Your SpringShell (Spring4Shell) Remediation Cookbook Using the JFrog Platform

A new zero-day exploit in the spring-web package called “SpringShell” (nicknamed “Spring4Shell”) was just leaked and is threatening the internet and the community. The JFrog security research team is investigating the exploit and continuously updating our blog post with technical details on the SpringShell (Spring4Shell) vulnerability.
In this technical blog post, we explain how you can use the JFrog platform to detect, block, and remediate the SpringShell vulnerability to protect your organization.
What You Need to Know
As often happens when a zero-day exploit is discovered, the developer community, facing long evening and weekend hours to track it down, has many anxious questions. But users of the JFrog Platform most need to know these two things:
JFrog Products are Unaffected
None of our platform solutions, including Artifactory, Xray, Pipelines, and Distribution, are affected by the SpringShell vulnerability CVE-2022-22965 or Spring Cloud Function CVE-2022-22963.
You might well ask: How could we determine this so quickly and with such certainty? For the same reason that you, a JFrog customer, can for your own software projects – because Artifactory and Xray are a central part of our mission-critical software development lifecycle (SDLC).
Your Weekend is Safe With JFrog
As a JFrog Platform user, you already have the tools you need to quickly remediate against the SpringShell vulnerability – or any other zero-day security issue you have yet to encounter. With your accumulated packages, binaries, images, and metadata under Artifactory’s binary repository management, you already have everything you need to save your weekend.
– DevOps Service Owner, Bendigo and Adelaide Bank
We’ll explain how you can swiftly protect your organization using the JFrog Platform. You’ll learn how to:
- FIND – Use Artifactory’s build-info metadata and Xray’s deep-binary scanning to discover every usage of packages containing the SpringShell vulnerability, including transitive dependencies, across your entire inventory of artifacts and applications in all stages of the SDLC.
- FIX – Once yourJFrog Platform solutions have identified applications using a vulnerable package, developers can update their source code to use the safer, updated version and produce a new build.
- FORTIFY – Use Xray to block any further builds using vulnerable package versions, and any promotion to production release of vulnerable builds already in your pipeline. Or use Artifactory exclude patterns for more limited way to block.
Find all Usage of SpringShell (Spring4Shell) Vulnerable Packages
With JFrog Artifactory to manage all your binaries and JFrog Xray for automated vulnerability scanning of those binaries, you can quickly pinpoint where the SpringShell vulnerability is present in your software supply chain and implement security measures throughout the SDLC.
Depending on which set of JFrog Platform solutions you have installed and use as a regular part of your SDLC, you have these methods available to quickly pinpoint where the SpringShell vulnerability is present in your software supply chain and implement security measures throughout the SDLC.
- Using Artifactory and Xray (Best Method for All Coverage)
- Use Xray reports to trace all SpringBoot packages in Repos/Builds/Release Bundles/Watches
- Use the Xray violations pane to filter vulnerable monitored resources
- Use an Xray watch to alert upon an attempt to download the vulnerable SpringBoot package
- Using Artifactory only (Good Method for Internal Coverage)
- Use the Artifactory search capability to find all repositories and namespaces with SpringBoot library
- Use Artifactory build-info (Software bill of materials – SBOM)
 Using Artifactory and Xray (Best Method for All Coverage)
Using Artifactory and Xray (Best Method for All Coverage)
JFrog Xray’s deep-recursive scanning provides the most comprehensive analysis of your binaries in Artifactory, including transitive dependencies in third-party packages or artifacts such as Uber Jars or base Docker images from a public repository like DockerHub. With Xray, you can be sure to catch every usage of a critically vulnerable package like SpringShell in any or all of your repos, builds, or release bundles.
Xray is included in all JFrog Cloud subscriptions, including free accounts. For self-managed installations on-prem or in the cloud, you can install a free trial of Xray in as little as 5 minutes.
Try Xray
These are the ways you can use Xray:
Use Xray reports to trace all spring-web artifacts in Repos, Builds & Release Bundles
Assumptions:
- Artifactory with Xray is installed
- The required scope of artifacts are indexed (make sure to “reindex” so that already existing binaries will be scanned):
- Repositories – Relevant repositories are indexed
- Builds – CI systems are integrated with Artifactory and upload “Build-info” for builds.
- Release bundles – Release bundles are used to distribute binaries to production.
