CI/CD with Python: From Code to Cloud @ Python Web Conference 2022
JFrog is a proud 2022 Sponsor for the Python Web Conference
July 16, 2022
< 1 min read
CI/CD with Python: From Code to Cloud @ Python Web Conference 2022
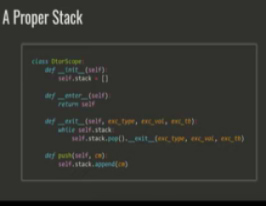
During our session, SuperFrog Daniel Keler, spoke about Python Code to the Cloud. by building a containerized Python Application, passing through security and compliance gates all the way to a Kubernetes cluster using Helm.
#PWC2022 attracted nearly 375 attendees from 36 countries and 21 time zones making it the biggest and best year yet. The highly engaging format featured 90 speakers,
6 tracks (including 80 talks and 4 tutorials) and took place virtually on March 21-25, 2022 on LoudSwarm by Six Feet Up. More information about the conference can be found at: https://2022.pythonwebconf.com