Use Case: Security Tools Consolidation
A holistic approach ensures continuous security across the supply chain
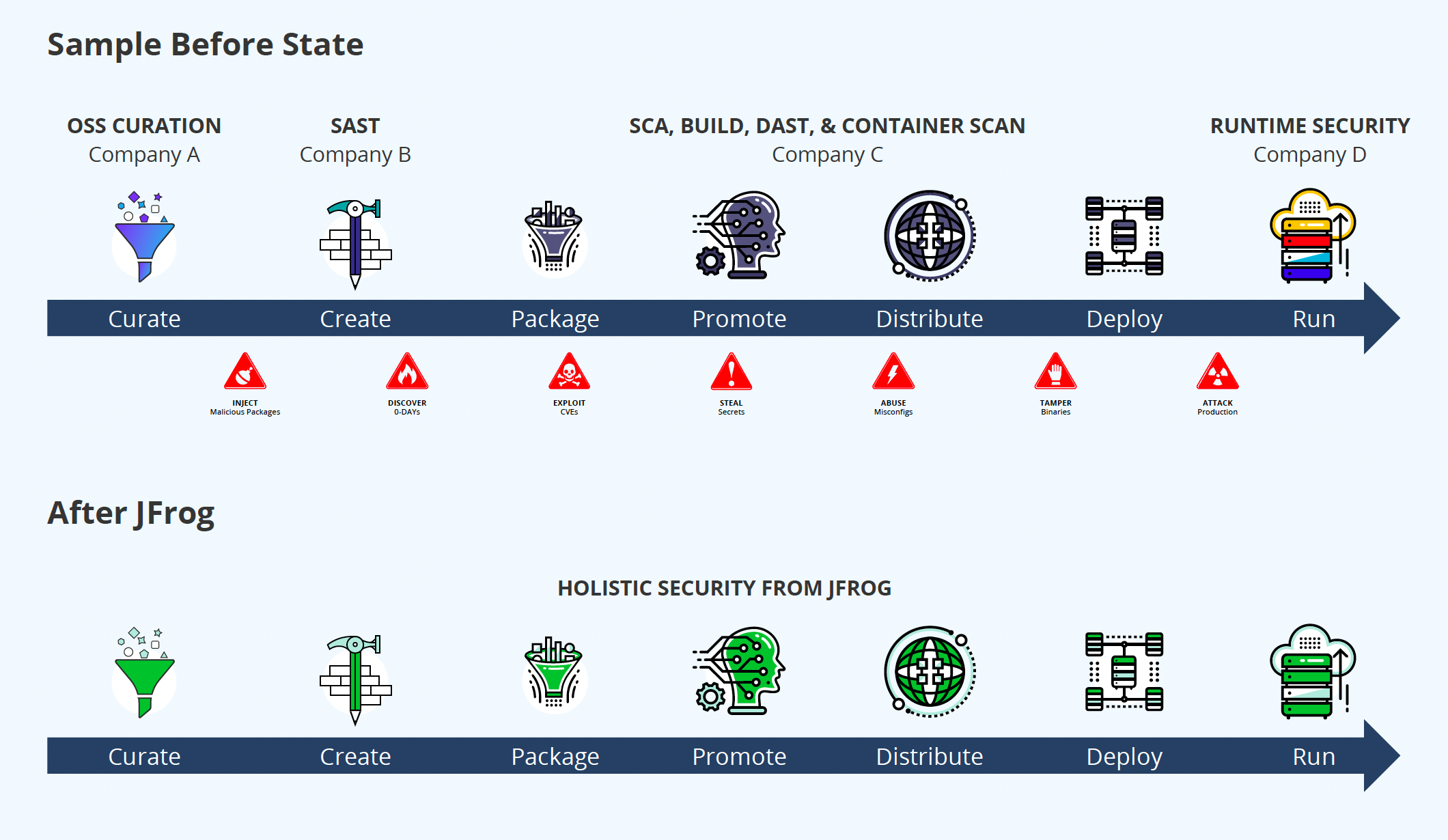
BACKGROUND
Recent security events such as Log4j have highlighted just how vulnerable software supply chains are to attacks from malicious actors. In 2022 alone there were over 26,000 new CVEs reported. Most CVEs are unintentional vulnerabilities, but the JFrog Security Research team discovered 1460 new intentionally malicious packages in the same time span.
Organizations are moving aggressively to ensure the integrity of their software supply chains. Between SAST, DAST, SCA and other types of application security tools it’s possible for businesses to have a dozen different tools in place to ensure secure releases.
More point solutions however, don’t guarantee a comprehensive approach to application security. A glut of security tools creates its own issues:
- Integration overhead and missing blindspots
- Flooded with security issues to track across different tools
- Prioritization and remediation overhead
- Manual security efforts
These issues negatively impact developer velocity and security risk. Ultimately, Security and DevOps teams are forced to try and apply policies consistently using multiple applications without a single pane of glass into the overall security of their component ecosystem.
SOLUTION
JFrog eliminates point security solutions in favor of a holistic binary focused approach, bolstered by a leading research team, that ensures continuous security across the supply chain. By shifting left security efforts and applying them consistently throughout the software lifecycle, organizations are confident that the software they’re releasing is safe and secure.
Key capabilities supporting security tool consolidation with the JFrog Platform:
- Enhanced SCA, Malicious Package Detection, IaC Security, Secrets Detection, Services and Application Exposures Detection
- Security IDE plugins, CLI Tools, Docker Desktop extension, and Git repository scanner
- Contextualized analysis to prioritize vulnerabilities with developer friendly remediation
- Automated SBOM creation (and export) in SPDX, CycloneDX, VEX standard formats
- Support for the leading OSS package and technology types (and growing)
- Policies to fail builds, block promotion, and trigger workflows
- Curate an approved set of packages for developers to use
- Application security that integrates with popular CI/CD and DevOps tools
- Signed pipelines and builds
By focusing on five core tenets — Developer Focus, Efficiency, Accuracy, Coverage, and Prioritization — JFrog delivers unbeatable protection from all potential supply chain threats whether self-hosting or making use of public clouds.
“Something that’s going to scan everything in that central repository of truth, automatically, with zero customization required, that’s really, really powerful.” Larry Grill, DevSecOps senior manager, Hitachi Vantara
RESULTS
Fast Remediation
Find and fix issues fast. JFrog customers resolved Log4j issues in hours and days, not weeks and months.
Cost Savings
Upwards of hundreds of thousands of dollars per year across license, maintenance, and integration costs.
Proactive Prevention
Automated policies block vulnerabilities and malicious packages before they enter your ecosystem.
Security Consistency
Ensure security policies and processes are applied consistently across all teams, projects, and developers.