Delivering Shift-Left Security with NeuVector and JFrog Xray

Bringing Kubernetes app security insights to developers
This post is co-authored by Craig Peters of JFrog and Henrik Rosendahl of NeuVector and is also cross-posted on the NeuVector blog.
Kubernetes, the container and orchestration tool favored by enterprises, provides great benefit in automating many aspects of application deployment at scale. But, like any emerging technology, there are perils as well. Administrators are learning that deployments of these new cloud architectures can be as vulnerable to exploits as non-containerized environments.
New technologies present new opportunities for hackers as weak spots are discovered. Cloud-native technologies like Docker and Kubernetes present a larger attack surface, with more potential entry points for malicious crypto mining, ransomware, and data theft. And unfamiliarity with new systems makes it more likely that administration teams will make configuration mistakes, as a recent exploit at Tesla has proved.
Shifting security left for container environments requires a comprehensive end-to-end set of monitors and safeguards to ensure that vulnerabilities are caught and dealt with quickly. A DevSecOps CI/CD pipeline has many technologies, layers, and processes to secure, and as these rapidly evolve, a single tool cannot provide all the needed security.
Fortunately, a broad range of tools are becoming available – but getting them to work together and provide security teams, architects and developers an integrated window into problems can be daunting.
Building Shift Left Security
We’re excited to share that NeuVector and JFrog have been working to bridge this gap. NeuVector is the first container security platform to offer Layer 7 deep network inspection of east/west traffic for real-time protection against network based attacks. NeuVector’s innovative approach to container security, of observing the behavior of executing containers and alerting for anomalies, already works cleanly with Kubernetes deployments that use JFrog Artifactory as their Kubernetes Registry. JFrog Xray works with Artifactory to perform universal analysis of binary software artifacts at any stage of the application lifecycle. Xray helps identify vulnerabilities in images by scanning and analyzing artifacts and their metadata, recursively going through dependencies at any level, before the images are run.
NeuVector 2.0 integrates the artifact scanning results of JFrog Xray with NeuVector’s innovative multi-vector container security platform, for a seamless source of information and action. This will add deep insight into the contents and vulnerabilities of containers through the NeuVector tool.
Integration between NeuVector and JFrog Xray shifts operational security information left into the developer’s hands.
NeuVector integrates the results of the image scanning performed by JFrog Xray into NeuVector’s new auto-response rules– instantly providing security policies and response actions to protect containers and generate alerts. These rules can be customized to match criteria such as specific container vulnerability profiles, or set to address suspicious activity across multiple threat vectors – including the container network, processes, or file system.
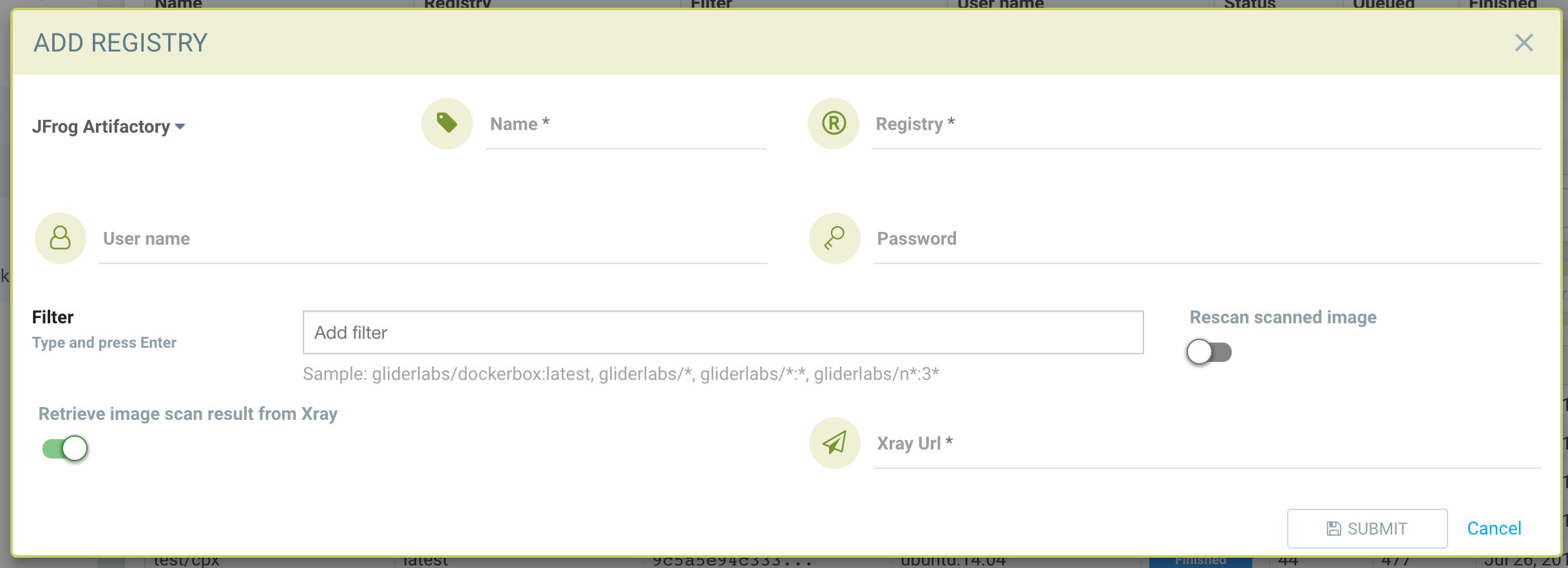
NeuVector 2.0 UI with JFrog Xray data
Further, the NeuVector container security platform grants the ability to specify a range of incident responses using webhooks, and generate custom notifications back to the owner of a compromised container’s image in JFrog Artifactory for the developer to take action.
A later NeuVector release will integrate the behavior alert information from NeuVector into JFrog Xray. In this way, developers choosing which containers to add to their projects as dependencies can be better informed about how appropriately the containers are behaving in operations, and get a view to their vulnerabilities and license data from Xray.
Build, Ship, Run
Let’s see how these integrated features bring security into the entire CI/CD pipeline.
In the Build phase, code and image analysis is critical for removing known vulnerabilities before applications are deployed. In the Ship phase, ensuring appropriate access controls and restricting deployment of images is critical to make sure vulnerabilities are not intentionally or accidentally introduced later in the pipeline. In the Run phase, there is a preparation phase for properly locking down hosts and orchestration tools. And while in production, real-time monitoring of the container environment is critical to catch exploits that are likely to occur.
In this platform environment, JFrog Artifactory and Xray provide the needed security, tools and features for the Build, Ship, and Pre-Deployment phases. NeuVector completes the pipeline by providing the Run phase security that protects against network and host-based exploits with a layer 7 container firewall combined with container inspections and host security.
As customers take more and more advantage of the scaling and operational advantages of Kubernetes, JFrog and NeuVector continue to focus on bringing new kinds of insights to help mitigate the security risks posed by attacks on these emerging technologies.
Learn More
On August 15, 2018, NeuVector & JFrog presented a live webinar that demonstrates the features of NeuVector 2.0 and how the integration with JFrog Xray completes the DevSecOps circle.
View for the webinar
Try JFrog Xray
Try NeuVector