Steps:
1. Go to Security and compliance > Reports
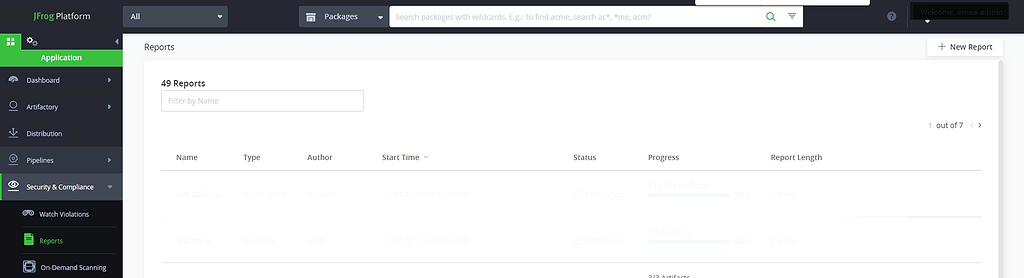
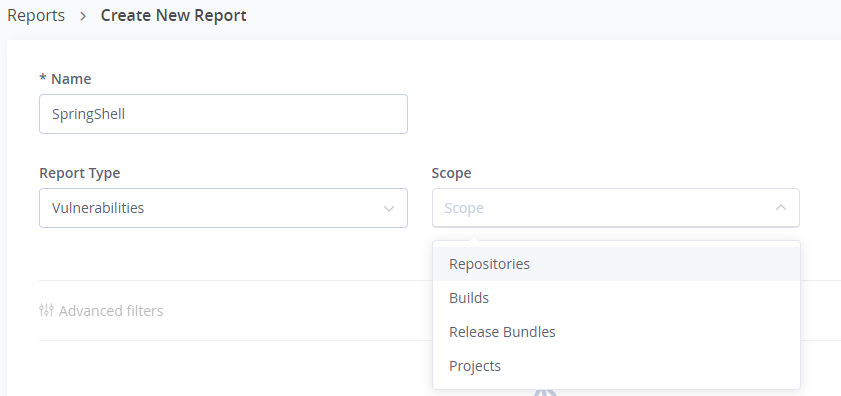
2. Create new report with the scope you would like to discover
3. After selecting the concerned resources, add CVE-2022-22965 as the criteria
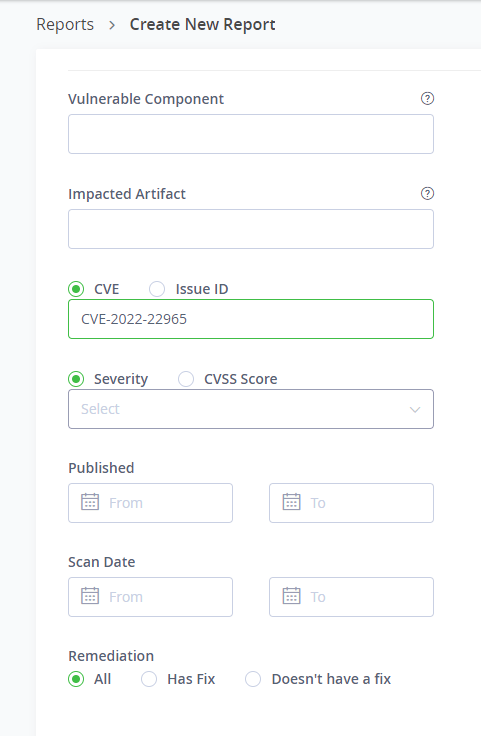
These criteria will help to generate a report in various formats, such as the following example:
