Enhancing IoT Deployment Security Under the Cyber Resilience Act
The rise of connected devices has brought significant progress in various sectors, but it also increases vulnerability to cybersecurity risks. As global regulatory authorities tackle this critical issue, the European Union leads the way with the EU Cyber Resilience Act (CRA), which focuses on enhancing the security of embedded devices. Although the CRA is still pending approval from the European Commission, the suggested guidelines indicate a major shift in cybersecurity standards for equipment manufacturers in Europe.
To meet these evolving requirements, we are pleased to announce a new feature in JFrog Connect, a key component of the JFrog Platform for trusted software supply chain management from developer to device. Keep reading here to learn more about these timely developments.
What is the Cyber Resilience Act?
The Cyber Resilience Act (CRA) requires companies to adopt secure development practices, provide regular updates and patches, and proactively manage vulnerabilities. These measures are intended to create a safer digital landscape, protect user data, and ensure the reliability and integrity of digital products and services in the EU market. Compliance with the CRA is crucial for companies operating in or targeting the EU market, ensuring they remain secure, competitive, and trusted.
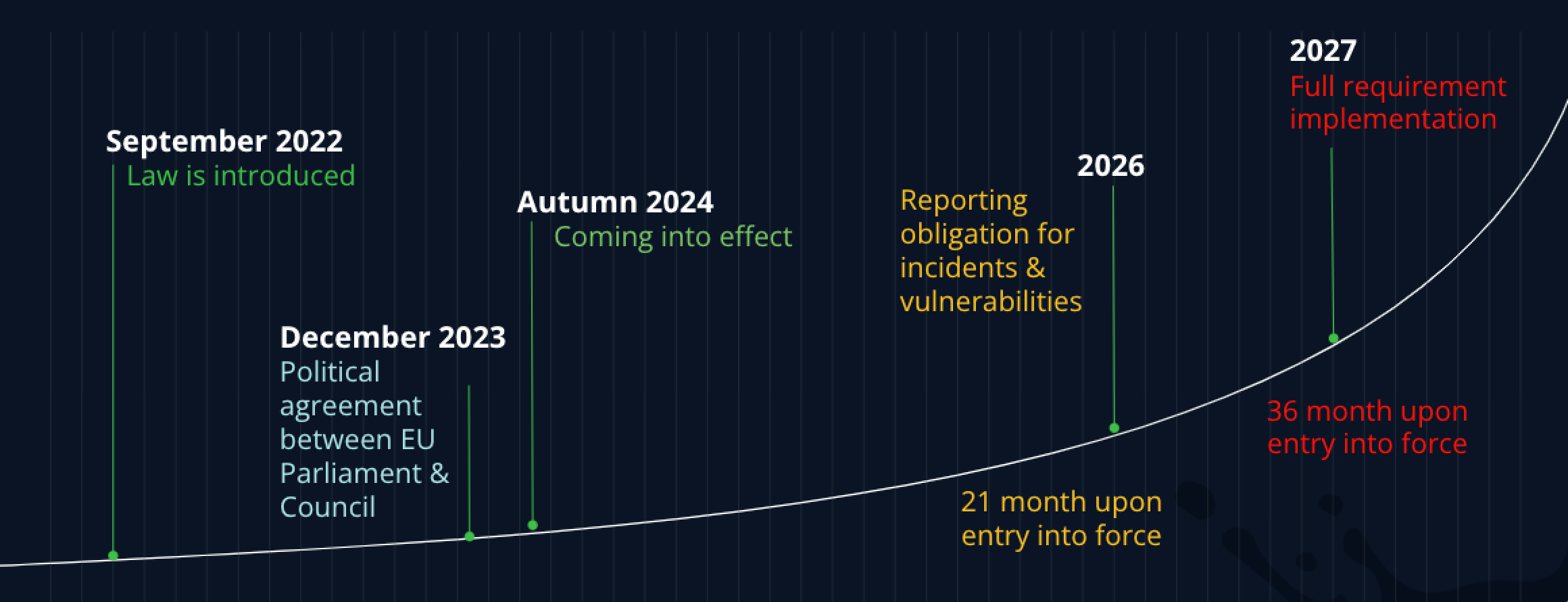
Why the Cyber Resilience Act is needed
The regulation tackles two primary issues. First, many products suffer from poor cybersecurity or receive insufficient security updates. Second, both consumers and businesses struggle to identify which products are secure and to configure them in a manner that safeguards their cybersecurity.
