JFrog vs. Checkmarx: The Binary Difference
Securing the Software Supply Chain from code to runtime.
Key Highlights:
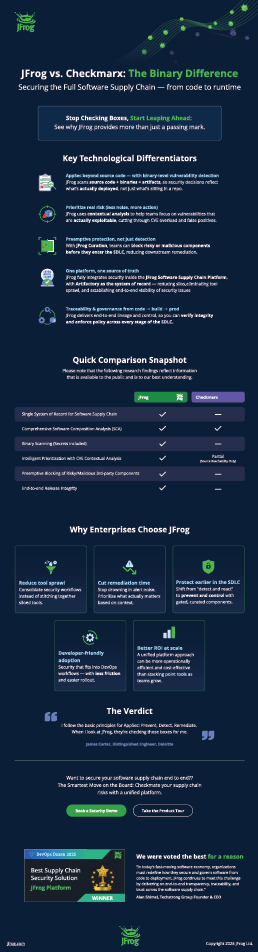
- Beyond Source Code: The core argument is that traditional tools like Checkmarx focus primarily on Static Application Security Testing (SAST)—scanning source code. JFrog highlights that this creates “blind spots” because attackers often target the compiled binaries and third-party dependencies that SAST might miss.
- Binary-Focused Security: JFrog emphasizes its ability to scan binaries, containers, and artifacts (the actual components being deployed). It argues that “the binary is the reality,” providing a more accurate security posture than scanning intent (the code) alone.
- Contextual Analysis: Similar to the Black Duck comparison, JFrog touts its Contextual Analysis feature. This determines if a vulnerability in a dependency is actually reachable and exploitable within the specific configuration of the application, significantly reducing developer “noise” from false positives.
- Integrated Platform vs. Point Solution: JFrog is presented as a “DevOps-native” platform where security is built into the artifact repository (Artifactory). In contrast, Checkmarx is depicted as a “bolted-on” security tool that can lead to silos between security and DevOps teams.
- Comprehensive Coverage: The page compares specific capabilities, noting that while Checkmarx is strong in SAST, JFrog provides a “Single System of Record” for the entire supply chain, including secrets detection, infrastructure-as-code (IaC) scanning, and even AI/ML model security.
DOWNLOAD THE INFOGRAPHIC
Or click on the image to download the infographic.