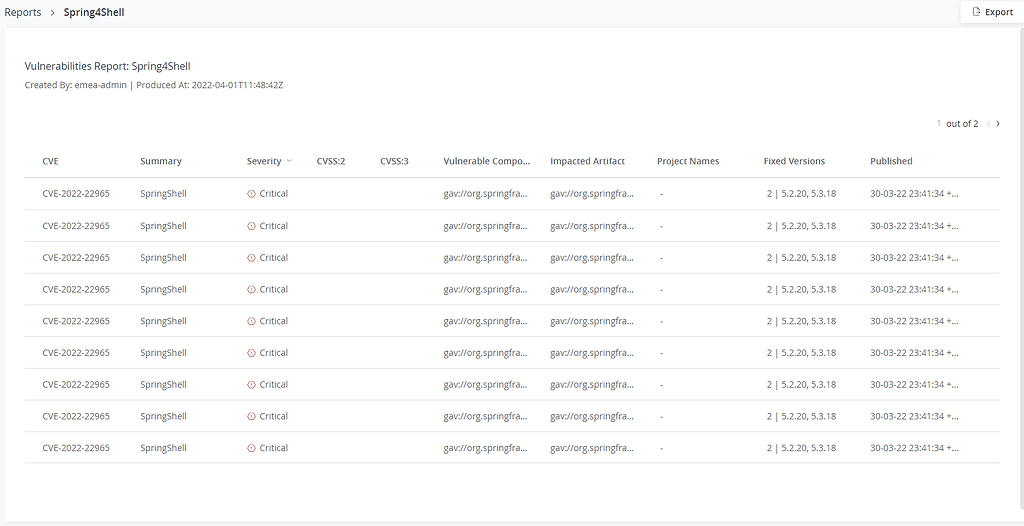
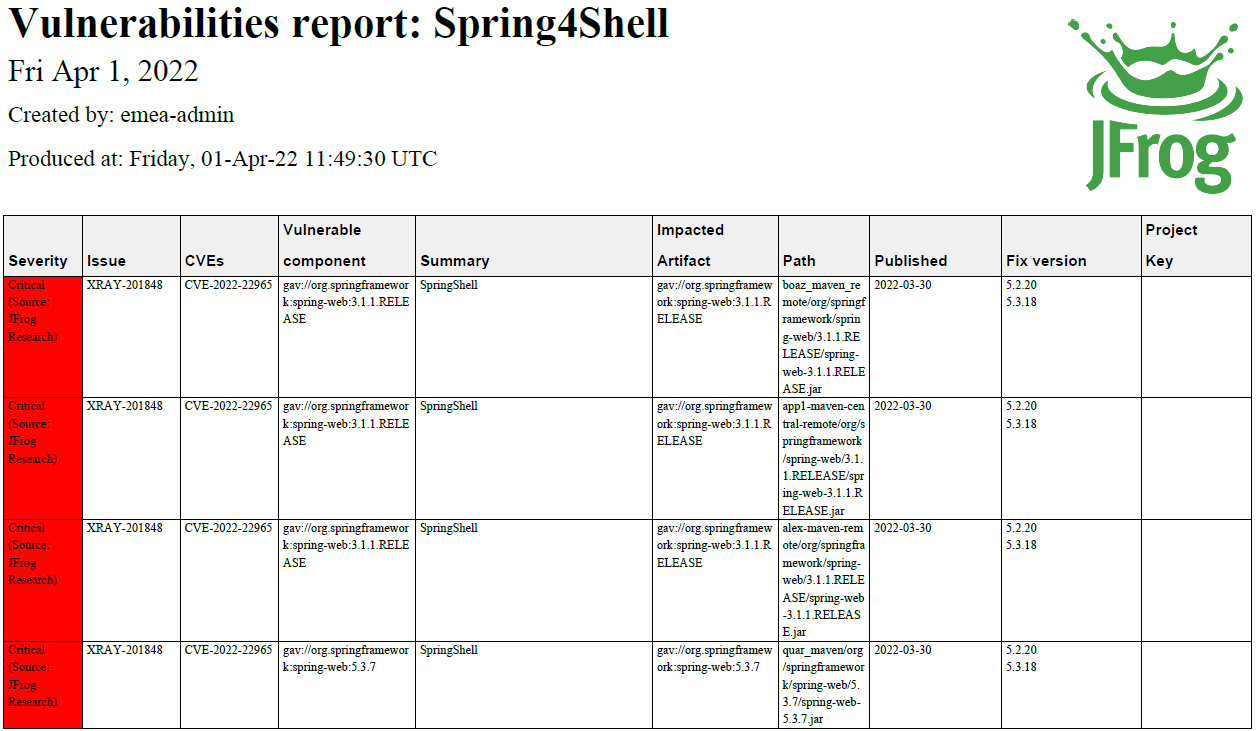
You can later export to PDF / CSV / JSON formats:
Use the Xray violations pane to filter vulnerable monitored resources
Assumptions:
- Artifactory with Xray is installed
- Watch is monitoring the resources you would like to filter, and the CVE-2022-22965 triggered a violation
Steps:
