Linux Permissions: Dos and Dont’s
By Harel Erez, Enterprise Solutions Lead @JFrog
1月 27, 2022
5 min read
In this blog I will give you some hints and ideas about some best practices, approaches, and “Dos and Dont’s”, you should consider when working with Linux file permissions.
What are Linux File Permissions?
In Linux, file permissions, attributes, and ownership control the access level that the system processes and users have to files. This ensures that only authorized users and processes can access specific files and directories.
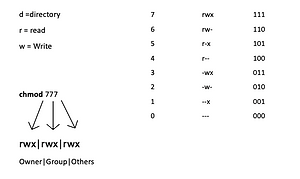
For each Linux file, we have several permissions that can be changed by the chmod command, as can be seen below.
Manage Linux File Permissions via chmod command
One effective way to use chmod is to provide the permissions you wish to give to the owner, group, and others as a three-digit number. The leftmost digit represents the permissions for the owner. The middle digit represents the permissions for the group members. The rightmost digit represents the permissions for the others.
The digits you can use and what they represent are listed here:
· 0: (000) No permission.
· 1: (001) Execute permission.
· 2: (010) Write permission.
· 3: (011) Write and execute permissions.
· 4: (100) Read permission.
· 5: (101) Read and execute permissions.
· 6: (110) Read and write permissions.
· 7: (111) Read, write and execute permissions.
Each of the three permissions is represented by one of the bits in the binary equivalent of the decimal number. So 5, which is 101 in binary, means read and execute. 2, which is 010 in binary, would mean the write permission.
Using this method, you set the permissions that you wish to have; you do not add these permissions to the existing permissions. So if read and write permissions were already in place you would have to use 7 (111) to add execute permissions. Using 1 (001) would remove the read and write permissions and add the execute permission. Chmod can be used also with +/- signs for example chmod +x which would give the file execution permissions, I would not recommend using this method.
Up until now, we explained what permissions are and how can we set them. We also have permission per user/group for each directory/subdirectory/file can be accessed only by the approved user/group and per the permissions we gave it:
Linux Permissions “Dos”
1. Linux is a “top-down” environment. This means that if you deny “group” or “other” permissions to a directory, all subdirectories and files within that directory will be denied the permissions established at the directory level. The minimum permission for access to a directory is executed (x).
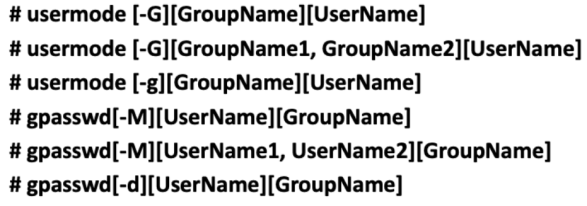
2. Make sure you associate the correct user to the correct group and give the correct permissions to the file/subdirectory/directory using the command usermod and gpasswrd as seen below:
Linux Permissions management- associate the right user with the right group with the right permissions
Usermod command: this is a command-line utility that allows you to modify a user’s login information, in our case we use it to change or add groups to the user.
-g : is changing the primary group of the user
-G : is adding a group to the user
Gpasswd command: This command assigns a user to a group with some security criteria
-M : is to set the list of group members
-d : it is to remove a user from the group.
3. Make sure you are overlapping groups and users.
4. Defined groups are maintained by the root operator
5. When we create a user, it will create a directory for that user. With permissions for that user only. Don’t change the permissions. Home directory can be changed at
Open (using sudo or root) vim /etc/passwd
6. When you are zipping files make sure you use the user needed
7. Creating a file with “owner only Permissions:
chmod 700 test.txt where test.txt is the name of the file(of course user root can read this file).
8. Set a file for read-only: chmod 744 test.txt
Linux Permissions “Dont’s”
1. Don’t use root unless instructed by your manager/IT department!
2. Don’t give your password to anyone. They will be able to edit/delete/change the files in your name.
3. Make sure to give the correct permissions to the correct group. Wrong permissions can create a huge mess.
4. Make sure the correct users are attached to the correct groups, issues with permissions can cause serious problems.
5. Changes with root user cannot be unchanged unless you use root user or a sudo approved user.
Conclusion
To sum it up, Linux security and permission are very important to consider. One small change may open up permissions to your file to anyone! Make sure you check, double-check, and even triple-check your permission prior to publishing an environment and stick to the Linux permissions Do’s and Don’ts we mentioned above to ensure the safety of your code.