phases, the effort required to correct them is minimal, involving simple code changes or design adjustments. In stark contrast, identifying and patching critical flaws after software has been deployed to production can incur substantial expenses related to emergency hotfixes, extensive retesting, potential downtime, and even the cost of managing a breach, making early detection a significant cost-saving measure.
Improved Compliance: Adopting a robust SSDLC significantly contributes to improved compliance with a wide array of regulatory standards and industry best practices. By embedding security controls and processes directly into development workflows, organizations can systematically address requirements from frameworks such as GDPR, HIPAA, PCI DSS, and NIST. This proactive integration makes demonstrating adherence during audits far more straightforward and less burdensome than attempting to retroactively apply security measures, ensuring that legal and industry mandates are met from the ground up, rather than being an afterthought.
Enhanced Customer Trust: A visible commitment to secure software development, underscored by a strong SSDLC, invariably leads to enhanced customer trust and stronger brand reputation. In an era where data breaches are common headlines, customers are increasingly wary of the security of the products and services they use. By consistently delivering applications with fewer vulnerabilities and demonstrating a proactive posture towards security, organizations prove their dedication to protecting customer data and privacy. This builds confidence, differentiates the product in the market, and fosters loyalty among a security-conscious user base.
Prevention of Costly Breaches: Perhaps the most critical benefit of a mature SSDLC is the effective prevention of costly security breaches and the severe reputational damage they inflict. By systematically reducing vulnerabilities throughout the software’s creation, the likelihood of successful exploitation by malicious actors is significantly diminished. This proactive risk mitigation safeguards sensitive data, intellectual property, and critical operations. Avoiding breaches not only protects financial assets that would be spent on incident response, legal fees, and regulatory fines, but also preserves invaluable customer trust and brand integrity, which are often far more difficult and expensive to restore.
Role of SSDLC in mitigating security risks
An SSDLC plays a vital role in mitigating application security risks by identifying and remediating vulnerabilities early in the development process. This “shift left” approach ensures that security flaws are detected when they are easiest and cheapest to fix, significantly reducing the attack surface of the final product.
How JFrog helps enable a secure software development lifecycle
Embedding security into all phases of the SSDLC
To effectively secure the software development process, security must be integrated into each phase of the SSDLC, from planning to deployment and beyond.
What are the phases of an SSDLC?
The SSDLC typically mirrors the phases of the traditional SDLC (e.g., requirements, design, development, testing, deployment, maintenance), but with specific security activities embedded within each. For example, security requirements are defined during the planning phase, and threat modeling is conducted during design.
Specific security practices for each phase
Here is a table with each stage of development and a description of the type of security that should be applied to that particular phase.
| Phase | Description |
| Design | Incorporate secure design principles. Perform security architecture reviews and data flow analysis. |
| Development | Implement secure coding guidelines. Conduct peer code reviews for security flaws. Utilize static application security testing (SAST). |
| Testing | Execute dynamic application security testing (DAST). Perform penetration testing and vulnerability scanning. |
| Deployment | Ensure secure configuration of deployment environments. Implement continuous security monitoring post-deployment. |
| Maintenance | Conduct regular security audits and updates. Implement robust incident response plans. |
What tools and technologies enhance security in an SSDLC?
There are a number of key tools that support SSDLC implementation across each phase of development:
Static Application Security Testing (SAST) tools: SAST tools are pivotal in the early phases of the SSDLC, analyzing source code, bytecode, or binary code without executing the application. They pinpoint potential security vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure direct object references directly within the code base. By integrating SAST into developer workflows and CI/CD pipelines, security flaws can be identified and remediated much earlier, preventing them from propagating into later stages.
Dynamic Application Security Testing (DAST) tools: DAST tools come into play during the testing phases of the SSDLC, assessing the application from the outside by executing it and simulating attacks. They actively probe the running application for vulnerabilities that might not be evident from code analysis alone, such as authentication flaws, session management issues, and server misconfigurations. DAST provides a black-box view of the application’s security posture, complementing SAST by finding issues in the deployed environment.
Software Composition Analysis (SCA) tools: SCA tools are essential for managing the security risks associated with open-source and third-party components, which often comprise a significant portion of modern applications. These tools automatically identify all open-source libraries and dependencies used in a project, scanning them against comprehensive vulnerability databases. SCA helps prevent the introduction of known vulnerabilities, ensures license compliance, and enables proactive management of the software supply chain.