1. Go to an already existing watch and click on the “filters” icon.
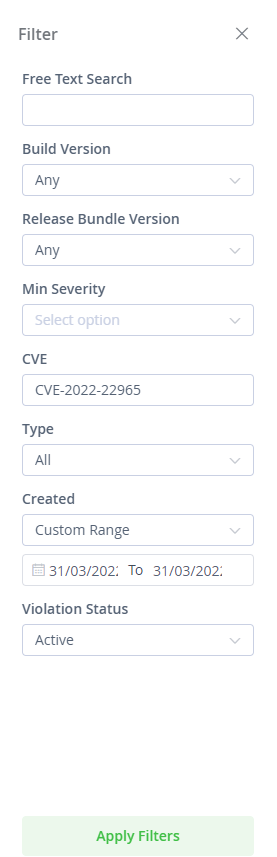
2. Filter on the specific CVE-2022-22965, with the relevant settings such as custom timeframe, Any Build, and Any Release Bundle
Using an Xray watch to alert upon an attempt to download vulnerable spring-web artifact
Using Xray policies and watches, you can alert (and block) upon an attempt to download the vulnerable spring-web artifact. We recommend that upon a violation a webhook would alert to a dedicated channel (such as Slack) to your security team
Assumptions:
- Artifactory with Xray is installed
- Relevant Maven and Gradle repositories are flagged with “Xray index” enabled.
Steps:
1. Create an Xray policy that defines a violation with a criteria of minimal severity “Critical.”
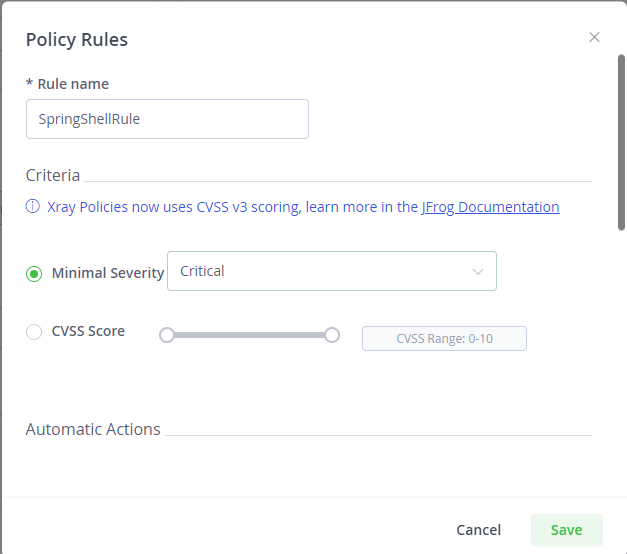
2. Create a watch associated with the policy above
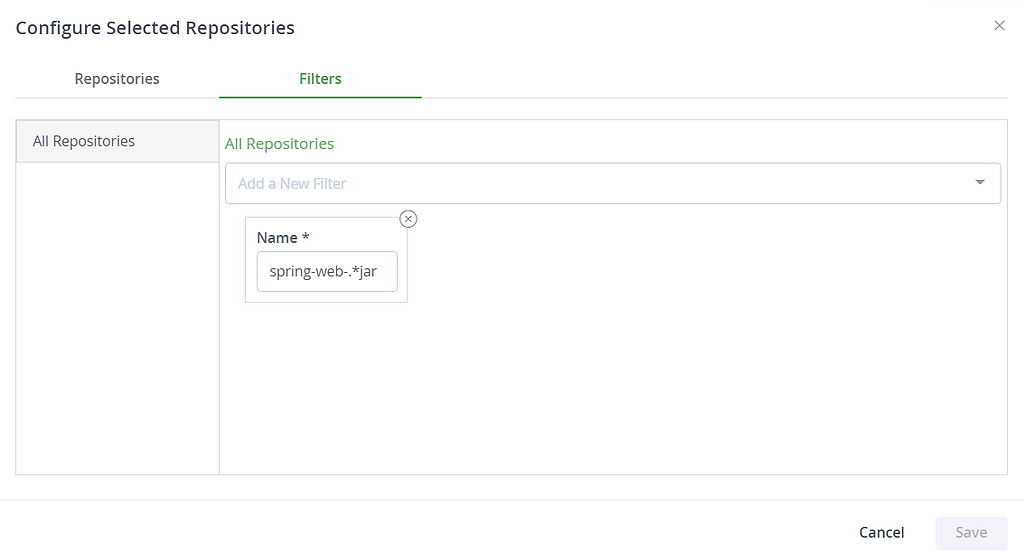
3. Apply it to “all repositories” with a filter to include only spring-web artifact names (spring-web-.*jar).
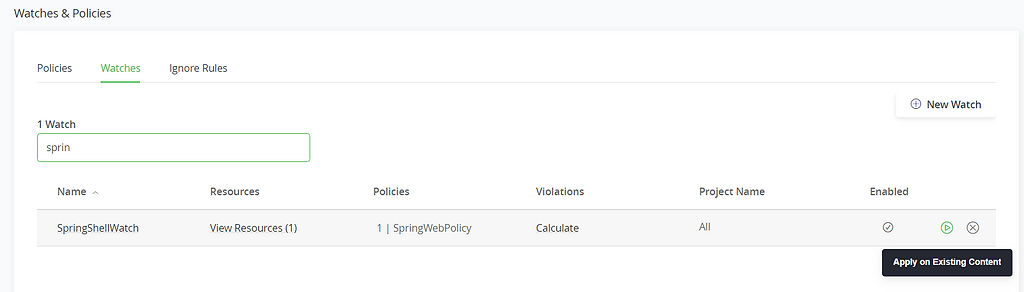
4. Run the “Apply on existing content” with the relevant time frame on the new watch to trigger violations on spring-web.
 Using Artifactory Only (Good Method for Internal Coverage)
Using Artifactory Only (Good Method for Internal Coverage)
To produce a Software Bill of Materials (SBOM) for your applications, we hope you have been publishing build-info metadata through the JFrog CLI or in your Pipelines CI/CD automation. This is one of the most essential best DevOps practices enabled by the JFrog Platform, making all of your builds fully traceable to all of their component sources.
Armed with this data about your binaries, you can search all your builds for the vulnerable SpringShell package.With Artifactory’s rich search capabilities, you can also narrow your search to target the most immediately relevant builds, enabling you to focus your efforts and zero in on what needs your urgent attention.
However, this benefit accrues only to the builds you make through your CI. So using build-info in Artifactory alone will not cover situations when SpringShell is already packed into another package/artifact like Uber Jars, a base docker image, etc. Only Xray can scan these third-party binaries and provide you complete coverage, as well as continuously monitor for download and use of this vulnerable artifact in future.
Use Artifactory search to find all ‘spring-web’ artifacts and all the related builds
You can search across all of your Artifactory repositories to discover where packages, artifacts, and builds are used.
Assumptions:
- Artifactory is installed
Steps:
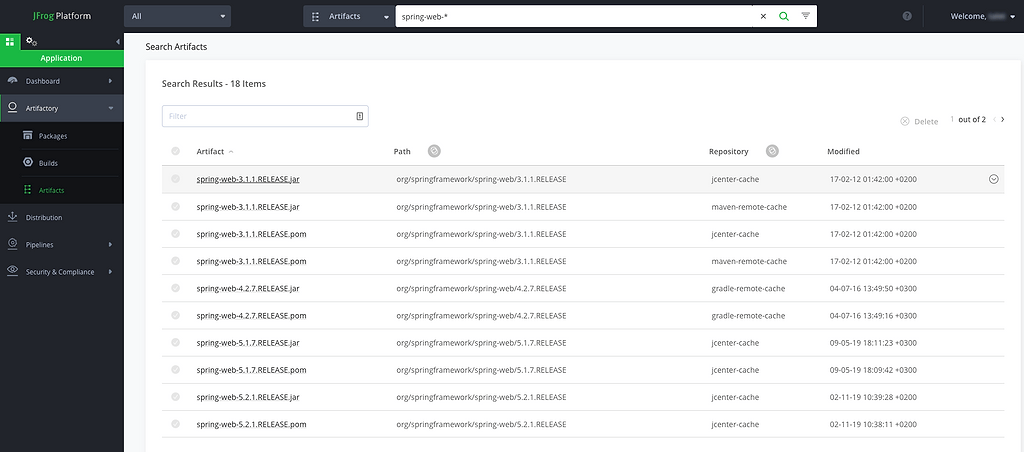
Use the search bar in Artifactory to lookup the spring-web artifacts that are cached in Artifactory remote repositories, as well as their locations in local repositories.
Use Artifactory build-info (Software bill of materials – SBOM)
JFrog artifactory CLI and CI plugins can store build-info, the metadata associated with a build from Artifactory. When you follow the JFrog best practice and store build info in your Artifactory instance, you can search Artifactory repositories to list all the builds that use the spring-web library as a dependency.