To address these problems, the CRA has three main objectives:
- Reduce vulnerabilities in digital products
- Enhance protection for users and hold manufacturers accountable
- Create a unified cybersecurity framework across the EU
Who is affected by the CRA?
The law affects manufacturers, distributors, and importers of products with digital elements in the EU, including hardware and software that can connect to networks, either directly or indirectly.
To enforce compliance, the regulation will impose fines between €5 to €15 million or 1-2.5% of global annual turnover, depending on various factors such as the nature, severity, and duration of the violation, cooperation with authorities, and previous non-compliance incidents.
CRA requirements
Most of the requirements of the Cyber Resilience Act can be divided into two categories: vulnerability handling and security by design.
Vulnerability Handling
Companies must implement robust measures for handling vulnerabilities throughout the product lifecycle:
- Early Detection & Blocking of Exploitable Vulnerabilities
- Automated Vulnerability Management
- Software Bill of Materials (SBOM)
- License Compliance
- Operational Risk Management
- Comprehensive Security Governance
- Enhanced Reporting & Documentation
- Proactive Security Measures
Security by Design
Products must be designed, developed, and maintained with cybersecurity as a core consideration (incl. regular updates & patches):
- Secure Development Lifecycle
- Risk Assessment & Management
- Minimize Attack Surfaces
- Secure Default Configurations
- Robust Authentication & Data Protection
- Continuous Vulnerability Monitoring & Timely Updates
- Notification and Documentation
- Audit Trails and Security Advisories
Additional requirements include: the disclosure of vulnerabilities and security incidents in a timely manner, secure and reliable update flow/warranty on vulnerabilities, and centralized reporting of incidents or vulnerabilities (ENISA).
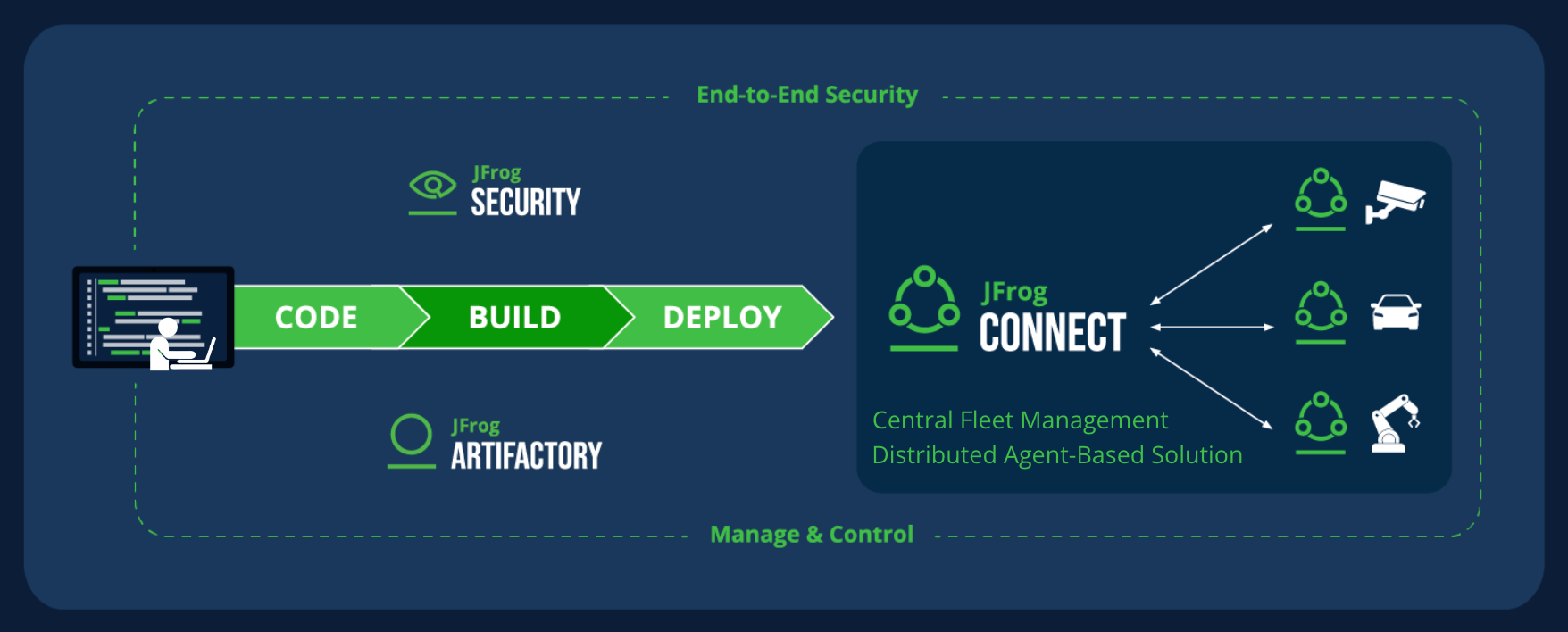
Enhancing IoT deployment security with JFrog
To meet the evolving needs of our industry, we’re excited to introduce a powerful new capability within JFrog Connect. This update enhances functionality by offering deeper insights into vulnerabilities affecting deployments, particularly for IoT or edge devices.
