

Target Key Threats:
Secure Exploitable Vulnerabilities
Improve software release efficiency and security by pinpointing accuracy on critical AND relevant CVEs you must fix. Our secrets detection capability ensures your sensitive information remains protected.
- Focus on software vulnerabilities that pose critical and relevant risks.
- Streamline vulnerability prioritization and accelerate application development.
- Scan to determine code and configuration violations.
- Meticulously scan binaries and code that expose sensitive information, such as API keys and passwords.
Experience the JFrog Platform
Google
GitHub
Or sign up with email
Choose Your Experience
Platform Tour
Free Trial
For performing a full review or
POC of JFrog’s capabilities.
POC of JFrog’s capabilities.
Complete Your Details
Certified by:



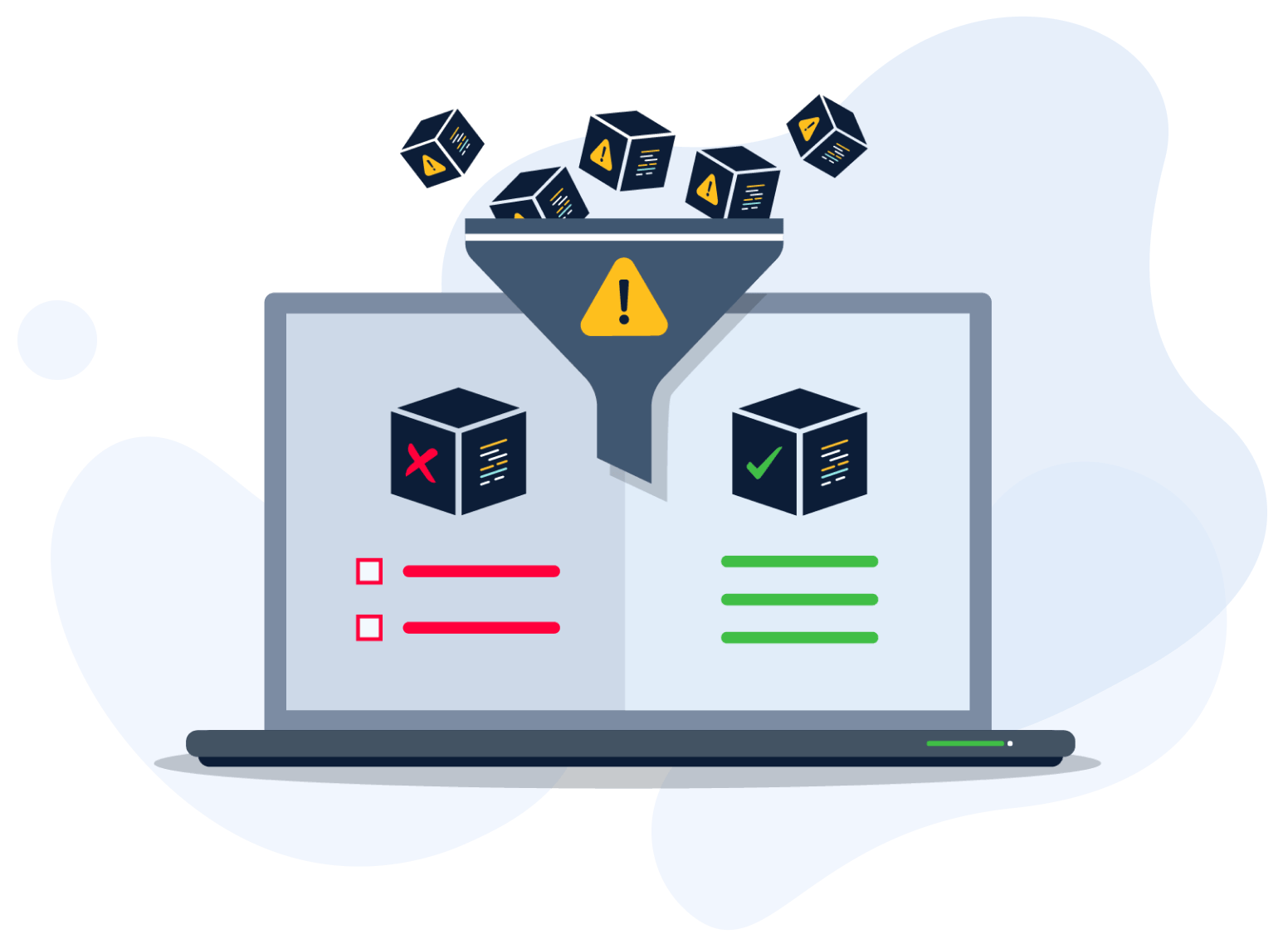
Improve software release efficiency and security by pinpointing accuracy on critical AND relevant CVEs you must fix. Our secrets detection capability ensures your sensitive information remains protected.
- Focus on software vulnerabilities that pose critical and relevant risks.
- Streamline vulnerability prioritization and accelerate application development.
- Scan to determine code and configuration violations.
- Meticulously scan binaries and code that expose sensitive information, such as API keys and passwords.
Our Partners:
See How Contextual Analysis and Secrets Detection
Allow You to:
- Target only the vulnerabilities that genuinely threaten your software.
- Prioritize critical security issues to optimize your efforts.
- Discover how our Secrets Detection rigorously secures exposed sensitive data.

Prioritize, Resolve, and Secure
- Prioritize Actionable Threats: Focus resources on vulnerabilities that directly impact your security posture.
- Resolve Issues Efficiently: Quickly address critical vulnerabilities with targeted remediation strategies.
- Secure Sensitive Data: Protect your most valuable assets from unauthorized access with advanced secrets detection. Detect and protect secrets in both source code and binaries.
Experience Contextual Analysis and
Secrets Detection with a Free Tour
Already Familiar? Skip Tour, Start Trial!