Vulnerability Scanning tools: Vulnerability scanning tools are critical across multiple phases of the SSDLC, offering comprehensive coverage by identifying weaknesses in various layers of the software ecosystem. Beyond application-specific testing, these tools often scan infrastructure, networks, and deployed systems for known vulnerabilities and misconfigurations. Their continuous and broad-spectrum assessment capability ensures that security gaps are identified not just in the custom code but also in the underlying environment and dependencies, providing a holistic view of potential risks.
What are best practices for implementing an SSDLC?
Adhering to best practices ensures a robust and effective SSDLC, including adopting a recognized framework, implementing secure practices and continuously monitoring potential vulnerabilities.
Adopting the SLSA framework
Adopting SLSA (Supply-chain Levels for Software Artifacts) or similar frameworks helps with implementation of an SSDLC as it provides a verifiable, measurable approach to securing the outputs of the development process. While SSDLC emphasizes embedding security throughout every phase, from design to deployment, SLSA offers concrete standards and attestations that directly prove the integrity and trustworthiness of software applications and the artifacts used to produce them.
Implementing secure coding practices
Secure coding practices are fundamental to SSDLC, as developers must rigorously adhere to the following guidelines:
- Practice Input Validation and Sanitization
- Implement Proper Error Handling and Logging
- Adhere to the Principle of Least Privilege
- Manage Secrets Securely
- Protect Against Common Web Vulnerabilities, if and when relevant
- Utilize Secure Libraries and Frameworks
- Conduct Secure Code Reviews
Performing thorough security testing and code reviews
Comprehensive security testing, including SAST, DAST, and manual penetration testing, is crucial, supplemented by:
- Regular code reviews by security experts or peers help identify subtle security flaws that automated tools might miss.
- This includes reviewing open-source dependencies using Software Composition Analysis (SCA) to identify known vulnerabilities.
Ensuring continuous monitoring and vulnerability management
Post-deployment, continuous monitoring of applications for new vulnerabilities and anomalous behavior even after the software has been deployed is critical for long term success. This usually involves:
- Utilizing security information and event management (SIEM) systems.
- Implementing proactive vulnerability management processes to promptly address newly discovered threats or CVEs.
Building an effective DevSecOps culture
Integrating security into DevOps workflows, or adopting a DevSecOps approach, is a natural extension and enhancement of the SSDLC, emphasizing automation and collaboration.
Integration of security into DevOps workflows
DevSecOps seamlessly integrates security into every stage of the DevOps pipeline. This means:
- Security checks, tests, and policies are automated.
- They are applied continuously from code commit to production deployment.
- This integration accelerates development cycles while enhancing security.
Collaboration between development, operations, and security teams
A core tenet of DevSecOps and a successful SSDLC is breaking down silos between development, operations, and security teams.
- Shared responsibility and collaborative efforts ensure security is a collective priority.
- This leads to faster issue resolution and a more secure software supply chain.
Automation and tooling for streamlined security processes
Automation is key in DevSecOps. Automated security testing, compliance checks, and vulnerability remediation workflows:
- Accelerate feedback loops.
- Ensure consistent application of security policies.
- Tools for continuous integration and continuous delivery (CI/CD) pipelines, artifact management, and vulnerability scanning are essential.