Now integrated directly with JFrog Xray, Connect enables continuous monitoring of CVE severity throughout the deployment lifecycle, aligning with the EU’s Cyber Resilience Act requirements for embedded devices.
The JFrog Security Suite
The JFrog Platform is a unified Software Supply Chain Management solution to ensure secure and controlled software development from source code to runtime. It provides a single source of truth for software development, bridging the gap between developers, operations, and security teams to protect the entire software supply chain – all from one unified platform. JFrog’s Security solutions support the CRA and are delivered as cloud, multi-cloud, self-hosted, air-gapped.
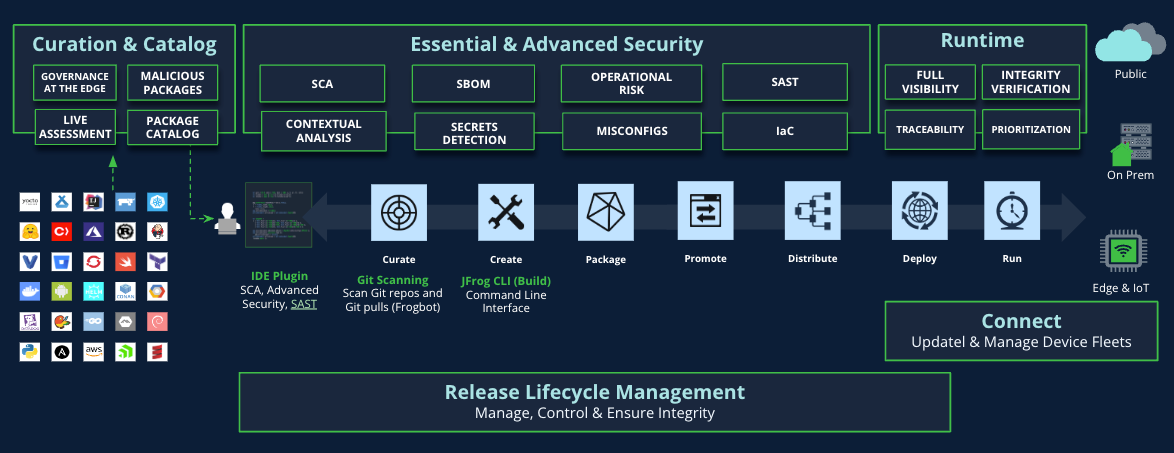
JFrog Curation & Catalog
- Enforce automated security policies to block unsafe OSS components from entering the software supply chain, ensuring only trusted components are used.
JFrog Essential & Advanced Security
- Easily identify, prioritize, and remediate vulnerabilities, deliver secure automated updates, and ensure timely reporting via SBOMs
- Implement secure coding practices with advanced application security testing and robust vulnerability management, including contextual analysis, SAST, and security exposure scanning
JFrog Release Lifecycle Management
- Create immutable release bundles early in the SDLC to establish secure development practices and streamline timely updates and security patches
- Gain full visibility into the release process with comprehensive documentation, including risk assessments and audit trails
What’s on the roadmap
In the future, JFrog Connect will also integrate with Runtime, granting users visibility into the processes running on a given device, so they can understand the real impact of any vulnerabilities present. For instance, if the vulnerability is found on binaries that are not running, then the impact will be considered low. However, if they are running as a process, the impact will be considered high. This detailed context will help boost developer efficiency, reserving their time and focus for what matters most.
The JFrog Platform integrated security solutions provide comprehensive risk assessments and maintain detailed audit trails and documentation, helping businesses comply with CRA regulations and ensure accountability.
By leveraging the JFrog Platform and its Security Suite, you can seamlessly integrate security into your development workflows, ensuring compliance with the Cyber Resilience Act while enhancing the overall security of your software supply chain.
Request a demo to learn more about how the JFrog Platform can help you meet the requirements.