Access Service
JFrog Artifactory offers a variety of means for authentication and authorization, from LDAP and Active Directory, to OAuth and SAML SSO. Once a user is authenticated with Artifactory, Teams and Permissions provide a flexible way to exercise fine-grained access control. However, all of these capabilities are only applicable to Artifactory users, and then, authentication and authorization must be configured for every Artifactory instance which you want the user to access. The Access Service extends Artifactory’s security model providing a flexible means of authentication with a range of advanced capabilities through Access Tokens.
“Access” runs as a separate service under the same Tomcat webserver as Artifactory communicating with it via HTTP. This separation is a step towards breaking Artifactory down into set of smaller services. Using access tokens for authentication opens up several unique capabilities when using Artifactory.
Cross-instance authentication
Access tokens introduce the concept of a “circle of trust”; a set of Artifactory instances that allow a user to be authenticated using the same access token. This means that you only have to manage users on one instance in your circle of trust, and by providing them with an access token, you can give them access to any other instance within the circle.
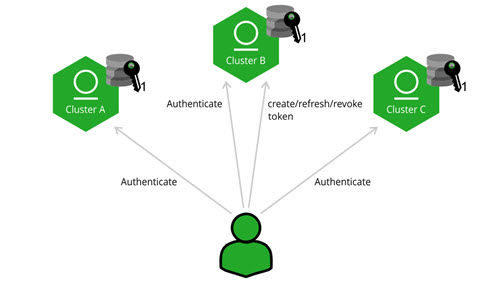
User and non-user authentication
With access tokens, you can provide access to entities that are not human users. For example, you can provide an access token to a CI server that needs to access Artifactory to resolve dependencies and upload builds.
Time-based access control
Access tokens are “expire-able” so you can control the period of time for which you grant access. However, you may also delegate that control to the receiving user by making them refreshable. Effectively, you can provide a user with an access token and then forget about it, letting the user refresh the token before it expires. Naturally, as the issuer of a token, you retain full control and are able to revoke tokens as needed.
Flexible scope
By assigning Groups to tokens, you can limit those tokens to the same access privileges exposed to those groups.
Currently, the Access service only manages access tokens, however, going forward, it will also manage all aspects of user and permission management.