Assumptions:
- Artifactory is installed
- CI server is integrated with Artifactory and it publish build-info
Steps (through the JFrog Platform UI):
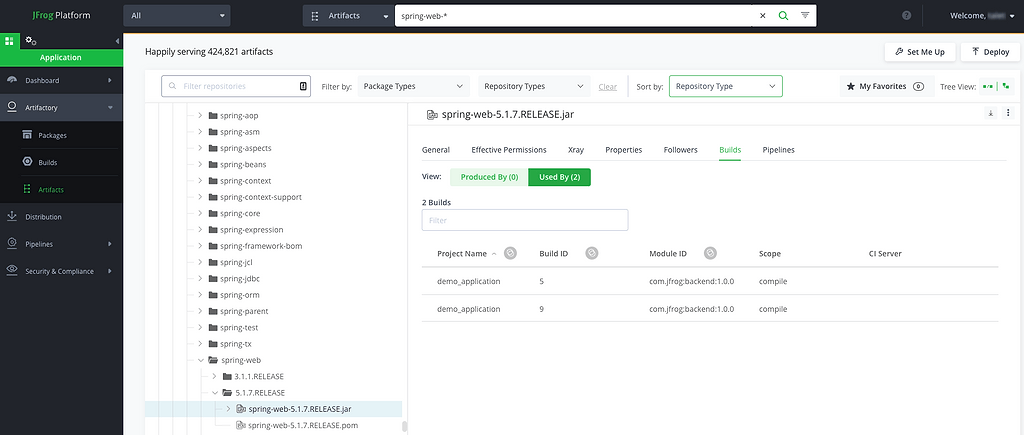
1. Follow the previous section of “Use Artifactory search to find all repositories and namespaces with spring-web library”
2. For each vulnerable version of the spring-web artifact, examine the “used by” tab.
Steps (through the Artifactory REST API):
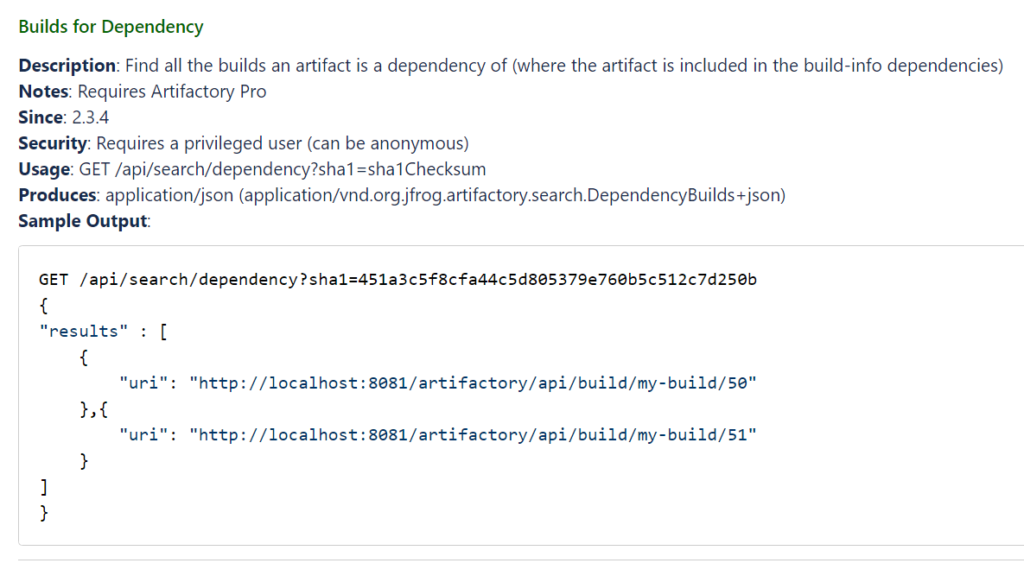
Another method is to use the Artifactory API to search a checksum in builds (each spring-web artifact has a different checksum):
Fix Your Builds
Once you know which of your artifacts, builds, and release bundles are vulnerable, your development teams can update their source code and produce new, remediated builds and release bundles.
Spring has posted a Spring Framework RCE response, and continues to update it with fresh information as it becomes available, including fixes and workarounds.