The role of JFrog in implementing an SSDLC
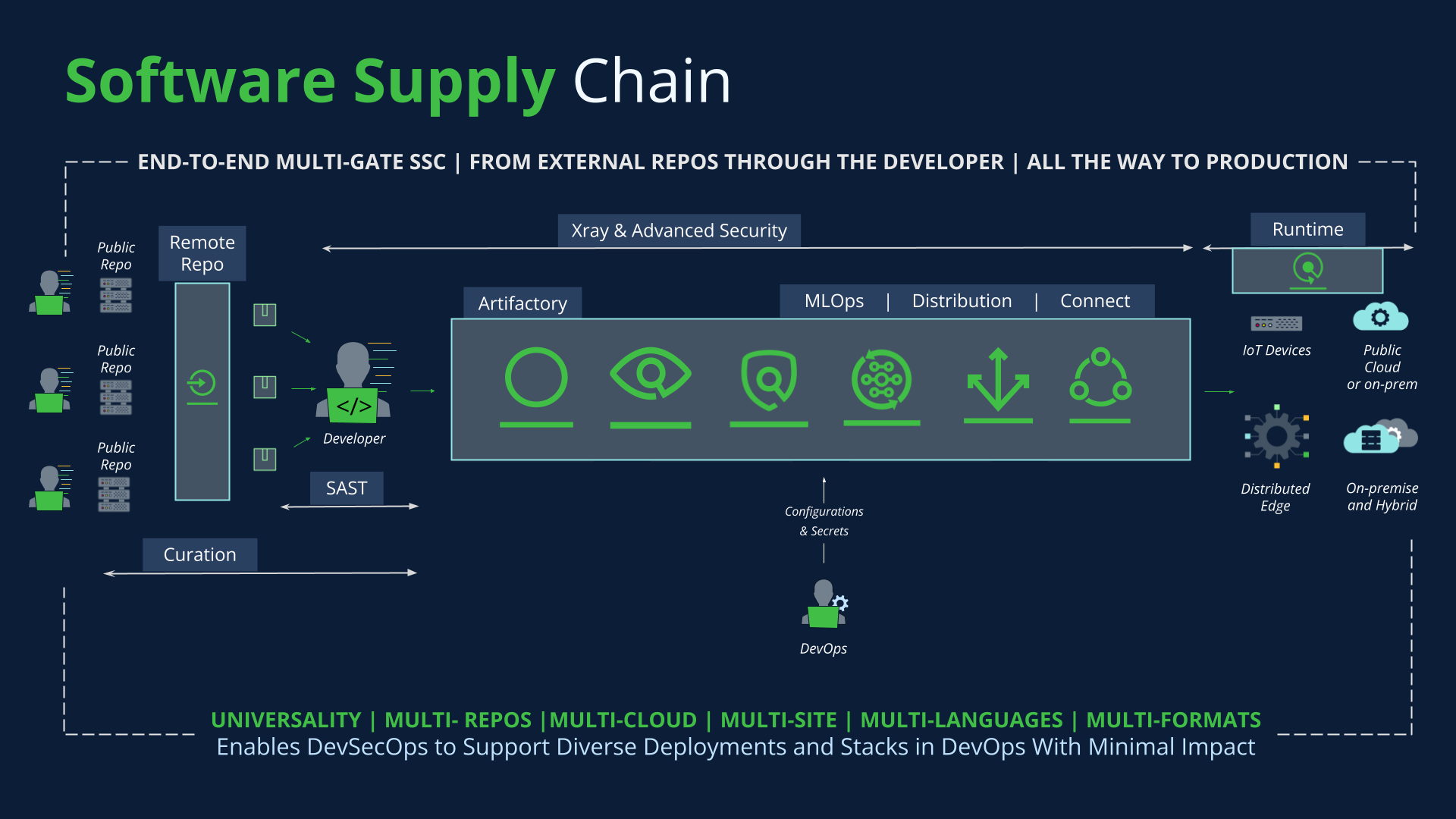
The JFrog Platform simplifies implementation of a Secure Software Development Lifecycle by providing integrated solutions for artifact management, vulnerability analysis, and secure release orchestration. By shifting security left and automating processes, JFrog helps organizations achieve a comprehensive SSDLC, ensuring higher quality, more secure software delivered faster.
The JFrog Platform plays a pivotal role in supporting a robust Secure Software Development Lifecycle (SSDLC) by integrating essential security and management capabilities directly into the software supply chain. At its core, JFrog Artifactory facilitates the secure management of all software artifacts, from binaries and dependencies to Docker images, ensuring that every component used in development and deployment is versioned, traceable, and centrally controlled.
Complementing this, JFrog Xray provides deep scanning capabilities, automatically identifying known vulnerabilities (CVEs) and license compliance issues within these artifacts and their transitive dependencies. This early and continuous security analysis helps to “shift left” on security, preventing insecure components from ever entering the build or deployment process.
For “shifting right”, JFrog Runtime enables DevOps and Security teams to monitor applications in real time to identify, prioritize, and remediate security incidents based on actual risk and image integrity. By ensuring the integrity and security of binaries throughout the entire pipeline, the JFrog Platform helps organizations reduce their attack surface, improve compliance, and ultimately deliver more secure software.
JFrog’s unified platform integrates seamlessly with your existing security infrastructure, enabling effective access governance across repositories, builds, and pipelines. For more information, take a virtual tour, or set up a one-on-one demo or start a free trial at your convenience.