The JFrog Security Research team is also investigating, and has provided a technical explanation of SpringShell. We will update with suggested remediations and mitigations as our investigations continue.
Fortify to Block Use of Vulnerable spring-web Artifact
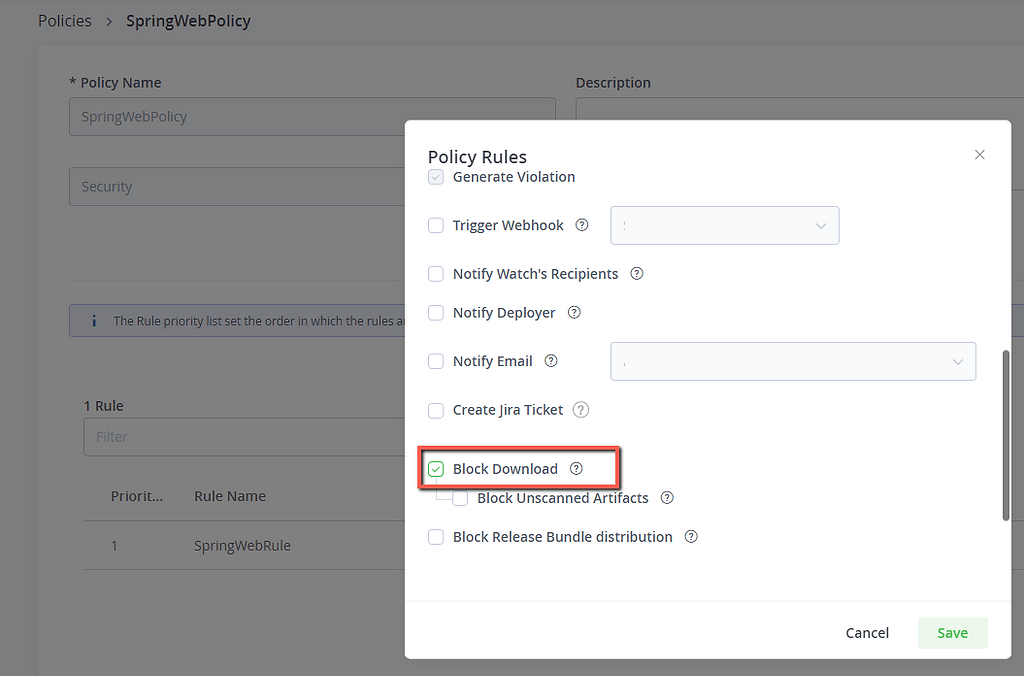
 Use Xray policy to block attempts to download of the vulnerable artifact
Use Xray policy to block attempts to download of the vulnerable artifact
Using Xray policies and watches, you can alert (and block) upon an attempt to download a vulnerable spring-web artifact.
Assumptions:
- Artifactory with Xray is installed
- Relevant local and remote Maven and Gradle repositories are flagged with “Xray index” enabled.
Steps:
Same as “Using Xray watch to alert upon an attempt to download vulnerable spring-web artifacts”, with “Block download” flag set
 Configure Artifactory exclude patterns on remote repositories
Configure Artifactory exclude patterns on remote repositories
Assumptions:
- Artifactory is installed
- Note: This is considered a partial coverage since you can find association to this package, but it will not cover situations when the package is already packed into another package/artifact like Uber Jars, base docker image, etc.. Only Xray can scan binaries and provide you complete coverage, including continuous monitoring if one of the developers will upload or use this artifact in the near future.
Steps:
Configure an exclude rule to select against the library’s `*jar` file, to prevent it from being resolved by Maven and Gradle repositories. (For more information, see this blog post.)
This will result in developers being unable to access the base jar for their dependency resolution and is a good way to prevent the affected code from being used.
Something for Everyone
As you can see, thousands of customers of the JFrog Platform, whether in the cloud or on-prem, have the ready means to find, fix, and fortify their entire software supply chain from the SpringShell vulnerability in only hours. The best practices of DevSecOps through rich binaries management, SBOMs, and SCA enabled by Artifactory and Xray are helping many to save their weekends and holidays.
Not using the JFrog Platform? Well,…you may have to reconsider your weekend plans.
But not so fast, we’re still here to help! The JFrog Security Research Team has just published an open source scan_spring tool that can be used to scan any compiled code (not just in Artifactory) and verify whether Spring endpoints that make the vulnerability exploitable exist in the codebase.